Table of contents
- How an evil twin attack works: step-by-step
- Step 1: Choose a location with free Wi-Fi
- Step 2: Set up a Wi-Fi access point
- Step 3: Create a fake portal page
- Step 4: Stay close to potential victims
- Step 5: Monitor & steal data
- How to protect yourself from an evil twin attack
- Avoid unsecured Wi-Fi networks
- Use your own hotspot
- Use a VPN
- Turn off autosaves for Wi-Fi networks
- Don’t log into private accounts on public Wi-Fi
- Only use secure websites
- Use two-factor verification
- Why are evil twin attacks so dangerous?
- What to do if you have been hacked with an evil twin attack
How an evil twin attack works: step-by-step
Evil twin cyber attacks work by getting someone to believe that they are connecting to a legitimate public Wi-Fi network. To make their attack believable, hackers generally follow these steps:
Step 1: Choose a location with free Wi-Fi
First, they need a busy location that already offers free Wi-Fi, like an airport or cafe. Generally, they look for a place that has multiple access points to make it easier for their network to go unnoticed.
Step 2: Set up a Wi-Fi access point
Next, the hacker will set up a new hotspot that uses the same Service Set Identifier (SSID) as the free, public Wi-Fi network. This makes it almost impossible for connected devices to tell if they are on a fake or legitimate connection.
This setup can be done from almost any device too–phones, laptops, tablets, portable routers. Sometimes, hackers will even use a Wi-Fi Pineapple to allow for a broader range.
Step 3: Create a fake portal page
If you’ve used public Wi-Fi, you’re likely familiar with the sign-in or optin pages that public Wi-Fi networks have. To make their network look more legit, evil twin hackers will often create a fake portal page where users have to log in to use their network.
This creates an opportunity for hackers to collect your passwords and other log in information that you may use on a regular basis. And, if the hackers know what they are doing, they can create a login page that is identical to the legitimate network’s portal page, making it impossible to tell the difference between the fake and real versions.
Step 4: Stay close to potential victims
As people use their devices in public spaces, they generally want Wi-Fi connections with stronger signals. Hackers will use this to their advantage by setting up their devices closer to potential victims. The closer they are, the stronger their Wi-Fi signal will be. Some devices even default to connect to stronger connections automatically.
Step 5: Monitor & steal data
Once a user connects to the evil twin network, the hacker can monitor their activity and steal information that gets entered into log-ins, order forms, and more. If you log into your bank account or enter your credit card information on an online store website, the hacker can see this information and steal it.
Evil twin attacks, phishing scams, spyware—there are countless ways bad actors can monitor your online activity. That's where Clario Anti Spy comes in. This anti-spyware utility features an Anti-spy setup that helps you quickly implement the best practices for staying safe online. It also includes a Data breach monitor that alerts you if your email account has been compromised.
Here's how to run the Data breach monitor in Clario Anti Spy:
- Download Clario Anti Spy and subscribe to create an account.
- Tap Scan under Data breach monitor.
- Wait for the app to scan your primary email account. If it detects breaches, update your passwords immediately, starting with your most important accounts.
- Enter a different email address to scan additional accounts if needed.
- If you need assistance, tap the Messages icon at the bottom of the screen to connect with a security expert.
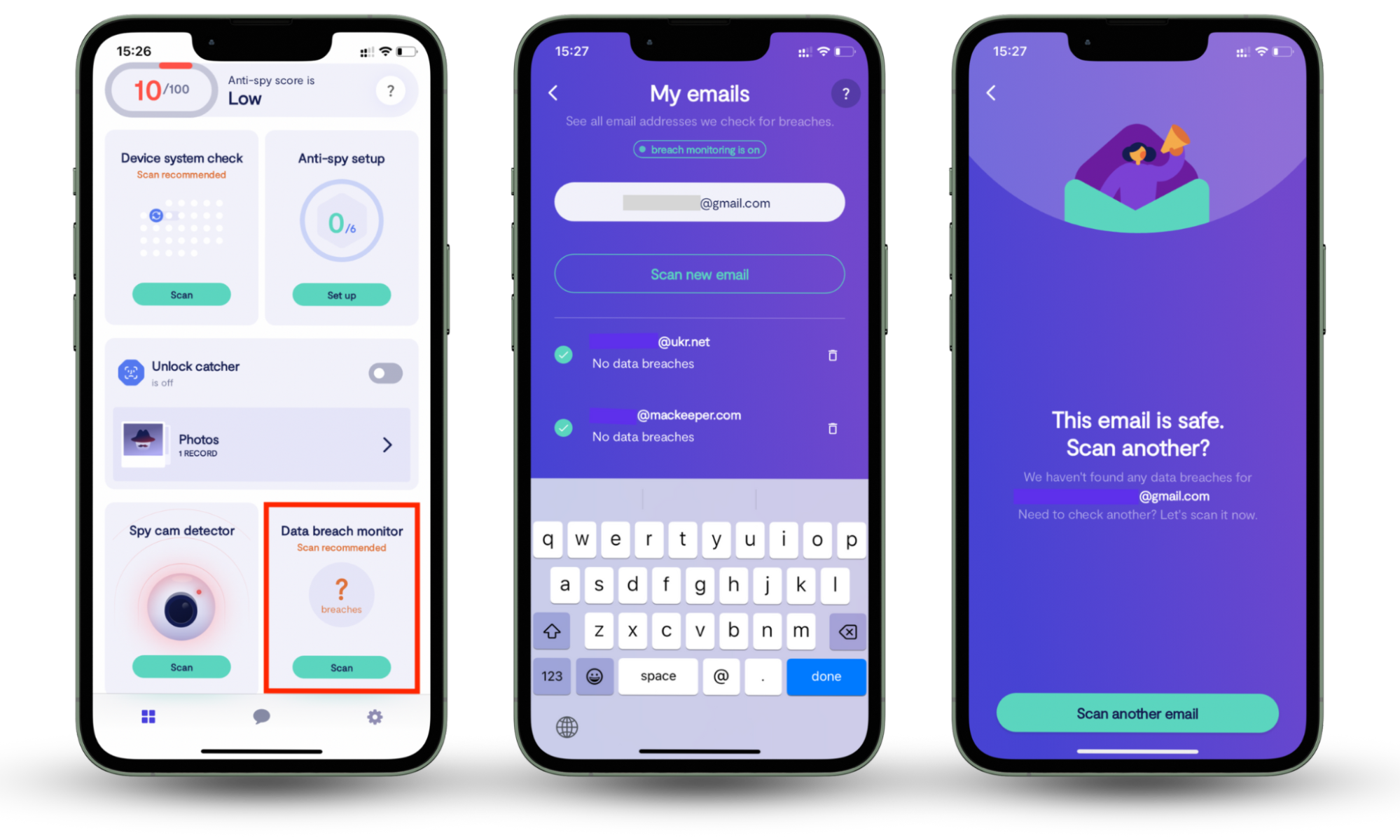
