Table of contents
- Is it possible to hack an iPhone remotely?
- 1. Remote hacking is costly
- 2. Vulnerabilities in iOS are immediately patched
- 3. Remote hacking is unlikely to happen to individual users
- How can a hacker access your iPhone remotely
- 1. Via public Wi-Fi networks
- 2. iPhone Hacks with Malicious Programs
- 3. Phishing Emails or Text Message
- 4. SIM card replacement
- How to ensure iPhone security
- 1. Lock your iPhone
- 2. Turn on two-factor authentication
- 3. Customize your lock screen
- 4. Install an anti-spyware program
- 5. Don’t click on suspicious links
- 6. Keep iPhone and apps up to date
- 7. Turn off your hotspot in crowded places
- Conclusion
Is it possible to hack an iPhone remotely?
While it is possible to hack an iPhone remotely, it is difficult and expensive. Apple prides itself on the security of its devices and is a leader in cybersecurity.
Let’s look at some reasons remote iPhone hacking tends not to happen.
1. Remote hacking is costly
Hacking is costly and time-consuming. It needs extensive research and complex software infrastructure. Hackers also take on substantial risk.
Here are the main reasons hacking is costly:
- It takes time to find operating system vulnerabilities.
- Hacking infrastructure, like exploit kits, botnets, and encryption software, is expensive.
- Hackers must rigorously test hacking tools, which is labor intensive.
- Maintaining anonymity requires multiple tools (proxies, encryption, botnets, etc.).
- There is substantial legal risk.
All of these factors make it prohibitively resource-intensive to attack a single iPhone. Hackers are more likely to balance risk by seeking greater financial or reputational rewards.
2. Vulnerabilities in iOS are immediately patched
Apple is well-known for its rigorous security policy. It’s got a good track record of addressing bugs and vulnerabilities quickly.
It issues regular operating system updates to enhance device protection. These updates often include security patches.
Apple's proactive stance is further supported by a bug bounty program, encouraging the reporting of security flaws in exchange for rewards.
iPhones also have several built-in security features, like phone hack check codes and app sandboxing.
3. Remote hacking is unlikely to happen to individual users
Because of cost, complexity, and time, your personal phone is unlikely to be hacked remotely.
If somebody did hack your iPhone, it would most likely happen non-remotely. The hacker would need physical access to your device and your authentication details.
