Table of contents
- Brute Force Attack Definition
- Types & methods of brute force attacks
- Simple brute force attacks
- Dictionary attacks
- Hybrid brute force attacks
- Reverse brute force attacks
- Credential stuffing
- Brute force attack prevention
- Use a strong, unique passwords
- Enable two-factor authentication
- Use a password manager
- Be aware of phishing scams
- Avoid connecting to unsafe Wi-Fi
- Monitor your personal info for breaches
- Keep yourself safe from brute force attacks
Brute Force Attack Definition
A brute force attack is a type of cyberattack wherein a hacker uses an automated program to guess the password or personal identification number (PIN) of a victim's account. Hackers often use this method when they have obtained a list of usernames or email addresses but don't have the corresponding passwords.
Types & methods of brute force attacks
When it comes to brute force attacks, hackers employ several methods to access your accounts. In addition, brute force attacks aren’t just used to crack passwords. They can also be used to discover hidden pages and content on websites (i.e. directories and files that have not been linked to from the main website).
While previously, hackers would need to guess your passwords manually, these days brute force attacks are automated. This means that hackers can try thousands–or even millions–of log-in combinations until they find the right one.
Here are some types and methods of brute force attacks:
- Simple brute force attacks
- Dictionary attacks
- Hybrid brute force attacks
- Reverse brute force attacks
- Credential stuffing
Simple brute force attacks
A simple brute force attack is a trial-and-error method used by hackers to obtain information such as a user password or personal identification number (PIN). Oftentimes, simple brute force attacks work by targeting a specific login page and then trying to guess the username and password using lists of common passwords.
Dictionary attacks
A dictionary brute force attack is one of the most common types of brute force attacks involving a list of common words to guess a password. While this might sound like an easy task for a hacker, it can actually be quite difficult. Unlike before, most sites now have measures in place to prevent these kinds of attacks, such as requiring a minimum number of characters or banning common words.
Hybrid brute force attacks
Through a hybrid brute force attack, hackers combine a simple brute force attack with a dictionary attack by trying various combinations of passwords with the most commonly used words in mind. By combining these two methods, the hacker has a much higher chance of success.
Reverse brute force attacks
A reverse brute force attack is when an attacker takes a list of common passwords and tries them all against a single account. The goal is to eventually find the correct password for that account. This type of attack can be very successful if the attacker has a large list of common passwords.
Credential stuffing
Credential stuffing is a type of brute force attack where hackers use lists of stolen usernames and passwords to gain access to your accounts. These lists are usually obtained through data breaches at other companies. Hackers will use automated tools to try these stolen credentials on your accounts until they find a match.
Brute force attack prevention
While it can be impossible to eliminate the risk of brute force attacks completely, there are ways you can prevent brute force attacks from working effectively.
Here are some ways how to prevent brute force attacks:
- Use a strong, unique password for each of your online accounts
- Enable two-factor authentication
- Use a password manager
- Be aware of phishing scams
- Monitor your personal info for breaches
Use a strong, unique passwords
When it comes to keeping yourself safe online, a tried-and-tested internet safety rule is to make an effort to create strong, unique passwords. To create a strong password, it’s best to use a combination of letters, numbers, and symbols.
In addition, it’s also recommended to avoid using common words, repeating the same password across multiple accounts, or sharing your passwords with other people. These days, many websites have tools to help determine whether a password is weak or strong. So, it’s best to try different combinations until you find one that fits the bill.
Enable two-factor authentication
Through two-factor authentication (2FA), you can include an additional layer of protection in the event of a hack. There are several types of two-factor authentication, which include one-time pin codes to be sent to your email or mobile number and authentication apps.
With two-factor authentication enabled, you can be sure that even if a hacker can crack your password, they will not have automatic permission to access your account. Aside from email addresses, you should also make sure that all accounts which allow for 2FA are enabled, including social media accounts.
Use a password manager
After creating a strong password, the next challenge is to remember it. Because strong passwords often mean a combination of difficult to remember strings of letters and numbers, it can be a hassle to keep all of them in check.
Using a password manager, you can make sure that your passwords are always within reach. With this, you’ll be incentivized to keep creating strong passwords without having to memorize all of them.
Be aware of phishing scams
Aside from creating and keeping strong passwords, the next thing you should do is to make sure they stay safe. Unfortunately, the internet is rife with phishing scams, wherein hackers try to get your exact password directly from you.
