Table of contents
- How & when did cryptojacking emerge?
- Main types of cryptojacking
- File-Based Cryptojacking
- Browser-Based Cryptojacking
- Cloud Cryptojacking
- How exactly does cryptojacking work?
- Can cryptojacking target mobile devices?
- How to detect cryptojacking
- Tips on how to stop cryptojacking
- Be aware of trends
- Perform regular malware & spyware scans
- Leverage anti-cryptomining extensions
- Leverage Ad-Blockers
- Best cybersecurity practices to follow
- Conclusion
Commonly referred to as “malicious cryptomining”, cryptojacking occurs when cybercriminals hijack personal computers with the intent of installing malicious software.
Following the installation, they can use computers to remotely “mine” digital money (cryptocurrencies) such as Bitcoin and others. The main challenge of cryptojacking is that it’s tough to detect by non-tech people. Apart from using the resources and power of personal/business computers to mine crypto, attackers can also steal cryptocurrency from people’s digital wallets.
Higher electricity bills, slow response times, computer overheating, or increased processor usage could be a sign of an attack. Read more and you’ll learn how to detect cryptojacking, as well as some tips and tricks on how to stay safe.
How & when did cryptojacking emerge?
Cryptojacking rose to fame in 2017 when the well-known cryptocurrency Bitcoin was booming. Around this period, Coinhive emerged too. This was a cryptojacking service made up of Javascript files. In simple terms, the promise of Coinhive was to give website owners an “opportunity” to make more money from their website visitors.
Numerous website owners jumped in as they believed this form of crypto-mining was easier, had more resources, and was a much better alternative to paid ads. For the service to work, it required the approval of visitors and website owners. But soon enough, Coinhive began implementing malicious code. The purpose was to exploit the main vulnerabilities of the websites, draining resources without anyone knowing and mining cryptocurrency for them.
Even though Coinhive has been shut down, replicas and scripts of the software are still available, leaving numerous other websites exposed to potential cryptojacking.
Since 2020, cryptojacking has seen a rise in mobile device attacks, where hackers exploit mobile apps with vulnerable permissions. These attacks are more difficult to detect due to the lack of system monitoring on mobile platforms. Recent reports have also shown that AI-powered cryptomining scripts are now being used to enhance mining efficiency, making these attacks harder to detect and mitigate.
Main types of cryptojacking
There are three core tactics to mine cryptocurrencies using cryptojacking: cryptomining script execution via malware, hijacking cloud services, and breaking IT infrastructures.
File-Based Cryptojacking
File-based cryptojacking uses malicious emails with executable files that users unknowingly download. These emails often impersonate trusted entities, like banks, and ask recipients to download attachments disguised as invoices or bank statements. Once downloaded, the malicious scripts run in the background, using the device’s resources to mine cryptocurrency without the user’s knowledge.
Browser-Based Cryptojacking
Browser-based cryptojacking occurs when hackers embed cryptomining scripts into websites, often through outdated WordPress plugins or malicious display ads. These scripts run within common browsers like Google Chrome, Mozilla Firefox, and Safari, using the device’s resources to mine cryptocurrency without the user’s knowledge.
Cloud Cryptojacking
Cloud cryptojacking occurs when attackers gain unauthorized access to an organization’s cloud service by exploiting vulnerabilities in code or files, often searching for API keys. Once they have access, they use the cloud’s CPU resources to mine cryptocurrency, resulting in increased electricity costs and overworked infrastructure.
How exactly does cryptojacking work?
Is cryptojacking illegal and how does cryptojacking work? Yes, it is. Just like most pioneering inventions, blockchain technology is a moral paradox. On the one hand, it has revolutionized industries like finance and payments. On the other hand, it has been used numerous times to fuel completely illegal activities. As a consequence, the world associates blockchain with shady and useless cryptocurrencies. To many, it’s an illusion driven by hype and speculation.
Because cryptocurrencies require enormous energy to be “mined” (aka produced), cryptomining has morphed into cryptojacking, a serious cybersecurity issue people and companies must be aware of if they want to steer clear of unwanted data breaches. This is how cryptojacking works assuming you use the Google Chrome browser:
- All of a sudden you get an email from your bank. The subject of the email is click-bait and usually sounds like this: “Your requested bank statement is ready to download. Click here!”