They will then install a spying app on your phone to track your activity. However, running a regular anti-spyware scan will protect against this.
Knowing how to remove a hacker from your phone is extremely important. However, preventing getting hacked is even better.
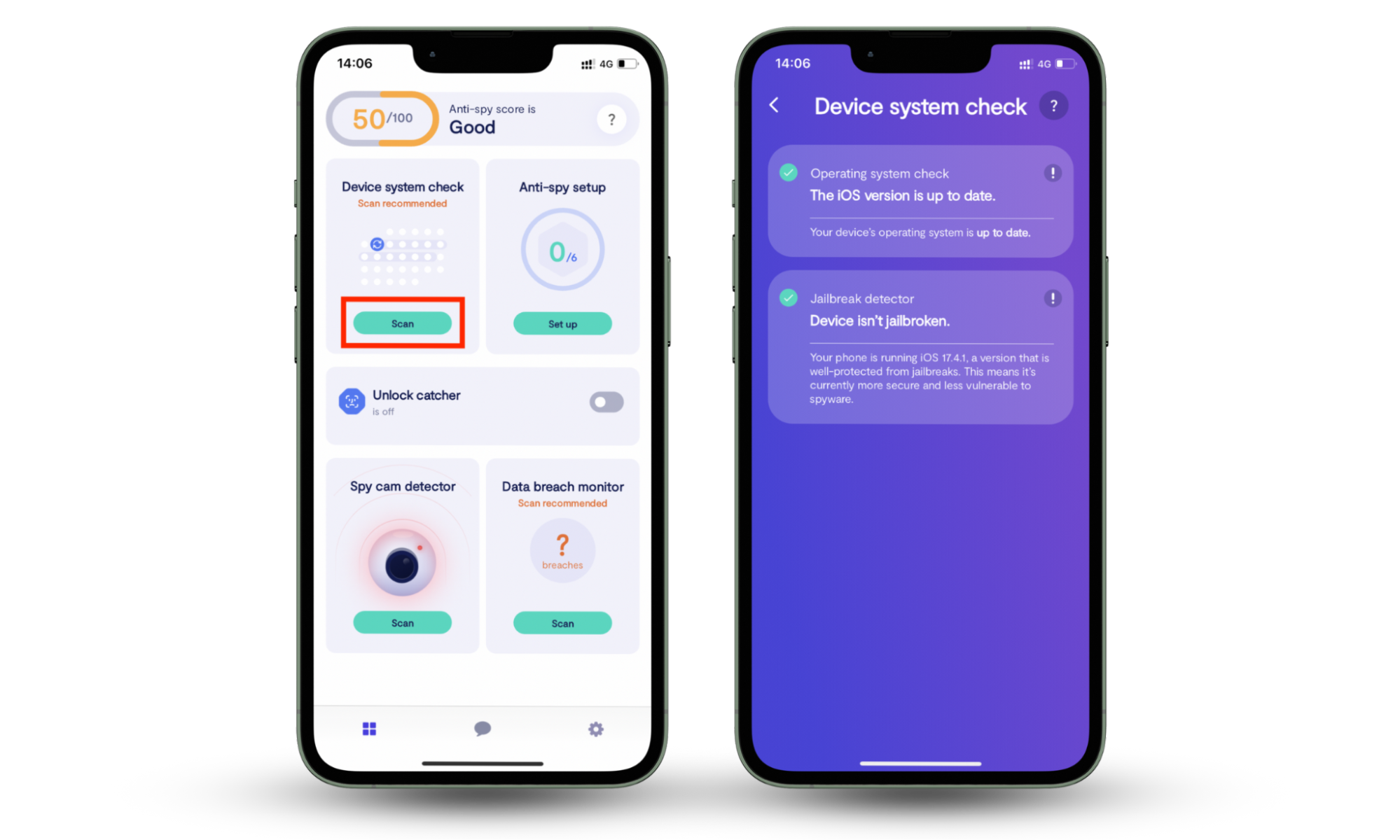
A jailbroken iPhone dramatically increases the chances of your data being seen or stolen. Clario Anti Spy can check your phone for signs of jailbreak so that you can take action to improve your security. The app’s Device system check scans for jailbreaks and available iOS updates—after all, keeping your phone up to date means you’ve got all of Apple’s latest security features working for you.
Here’s how to use Clario Anti Spy’s Device system check to see whether your iPhone is jailbroken:
- Download Clario Anti Spy, and get a subscription to set up your account.
- Open the app and tap Scan under the Device system check.
- When the scan is complete, check the results—is your iPhone jailbroken?
How can a hacker access your iPhone remotely
Remote hacking occurs when a hacker who is not physically present breaks into your iPhone. It’s different from non-remote hacking, which requires direct access to your device.
Let’s take a look at the most common methods.
1. Via public Wi-Fi networks
Attackers can use the following techniques to access your phone via a public Wi-Fi network:
- Man-in-the-middle attacks: The attacker uses tools, like an SSL stripper or packet injector, to interrupt communications between your iPhone and the network and access unencrypted data.
- Exploit public Wi-Fi vulnerabilities: This involves creating rogue access points, which trick the phone into connecting with them to capture data or inject malware.
- Zero-day exploits: This is when attackers use unpatched vulnerabilities in iOS to gain unauthorized access or control of your device.
- Remote code execution (RCE): RCE execution involves running malicious code on your iPhone, mainly by identifying app vulnerabilities accessible over the public network.
2. iPhone Hacks with Malicious Programs
If a hacker manages to gain access to your phone, they may install one of the following types of software:
- Spyware installation: Tricks you into installing software that secretly monitors and transmits personal data and may mean someone can control your iPhone remotely.
- Ransomware attacks: Locks the iPhone, demanding payment for device control restoration.
- Trojan apps: Masquerades as legitimate applications that perform malicious operations.