In some cases, hackers create convincing emails, landing pages, and apps, which they use to confuse unsuspecting users. By accidentally filling up these copies, you can serve your passwords on a plate to hackers. To prevent this, make sure that you always check if you’re on the right website, or you’ve downloaded the right app before logging into your account.
Avoid connecting to unsafe Wi-Fi
One of the most common ways wherein hackers access your data is through unsafe public or home Wi-Fi. Using unsafe internet connections, hackers can gather a wealth of information, which can help their automated bots guess your passwords more effectively.
For example, having access to your device through public Wi-Fi helps hackers identify what websites or apps you normally use. It also helps them learn things like your full name, mobile number, pet names, and other information. Thankfully, there are many things you can do to make your home Wi-Fi more secure.
Monitor your personal info for breaches
While you can be as careful as possible, there is always a chance that a company that you’ve trusted with your data exposes it. As more aspects of our lives go online, data breaches are only going to become more common.
To prevent any issues from leaked personal information, it’s best to monitor your email addresses for any breaches or invest in apps which can do them for you. This is where Clario comes in — check your emails for data breaches and take action as soon as possible to protect your digital privacy.
Keep yourself safe from brute force attacks
Unfortunately, brute force attacks are becoming more common as lists of stolen log-in credentials are readily available on the dark web. With technology becoming more advanced, the programs which enable hackers to perform brute force attacks also become more sophisticated.
Knowing all this, it makes sense to not only be mindful of how brute force attacks work but also know the different ways you can prevent it from happening. Aside from this, it also makes sense to invest in more advanced technology for your peace of mind.
With Clario, you can be sure to have true digital protection on the go. You can sleep better at night knowing that all your important log-in credentials are safe from hackers of every kind. Using Clario’s ID theft protection and breach monitor features, you can have 24/7 data breach monitoring, which lets you know when your data has been compromised.
Clario’s data breach monitor checks for leaks such as credit card details, SSN numbers, and passwords. This way you’ll be able to quickly restore your digital privacy before any damage is done.
Here’s how to use Clario’s data breach monitor:
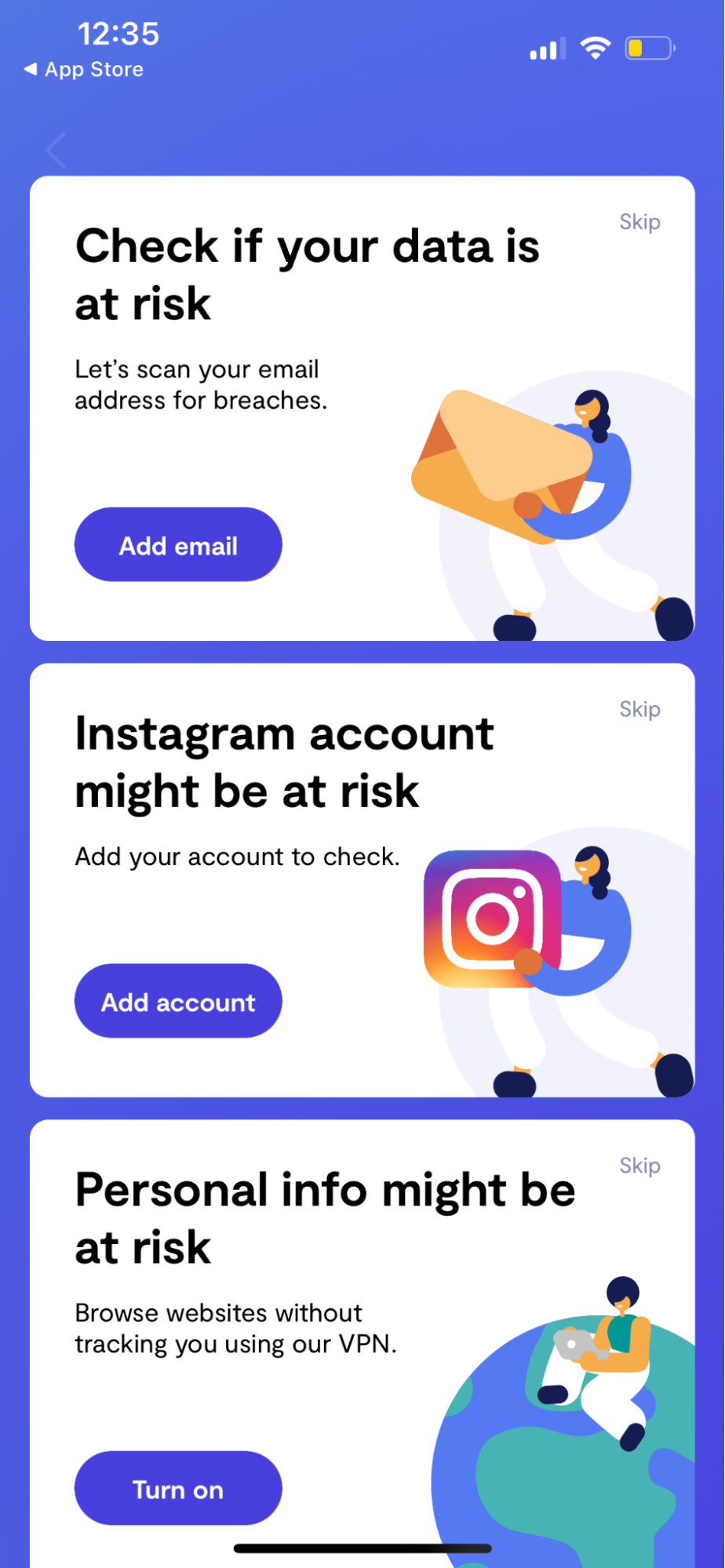
- Open the Clario app on your device.
