Table of contents
- What is Cracking?
- Hacking vs. Cracking
- Types of Cracking
- Password Cracking
- Software cracking
- Network Cracking
- How to Prevent Cracking?
- Protect Yourself From Cracking Today
What is Cracking?
Cracking is a technique that is used to break into computer software, systems, or networks with malicious intent. In the same way that a bank robber might crack a safe, a “cracker” breaks into a digital device or program.
Hacking vs. Cracking
To understand the difference between hacking and cracking, you have to know what hacking is in the first place.
Hacking is the act of compromising digital devices to gain unauthorized access. Although the media commonly uses the term “hacking” to refer to illegal activities, people in the hacking community generally consider themselves the good guys, while crackers are the bad guys.
This is because, in the hacking community, the goal of hacking is to improve or alter security systems and programs.
There is an often quoted line in the community:
For example, many companies hire white hat hackers to check their security systems and make them as hack-proof as possible.
Cracking, on the other hand, is any kind of hacking that’s done for personal gain or other malicious reasons.
Crackers, also referred to as black hat hackers, might take control over a system to destroy or steal information for profit, attempt to scam people, or just cause damage for the sake of it.
The bottom line
Hacking and cracking are functionally the same, but hackers maintain that their work is to find holes in security systems that can then be fixed. Whereas with cracking, the intent is purely malicious.
Types of Cracking
There are several types of cracking, and crackers employ many different techniques to break into computer systems and software. However, the three most common forms of cracking are password cracking, software cracking, and web cracking.
Password Cracking
Password cracking is the act of stealing people’s passwords from databases. But this is often more difficult than it sounds since most websites and services now encrypt their password databases using a one-way process called hashing.
Hashing cannot be reversed, so the cracker needs to:
- Find and obtain the website’s hashes and the algorithms and processes used to create them (also known as the hash function).
- Generate a password, apply the hash function, and see if it grants authentication.
Because this process would be so time-consuming if done manually, crackers employ powerful software to automate the guesswork. The two most common methods of cracking a password are:
- Brute-forcing. Brute-force cracking involves pumping out a massive amount of guessed characters until it gets a match to the hash algorithm. This also includes a dictionary attack which involves guessing the actual words used in the password.
- Rainbow table cracking. A rainbow table is a table of precomputed hash chains. This helps crackers overcome difficulties in large password sets where brute-forcing is infeasible. Using the table, crackers use programs to try and determine a website's hash function.
Software cracking
Software cracking involves changing a program or piece of software. Usually, software cracking is done to remove paid software requirements or pop-up purchase reminders so that people can access the software for free.
“Cracked” software is a paid program that has had its copy protections removed.
Some software cracking techniques include:
- Key generators. Also known as a keygen, key generators are programs that generate valid serial numbers for a piece of software. These serial number keys can then be used to trick the software into thinking you purchased a legitimate copy of the program.
- Patches. Patches are pieces of code that are added to software to change its functionality. If you’ve ever played a game, these are the small updates that remove bugs and glitches. In terms of software cracking, patches are used to remove unwanted features (like pop-up reminders) or add features.
- Loaders. Also known as a crack intro or cracktro, a loader is used to block or modify the start-up process of a program. For example, a loader might bypass copy protections or enable cheating in an online game.
Network Cracking
Network cracking is the act of infiltrating a local area network (LAN). Sometimes referred to as web cracking or wired equivalent privacy (WEP) cracking, this usually involves accessing poorly secure networks.
To illustrate how network cracks work, consider your home Wi-Fi system and all of the devices connected to it. These devices make up a wireless LAN that crackers can target.
Wireless networks are favorable since a cracker doesn’t need a physical connection (like they would with a wired network).
If your Wi-Fi network has no password protection, anyone could stand in its range and connect. But if it is password-protected, they will need to employ password cracking techniques to gain access.
Once they have access, they can infiltrate any of your connected devices (known as computer cracking) and monitor your web traffic. With this ability, they can steal your data, access your accounts, or try to impersonate you.
How to Prevent Cracking?
There are several steps you can take to protect yourself from cracking. While these don’t guarantee that you won’t be targeted, they will dramatically reduce the risk.
- Use unique, strong passwords. If a cracker or scammer gains access to one of your passwords, they could use it to gain access to any other account that you’ve used it on. Using unique passwords helps to reduce the damage that malicious actors can do.
- Avoid public Wi-Fi. Crackers frequent places with free, unsecured wireless networks as they make it easy to gain access to people’s devices. If you are going to use public Wi-Fi, make sure that you also use a VPN to protect yourself.