- Keyloggers: Records keystrokes to steal passwords and sensitive information.
- Adware: Automatically displays or downloads advertising material, often without user consent.
3. Phishing Emails or Text Message
Attackers might use these techniques the following techniques to access your phone through emails or text messages:
- Deceptive links: Persuades you to click on links that install malware or collect personal information.
- Fake alerts: Mimics legitimate warnings from trusted sources, like Apple security alert, to obtain sensitive data.
- Impersonation scams: Pretends to be a familiar contact requesting personal or financial information.
- Security threats: Claims your account is compromised to provoke an immediate, fear-driven response.
- Urgent requests: Uses urgency to trick you into making hasty decisions, bypassing their usual skepticism.
4. SIM card replacement
Attackers might employ the following strategies to gain control of your phone via SIM card replacement:
- Social engineering: Uses manipulation to persuade customer service representatives to transfer your phone number to a new SIM card they control.
- Identity theft: The theft of your personal information to pass identity verification processes for unauthorized SIM card replacement.
- Impersonation: Pretends to be you and requests a SIM swap, citing a plausible reason, like a lost or damaged phone.
- Exploiting weak authentication: Takes advantage of insufficient security measures in the SIM replacement process.
How to ensure iPhone security
Take the following steps to ensure the security of your iPhone:
- Make sure it’s locked.
- Turn on two-factor authentication.
- Customize your lock screen.
- Install an anti-spyware program.
- Don’t click on suspicious lines.
- Keep your iPhone and apps up to date.
- Turn off your hotspot in crowded places.
Let’s look at each of these in more depth.
1. Lock your iPhone
Ensure your iPhone is always secured with a strong passcode or biometric options like Face ID or Touch ID.
This simple action prevents others from accessing your data. It's your first line of defense against unauthorized use, especially if your phone is misplaced or stolen.
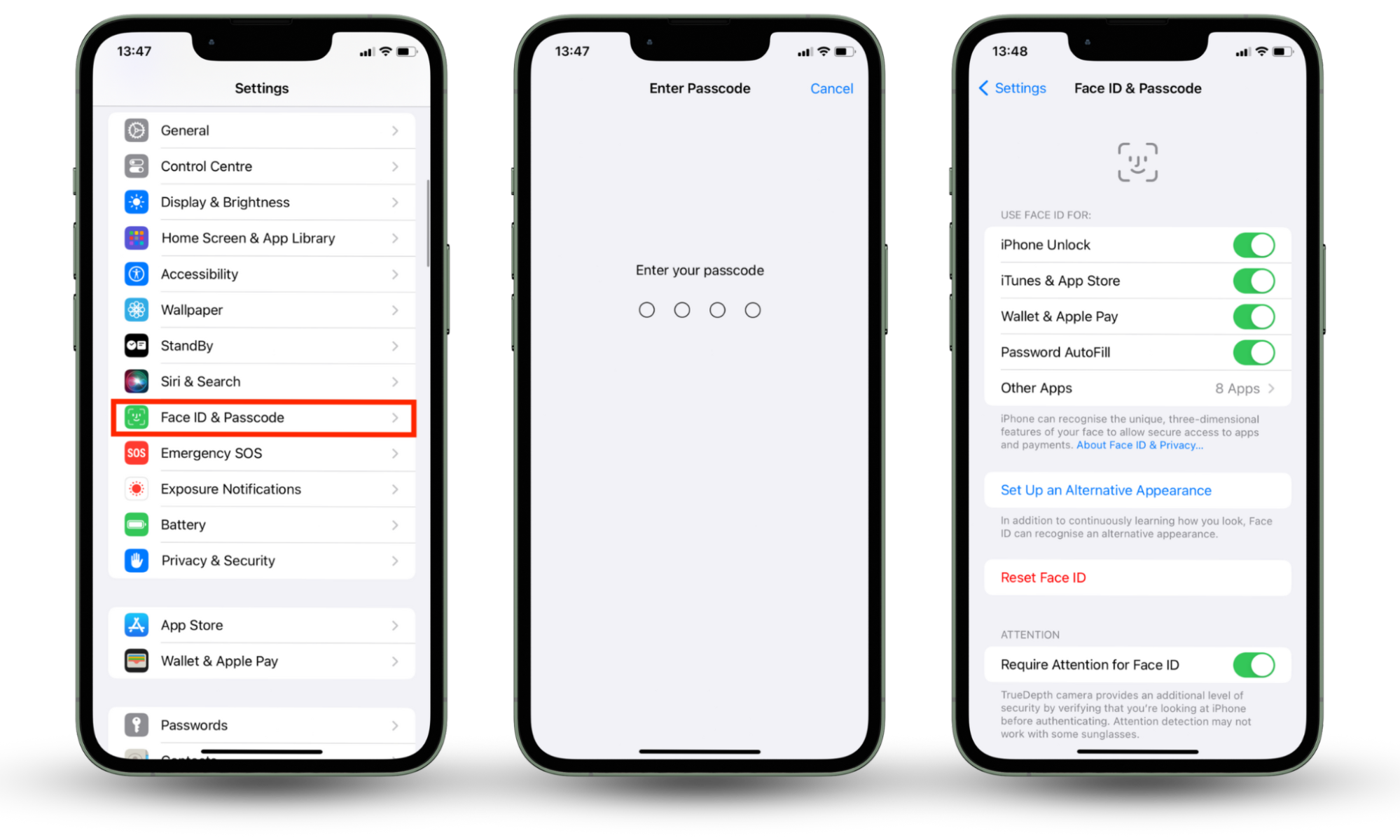