- Tap Identity.
- Under Check if your data is at risk, tap Add email.
4. On the space provided, type the email address you want Clario to monitor.
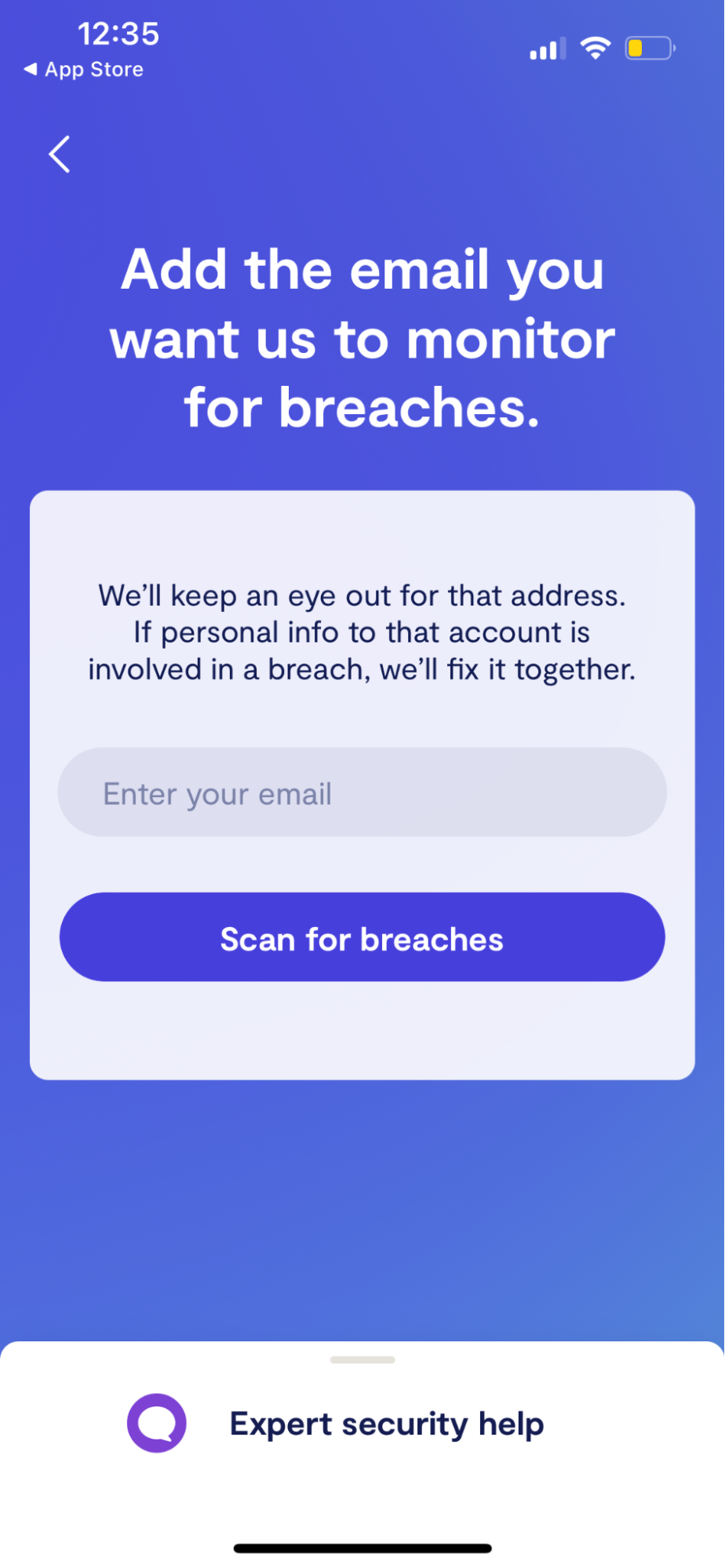
5. Select Scan for breaches.