- You open the email and download the attachment. Nothing happens, your attachment is nowhere to be found, and if you do find it on your computer, you can’t open it. If you are not tech-savvy, you’ll probably move on with your life and do nothing.
- While you do nothing, the crypto-mining malware has been installed in the backend of your computer’s infrastructure via a so-called “script”.
- The attackers will gain access to your device and use it to drain its power, or worse, access other mobile apps or messaging services you use.
- The ill-intended miner will start running the code on your device by using its power to calculate “hashes”. This will mine for his very own cryptocurrency. Then, once he/she is done, the coins will be transferred into their digital wallets.
This example only illustrates what happens to Google Chrome browsers but this doesn’t mean that other browsers are immune to threats. And although it might seem like no harm has been done, the attackers can seriously damage your device by triggering overheating and skyrocketing your electricity bill. Detection matters more now than ever.Now you have some idea on cryptojacking and how it works, let us have a closer look at how to detect and protect your devices, and ultimately your identity from cryptojacking.
In 2025, AI-powered cryptomining scripts have made it easier for attackers to bypass traditional detection systems, running efficiently without raising red flags in network traffic. These advanced scripts can adjust their operations dynamically to avoid detection and make the mining process more stealthy.
Can cryptojacking target mobile devices?
While cryptojacking traditionally targeted desktop and server computers, mobile devices are increasingly becoming a target. With many users downloading unverified apps or clicking on malicious ads, smartphones and tablets are now vulnerable to these attacks. iOS and Android devices can unknowingly become part of a cryptojacking botnet, using their processing power to mine cryptocurrencies in the background. Always be cautious when downloading apps from third-party sources and consider using trusted anti-malware apps for added protection.
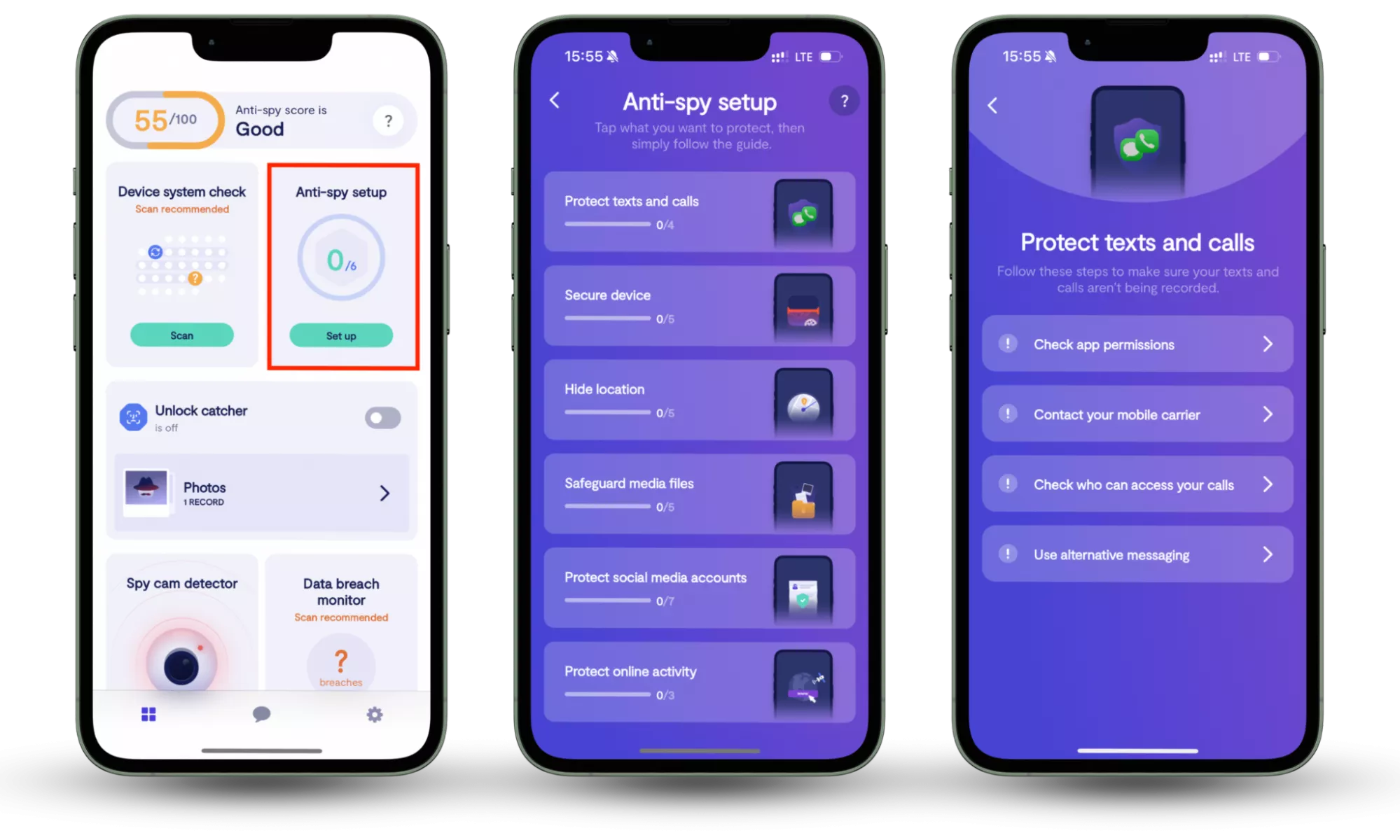
At Clario Tech, we understand how cryptojacking can affect not only your desktop but also your mobile devices. That’s why our Clario Anti Spy's Anti-spy setup feature is designed to detect these threats before they can harm your devices.
One of our customers was shocked when he noticed his phone overheating and draining its battery more quickly than usual. He had recently downloaded a few apps from unverified sources and couldn’t figure out why his phone was underperforming. After noticing a significant increase in his mobile data usage, he suspected something wasn’t right.