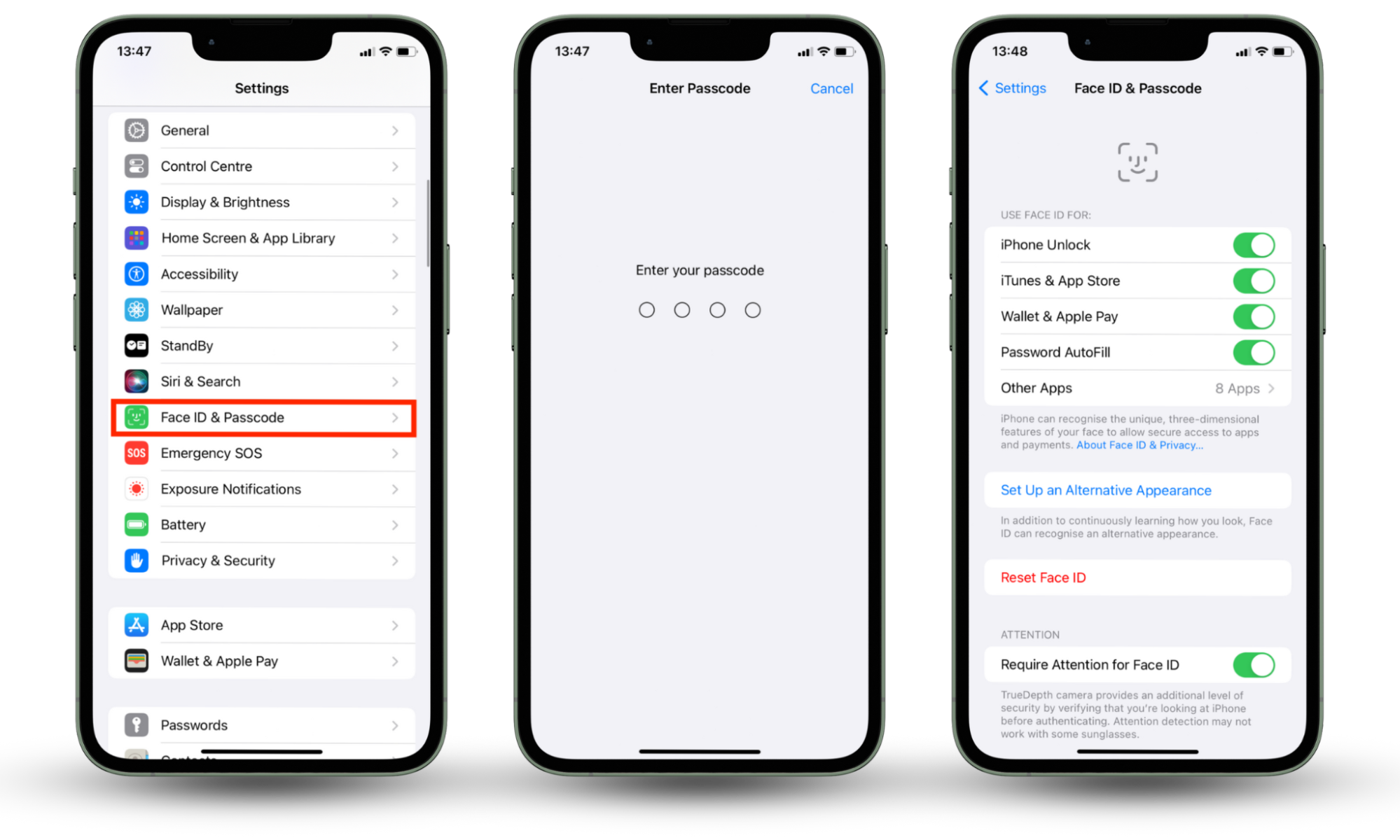
Here is how to set up Face ID or Touch ID on your iPhone:
- Go to Settings and select Face ID & Password.
- Enter your passcode to continue.
- Press Set Up an Appearance or Set Up an Alternative Appearance (if you already have one face your phone recognizes).
- Follow the on-screen instructions to set up a Face ID or Touch ID.
Setting up Face ID also prevents people you know from installing spying apps on your device. If you think somebody may have installed spyware, you can go through a published list of apps that spy on your iPhone to double-check.
2. Turn on two-factor authentication
Activating two-factor authentication for your Apple ID significantly enhances security. It requires a password and a verification code (sent to another number) when you sign in to your Apple ID account.
This double-check makes it much harder for unauthorized users to access your account.
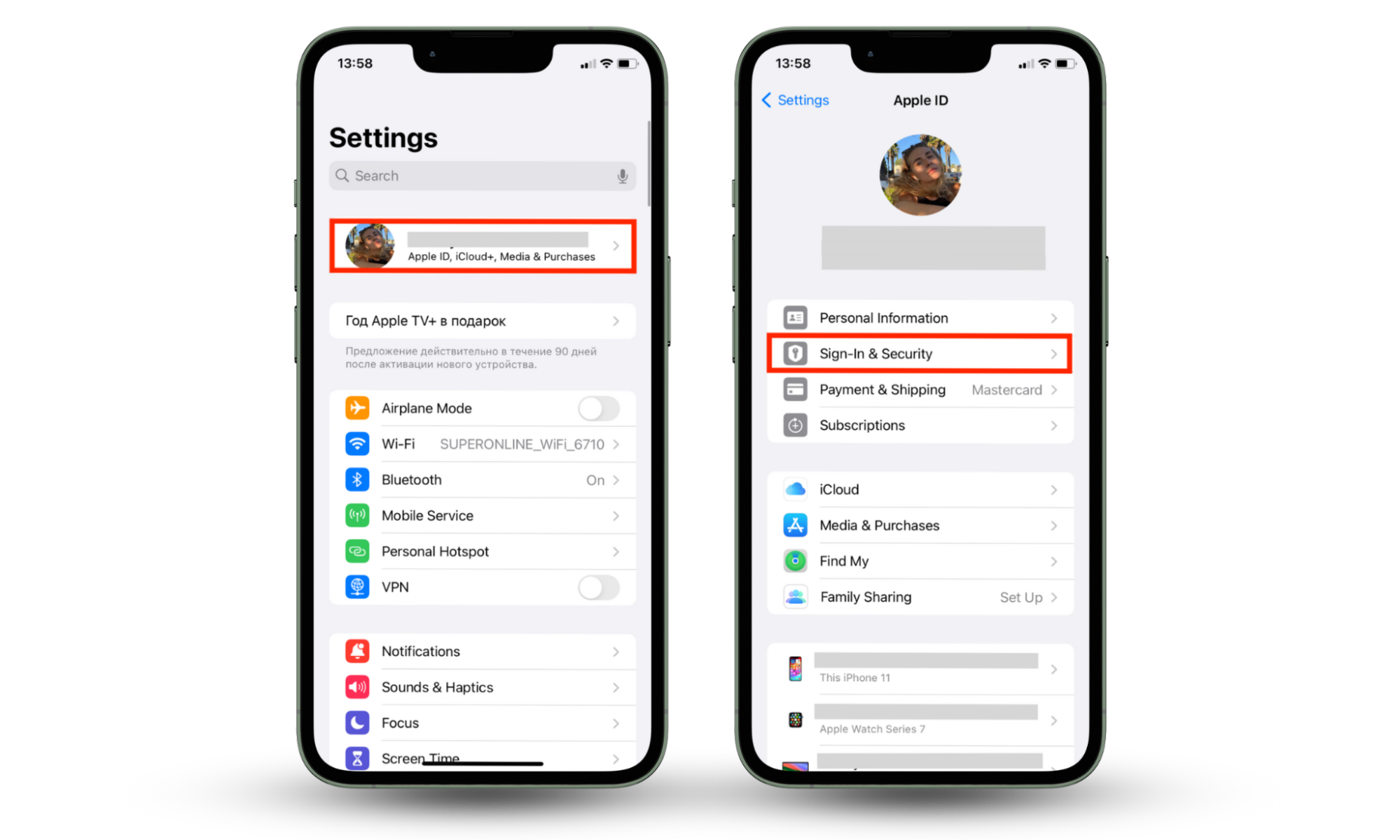
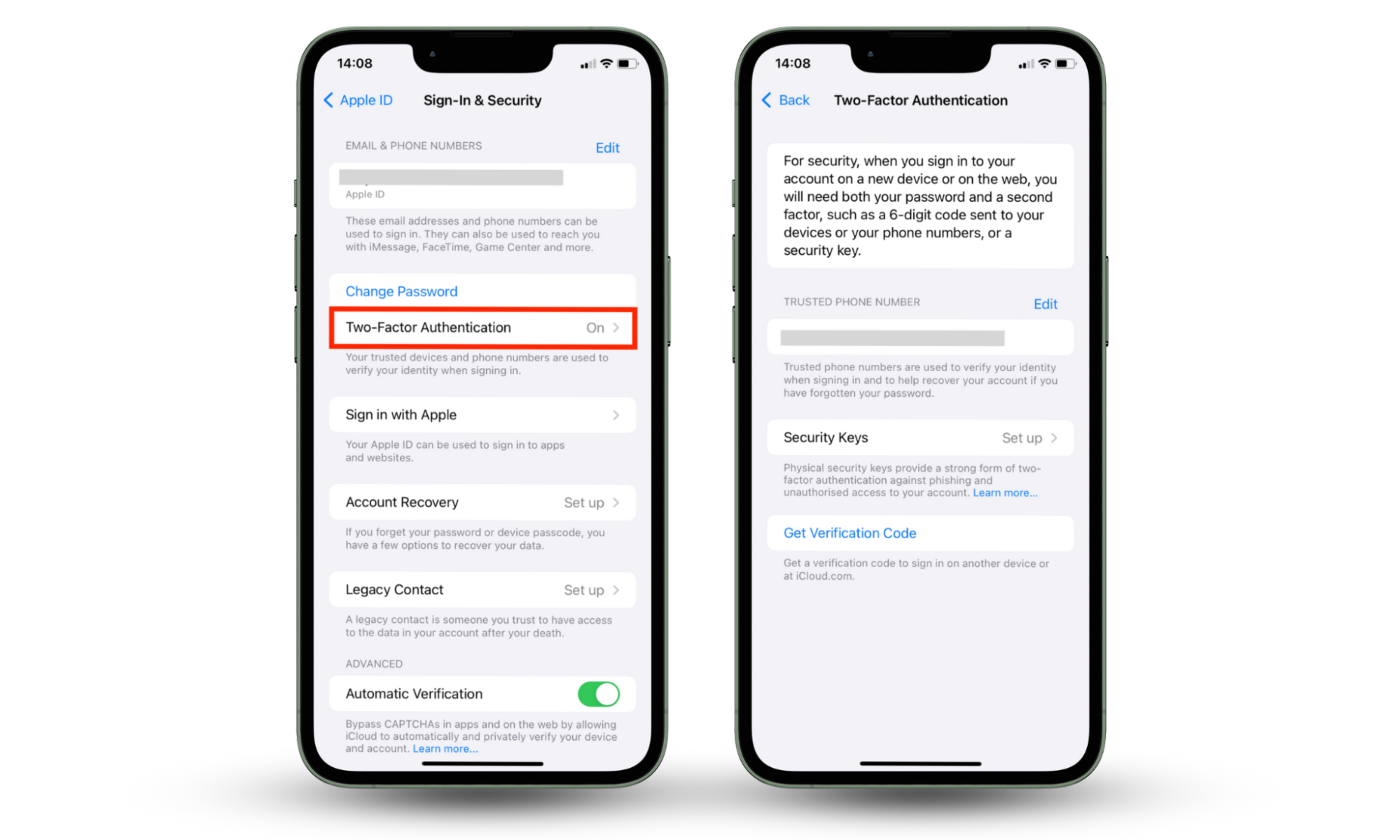
How to set up two-factor authentication for your Apple ID on your device:
- Go to Settings > your name > Password & Security (or Sign-in & Security).