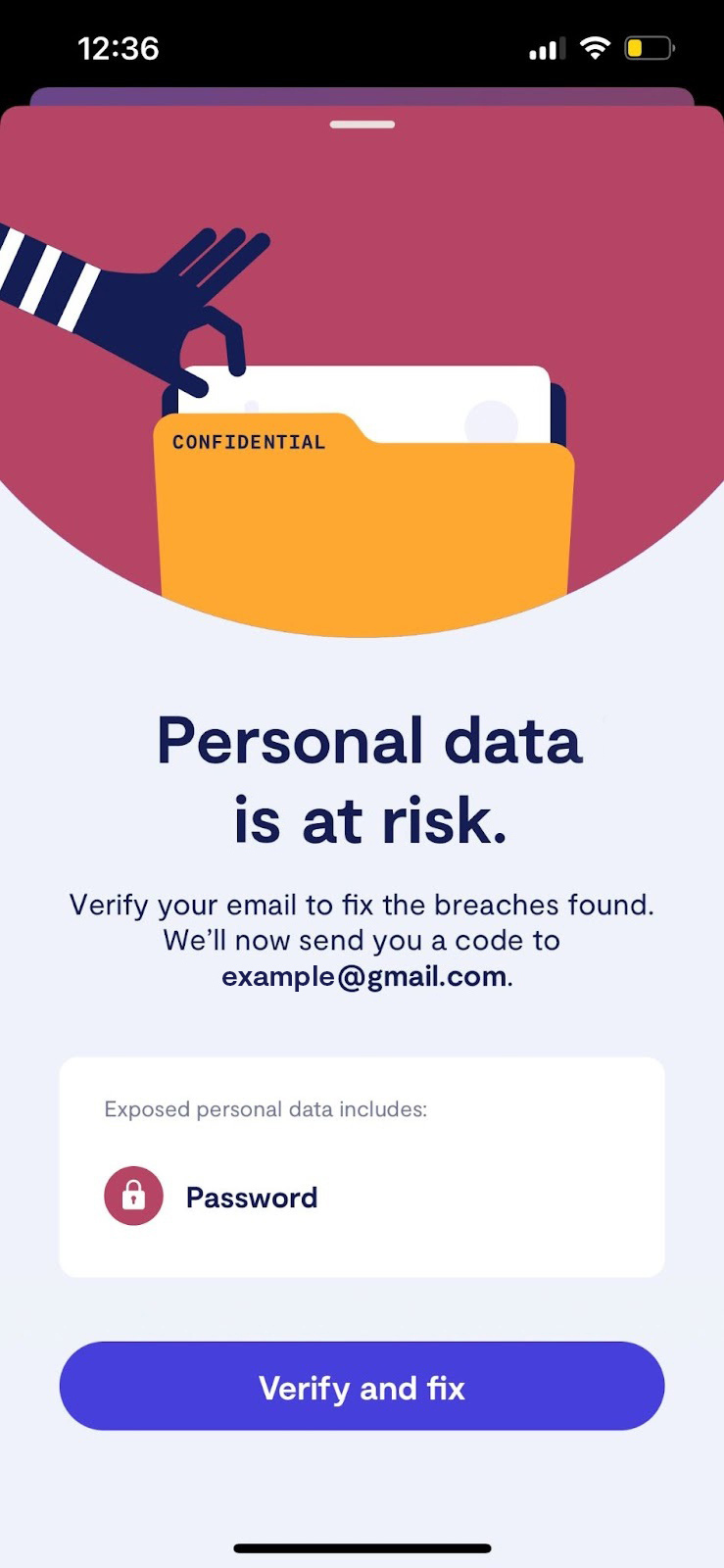
6. Hit Verify and fix and follow the instructions.
Afterward, Clario will do the hard work of monitoring your accounts and let you know as soon as it finds any leaks which may affect your safety online.