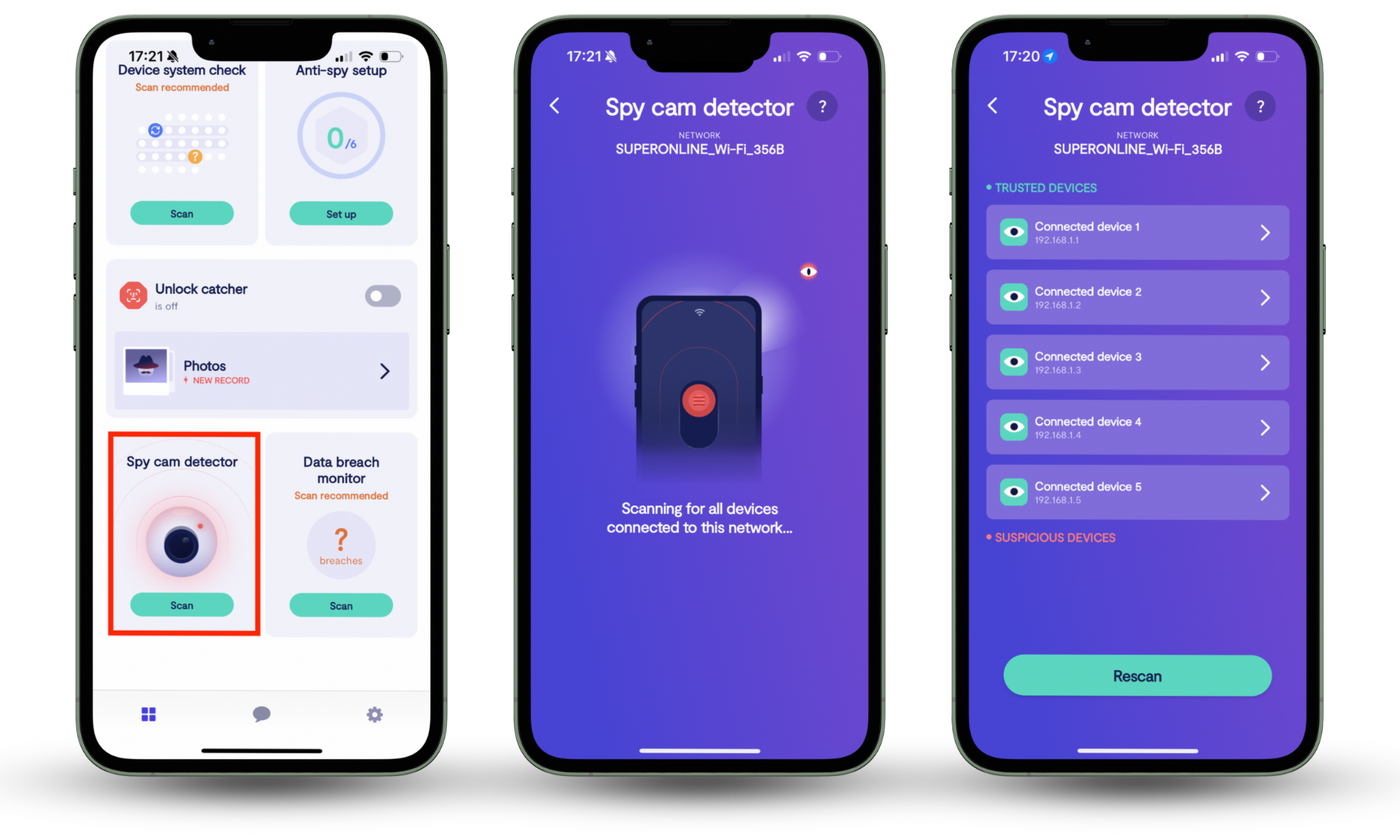
The danger isn’t limited to public Wi-Fi. At home, you should also check who is on your network. Clario Anti Spy’s Spy cam detector shows you all devices on your Wi-Fi and helps you spot intruders who might piggyback on your network for cracking purposes.
Here’s how to run Clario Anti Spy’s Spy cam detector:
- Download Clario Anti Spy, and create an account.
- Select Spy cam detector.
- Tap Scan to view devices on your Wi-Fi.
- Check the list for unknown devices.
- Block or remove suspicious connections.
- Brush up on your knowledge of scams. Many crackers employ scamming techniques to infect your system with adware, malware, and spyware. If you know what to look out for – like phishing emails and infected ads – you will reduce your risk of being cracked. You should also know what to do if you do get scammed to prevent further damage.
- Keep your devices and software updated. With every update comes additional security measures. As devices become older, more vulnerabilities are discovered. Crackers are constantly adding tools to their arsenal, and developers need to update their software to patch these vulnerabilities constantly.
- Use a trusted VPN. A VPN protects you against network cracking by encrypting your internet traffic. Even if someone intercepts data on a public Wi-Fi, they cannot read it once encrypted. Using a VPN makes it harder for crackers to spy on your activity or steal your credentials. Some popular VPN providers include:
- NordVPN
- ExpressVPN
- Proton VPN
- Surfshark
- Use an Antivirus. Antivirus helps guard against malware, adware, spyware, and other common threats that crackers use to break into systems. It blocks infected files and prevents malicious websites from loading.