- Tap Turn On Two-Factor Authentication.
- Then, tap Continue and follow the on-screen instructions.
3. Customize your lock screen
You can customize your lock screen so that notifications and features (like your camera) aren’t accessible without first logging in. This setting helps keep your sensitive information out of sight.
It's a quick way of enhancing privacy, ensuring only minimal information is accessible without full access.
How customize your iPhone lock screen:
- Go to Settings and select Face ID & Passcode or Touch ID & Passcode (depending on which you have enabled).
- Enter your passcode to continue.
- Adjust the settings to modify your lock screen.
4. Install an anti-spyware program
If you’re wondering how to secure your iPhone from hackers, installing a reputable security app can help. Clario Anti Spy includes a variety of privacy and security features that can help keep your iPhone safe.
We’ve already talked about the Device system check, which can scan your iPhone for signs of a jailbreak. But even if your phone isn’t jailbroken, Clario Anti Spy can help you reinforce your privacy.
The app’s Anti-spy setup can help you work through your phone’s security settings, making sure that your online activity, calls, and text messages are impossible to track.
And it’s not just about improving your phone’s privacy. The Spy cam detector will also scan your Wi-Fi network to make sure that there are no suspicious devices, such as hidden cameras, connected to the network—meaning that you’ll have peace of mind that no one’s spying on you in your home.
5. Don’t click on suspicious links
Avoid clicking links from unknown sources that seem out of character, even from known contacts. Malicious links can lead to phishing attempts or malware installations.
Caution helps protect your device from being compromised by harmful software or losing sensitive data to scammers. It will also eliminate the possibility that someone can control your iPhone remotely through this method.
6. Keep iPhone and apps up to date
Updates for iOS and apps often include important security patches. These updates seal up vulnerabilities, keeping your device safe from hacking attempts.