With Clario Anti Spy’s help, we were able to detect the malicious software and secure his device. He also set up ongoing protection, ensuring his phone is shielded from similar attacks in the future. Thanks to Clario Anti Spy, our customer now feels confident that his devices are protected.
Here is how you can use Clario Anti Spy's Anti-spy setup feature:
- Download Clario Anti Spy and create an account.
- On the home screen, look for Anti-spy setup. Press Set up when you find it.
- You’ll now see a list of actions you can take to make your device less vulnerable. Go through each action step-by-step until you’ve completed the process and secured your phone.
How to detect cryptojacking
Cryptojacking can be particularly harmful in a business environment. Office spaces have tens of computers, and the majority are high-end, fast, and capable of handling all kinds of business operations. And yet, detecting if your organization’s IT infrastructure has been compromised can be challenging. The best tactic is to be vigilant and mindful about such cyberattacks. It’s better to be safe than sorry. Here are some steps on how to check for cryptojacking:
- Look for poor computer performance. A major symptom of cryptojacking could be a sudden decrease in your computer’s performance. If, for any reason, one or more employees complain about having really slow computers, it might be best to have them checked out. The same rule applies with personal devices.
- Computer overheating. Even though overheating is not always the result of a cryptojack, it’s worth taking this into account. In time, overheating may shorten the life of your computer and even trigger complete damage. That being said, if you’re searching the web for a new fan to cool it off, you might as well read about cryptojacking malware and cybersecurity tools to help you stay safe too.
- Sudden increase in CPU Usage. Spikes in CPU usage can easily be done from Task Manager or Activity Monitor. If you spot a sudden increase while browsing through a website (or more) that looks suspicious or has little content, it might be a sign of cryptomining scripts running without you knowing.
- Website monitoring. Cyberattackers constantly seek vulnerable websites because they know it’s easier to embed malicious crypto mining code. To make sure it doesn’t happen to you, it pays to monitor your most used websites and pay close attention to any changes. The sooner you detect that you’ve been hijacked, the better chances you have to save your device.