Clario Anti Spy also offers additional features to enhance your security. For instance, it includes a Device system check to detect jailbreaks and rooting and an Unlock catcher to monitor device tampering. On Android, you can run a Spyware scan to identify malicious apps and use Virtual location to hide your real location.
How to protect yourself from an evil twin attack
As we’ve seen, evil twin attacks can be almost impossible to identify, but here are several steps you can take to protect yourself from hackers.
Avoid unsecured Wi-Fi networks
If you are going to use a free Wi-Fi network, make sure it is secured. Evil twin networks are almost always unsecured. There should be a designation next to each available Wi-Fi network that indicates whether it is secure or not. Secure networks usually involve asking an employee or manager for the Wi-Fi password.
Use your own hotspot
One of the safest ways to go online in public spaces is to avoid public networks altogether and use your own hotspot or data. Ensure you have a password on your hotspot so others can’t access it.
Use a VPN
A VPN encrypts your data before the hacker is able to see it. When you enter private information on any Wi-Fi network while using a VPN, your data gets encrypted to prevent those who may be monitoring the network from seeing your information. You’re all set for seamless and private browsing.
Turn off autosaves for Wi-Fi networks
Don’t let your device save public Wi-Fi networks for automated connections.If your device is set up to connect automatically to previous Wi-Fi networks, you open yourself up to evil twin attacks. Disable this feature to be more mindful of the networks you connect with.
Don’t log into private accounts on public Wi-Fi
When using public Wi-Fi, don’t log into private accounts. Logging into these accounts while on an evil twin network allows hackers to access your passwords.
Only use secure websites
It's just good cybersecurity etiquette to use websites that are marked as secure. This is indicated by the lock icon in the search bar next to the URL of the website. If the website has https in the URL, that also means it is secure.
Use two-factor verification
Even if a hacker gains access to your passwords, with two-factor verification on your accounts, it makes them much more difficult to access. 2FA can also protect your accounts against other forms of threats, such as brute force attacks and zero-day attacks.
Why are evil twin attacks so dangerous?
Evil twin attacks are dangerous for a few reasons:
- It is often impossible to tell the difference between a legit network and an evil twin network.
- They allow hackers to access your device, meaning they can access login credentials and other private data like social security and financial information.
- Hackers have the opportunity to insert malware on your device.
- You only realize you’ve been a victim of an attack after the hacker has performed unauthorized transactions or inserted malware.
What to do if you have been hacked with an evil twin attack
If you’ve fallen victim to an evil twin attack and have suffered a data breach or financial loss, contact your bank or credit card company immediately to investigate and cancel any pending transactions. Depending on the features of your bank account, you may be able to seek reimbursements for financial loss.
Also, be sure to change your passwords on your private accounts. If the attack is more severe in nature, you may also involve your local police department and submit a complaint to the FCC Consumer Complaint Center.
Evil twin attacks aren’t the only method that cyber hackers use to steal sensitive information online. To keep your mobile devices safe, install Clario Anti Spy—it monitors for data breaches, helps you fix security vulnerabilities, and keeps spyware at bay.