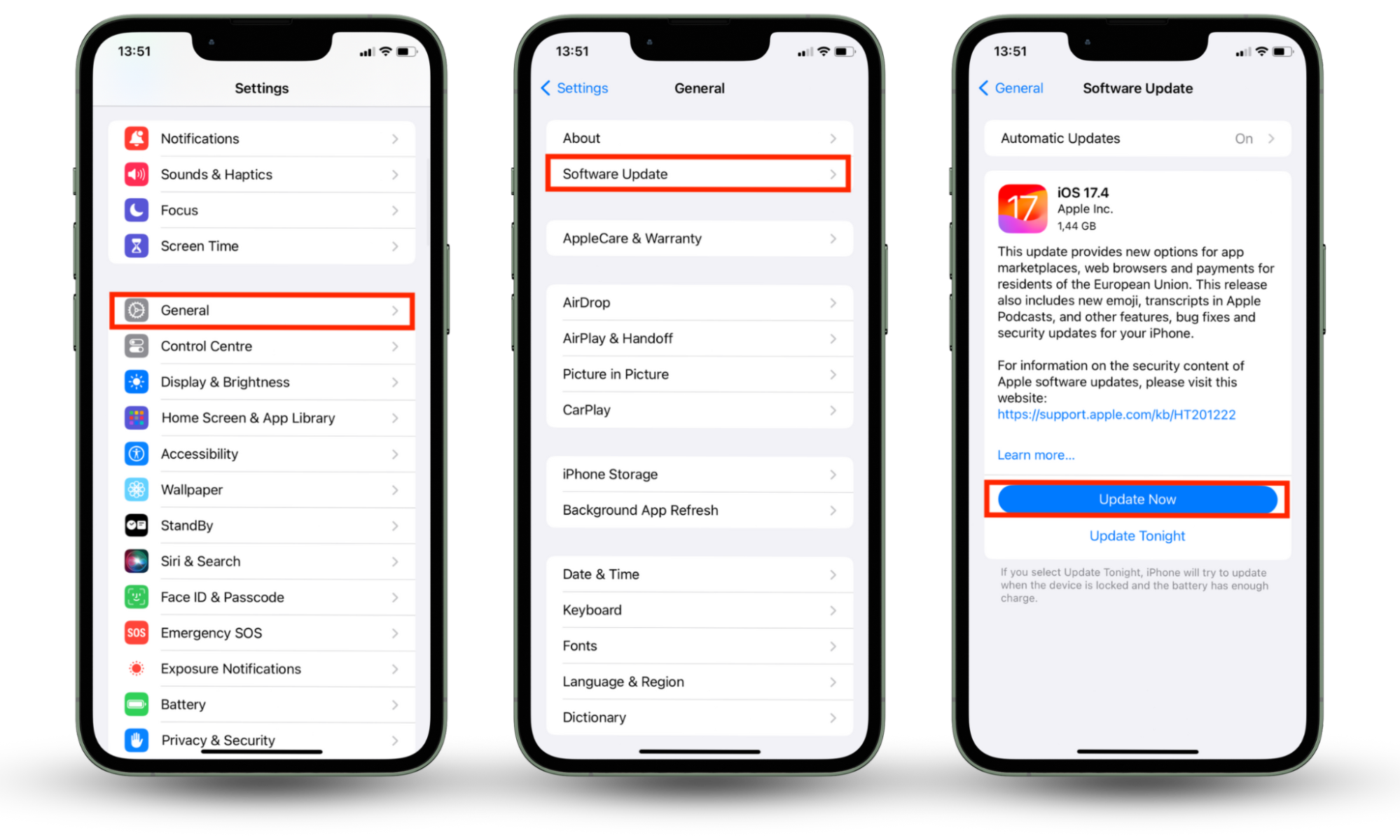
Installing these updates as soon as they’re released ensures you're protected against the latest threats and keeps your iPhone running smoothly. Follow these steps to check if there are any updates available on your iPhone:
- Go to Settings > General > Software Update.
- If any update is available, press Update Now.
- Wait for the update to download, and then press Install.
Tip
Enable automatic updates to prevent missing new security patches for iOS.
7. Turn off your hotspot in crowded places
In crowded areas, turning off your iPhone's hotspot feature prevents hackers from accessing your connection and taking advantage of weak encryption or an easy-to-guess password.
It's a simple yet effective step to safeguard your internet connection and personal data from being exploited in public areas.
Conclusion
Hacking an iPhone remotely is possible, but it’s difficult. And by taking a handful of straightforward security measures, you significantly reduce the risk.
Regular updates, cautious clicking, and enabling security features like two-factor authentication and lock mode are effective strategies.
Remember that protecting your iPhone doesn’t require technical expertise. You simply need to commit to consistently following the best practices in this article. A proactive approach is the safest way to secure your device against potential threats.
And if you’re worried someone has hacked your phone, the best thing you can do is install an app like Clario Anti Spy and check if your phone has been jailbroken. After all, a jailbroken iPhone has a much higher risk of hacking and malware.