But many cracking attempts rely on disguised apps that look harmless. Apps you might even download willingly, but which have ulterior motives.
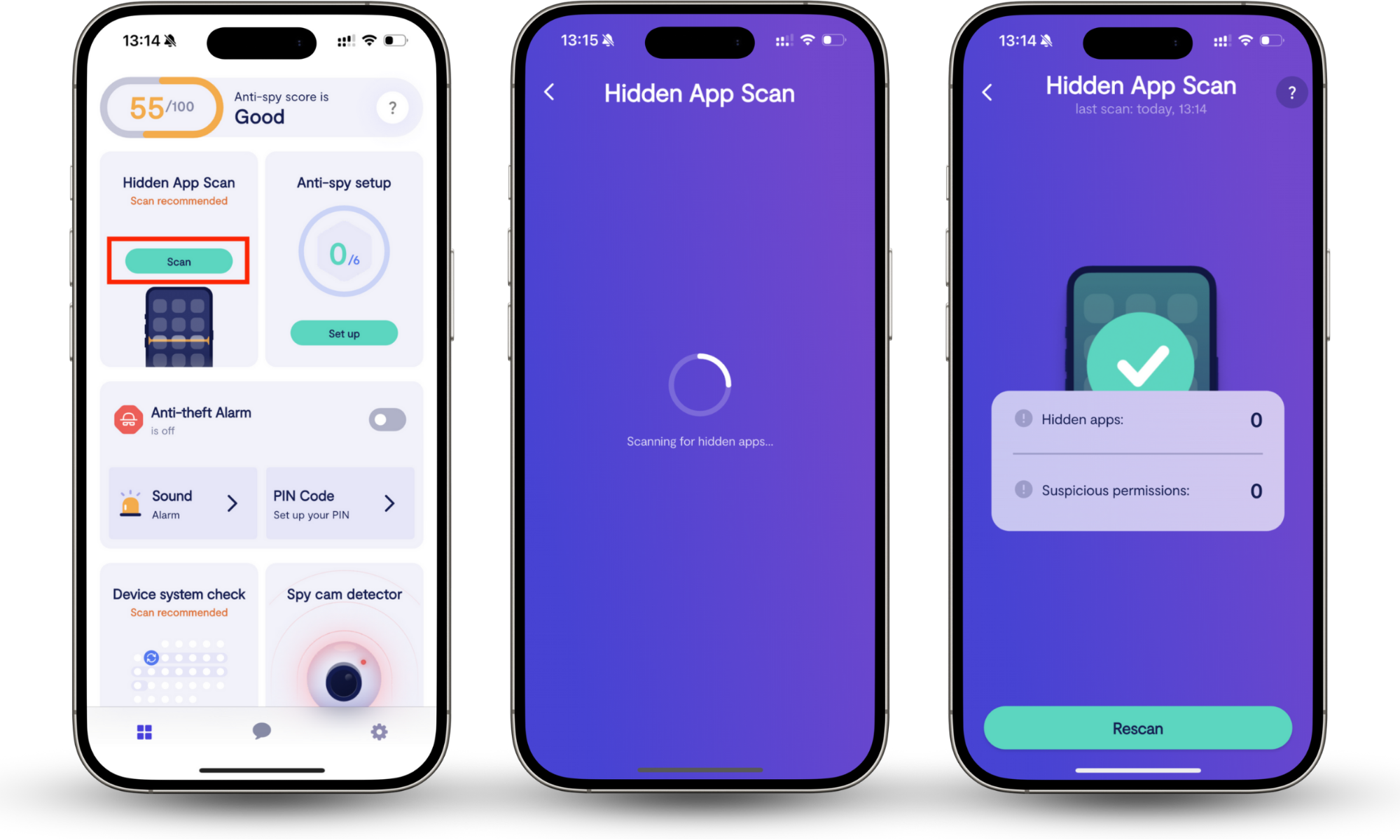
Clario Anti Spy’s Hidden app scan detects those hidden apps, checks their permissions, and shows you which ones put your data at risk.
Follow these steps to run the Hidden app scan:
- Download Clario Anti Spy and sign in.
- Select Hidden app scan.
- Tap Scan to check your phone.
- Review suspicious apps and permissions.
- Follow the recommendations to remove threats.
Protect Yourself From Cracking Today
Cracking and scams are becoming more common every year, so it’s important to stay on top of your digital security if you want to protect your data and devices.
Clario Anti Spy helps stop crackers by detecting hidden apps, monitoring risky permissions, and scanning your network for intruders. Protect your phone today and keep your information safe.