Tips on how to stop cryptojacking
It’s better to prevent an attack from happening in the first place than to stop it. However, if you suspect you may have downloaded cryptojacking malware, the first thing to do is to remove it from your device. Assuming that you already have anti-virus software installed on your computer, do a thorough scan (NOT a fast scan) of the device. Please note this could take several hours.
Following this step, you can quarantine the malware or remove it altogether. However, no matter how advanced your anti-virus is, hackers these days are becoming increasingly smarter. If, for any reason, you suspect that the software provider you’re using hasn’t caught up on the cryptojacking attempt, you could reset your computer and reformat the hard drive.
In case you don’t have IT experience, ask for the recommendation of an IT professional. Otherwise, you may lose important data already stored on your computer. Further actions you can take include:
Be aware of trends
Regardless of your experience with blockchain technology and cryptocurrency, it’s worth staying informed about cryptojacking and related threats because this attack vector continues to evolve rapidly. Cryptojacking remains relevant in 2025 as attackers increasingly exploit common behaviors like visiting compromised sites or running malicious scripts in browsers and cloud environments.
For ongoing updates, expert analysis, and breaking news related to cryptojacking and other crypto‑related cyber threats, check out these trusted sources:
- CoinDesk. A leading news site covering cryptocurrency markets, security trends, and blockchain developments worldwide.
- The Hacker News. Provides real‑time cybersecurity news, including cryptojacking incidents, emerging malware campaigns, and risk trends.
- Cybersecurity Ventures. Offers daily feeds on broader cryptocrime and threat landscapes, including mining malware and crypto attacks.
- Cybernews. Publishes insight on top crypto scam and hacking trends in 2025 and broader cybercrime shifts relevant to blockchain users.
Perform regular malware & spyware scans
Now you have some idea of what cryptojacking malware is, make some time to perform regular malware and spyware scans for your devices. Do it at least once a month just to be safe, and consider investing in a software solution with a good reputation and track record.
Modern anti-spy tools have started incorporating advanced cryptojacking detection algorithms, leveraging behavioral analytics to identify unusual CPU spikes, even when the attack is masked in the background.
Leverage anti-cryptomining extensions
Anti-cryptomining extensions can be just as useful. Since cryptojacking scripts are launched in-browser, such extensions will block them completely. Anti Miner and Miner Block are two free examples you can install directly from Google Chrome.
Leverage Ad-Blockers
Ads are everywhere and even though the majority are completely harmless, you can’t really be sure what you’re clicking on every time you see a catchy ad. One of the easiest ways to embed a cryptojacking script is within an ad. To make sure it doesn’t happen to you, AdBlocker is a great free extension compatible with numerous browsers.
Experts recommend using a multi-layered
Experts recommend using a multi-layered security approach to prevent cryptojacking. This includes not only relying on antivirus software but also using web filters, browser extensions, and regularly educating employees on phishing and malicious website tactics. Implementing AI-powered monitoring systems that can detect abnormal mining behavior is essential for larger organizations.
Best cybersecurity practices to follow
In general, cryptojacking can be avoided if you:
- Avoid unsecured websites (no SSL) and suspicious links.
- Don’t open emails or attachments from unknown senders.
- Keep your software updated, including antivirus tools.
- Use anti‑cryptojacking extensions like NoCoin and MinerBlock.
- Install ad-blockers to block malicious scripts and ads.
- Monitor CPU usage for unusual spikes or overheating.
- Enable endpoint protection tools with cryptojacking detection.
- Educate users to recognize phishing attacks and malicious downloads.
Secure your digital life and benefit from all the perks of the internet without worrying that your personal information has been exposed for the whole world to see.
Conclusion
Cryptojacking remains a growing threat, but with the right precautions, you can effectively safeguard your devices and personal data. By following these best practices, from keeping your software updated to using anti-cryptojacking tools and monitoring system performance, you can effectively protect against this silent yet dangerous cyberattack. For added protection, Clario Anti Spy offers comprehensive, real-time defense against cryptojacking and other online threats, ensuring your devices stay secure with minimal effort. Stay informed and proactive to keep your devices safe.
Read more:


