Table of contents
- Is iPhone safe from hackers?
- How can someone hack your iPhone?
- 1. Malicious links
- 2. Weak passwords
- 3. Unsecured Wi-Fi
- 4. Spyware
- 5. Keyloggers
- 6. Hacking your iCloud
- 7. Tracking programs
- What are the signs of your iPhone being hacked
- 1. Your battery depletes at an alarming rate
- 2. Your data depletes faster than it normally does
- 3. Your iPhone’s performance starts to deteriorate
- 4. Your friends and family report receiving concerning messages from you
- 5. You are locked out of your Apple ID
- 6. Strange apps appear on your home screen
- What to do if your iPhone has been hacked
- 1. Turn off your iPhone
- 2. Remove your phone’s external components
- 3. Lock down your Apple ID
- 4. Enable 2FA
- 5. Check your phone’s settings
- 6. Call your cellular service provider
- 7. Use a VPN service
- How to protect your iPhone from being hacked
- 1. Use an anti-spying tool
- 2. Don’t jailbreak your iPhone
- 3. Update iOS regularly
- 4. Use a complex passcode
- 5. Enable 2FA
- 6. Only sync important data
- Conclusion
Is iPhone safe from hackers?
No, it is not. iPhones, like other mobile devices, are vulnerable to hacking and cyberattacks. In many cases, this is achieved by remotely hacking your iPhone, accessing your data, and stealing your identity and money.
Apple has previously warned users about the threat of hacking. According to a Reuters article, it sent users in 92 countries a warning that attackers attempted to remotely access their iPhones. Jailbreaking, on the other hand, offers people with physical access to your iPhone a more straightforward solution to breaching it. It removes an iPhone’s software restrictions to gain root access, weakening its defenses and making it vulnerable to attacks. You can also check if your iPhone is jailbroken with Clario Anti Spy if you are concerned it may be breached and vulnerable.
The reality that people can hack iPhones highlights the importance of using strong passwords, keeping your phone away from people you don’t trust, and practicing healthy internet habits.
How can someone hack your iPhone?
Someone can hack your iPhone through various methods, including:
Before removing a hacker from your iPhone, it’s crucial to know the various methods cyber attackers can use to access your device. In the guide below, we delve deeper into these various points of entry.
1. Malicious links
Hackers and scammers create and distribute malicious links to promote fraud and scams, implement cyberattacks, and spy on victims. By clicking on a malicious link, you risk unknowingly downloading spyware on your iPhone, which hackers can use to gain access to your phone, spy on you, and steal your sensitive information over an extended period.
People can hack iPhones by sending malicious links via spam emails, text messages, and social media platforms like Messenger. In these emails, they entice you with the promise of a reward, like a gift you stand to win. They also employ psychological tricks to increase the chances of you falling for their phishing attempts, like pretending to be someone you’re likely to trust, such as a representative from your bank. Getting such emails can help you learn what to look for to avoid falling victim to phishing and, ultimately, spying.
Phishing emails usually have several red flags that make them suspicious. Look out for these telling signs that you’re likely dealing with an email from someone trying to hack you:
- A sense of emergency
- Imitating a brand or organization
- Limited details
- Impersonal (not addressing you by name)
- Grammatical and spelling errors
- Malformed prefixes in the URL
2. Weak passwords
Weak passwords are one of the leading causes of account hacks. Additionally, repeating the same passwords across multiple accounts poses a huge risk to your privacy.
Interesting
A Forbes Advisor study revealed that 35% of respondents believed that using weak passwords was why they were breached. This highlights the risks posed by using passwords that are easy to guess. An example is a password combination containing your name or date of birth. Additionally, 30% of respondents believed that repeating the same passwords across multiple platforms was another reason their accounts were breached. When you do this, you inadvertently give attackers the keys to unlock more of your online accounts, further exposing yourself to data compromises.
Creating weak passwords and using the same passwords across multiple accounts is like handing your sensitive information to attackers on a silver platter. You must use strong and unique passwords if you care about your online security and privacy.
3. Unsecured Wi-Fi
Public Wi-Fi networks are typically easy to breach. Attackers who hack them can see everything that users connected to them are up to on their devices. Therefore, when you use public Wi-Fi networks, you become vulnerable to hacking, which risks your privacy. Instead of using public Wi-Fi, consider using your mobile data, if possible. If that’s not possible, use a VPN service to mask your phone’s IP address, protecting you against spying.
4. Spyware
Your iPhone can be hacked using commercial spyware. Apart from attackers, your loved ones can also use commercial spyware to keep an eye on you. Basic versions are free, offering standard features, while paid or premium versions are more robust, allowing your spy to:
- Access your text messages
- Read your private social media chats
- Monitor your incoming, outgoing, and missed calls
- Track your location
- View your private media, such as photos and videos
- View your keystrokes (to learn your login credentials, banking information, and more)
Spyware is a more sophisticated spying method, as hackers typically need to jailbreak your iPhone to install it. If you notice strange occurrences on your phone, chances are someone is spying on you.
5. Keyloggers
Consider how often you sign in to your banking app or enter your login credentials or other sensitive information on your phone. Imagine how devastating it would be to realize that someone had access to all that information. That’s the danger posed by keyloggers.
Keyloggers are software programs that record all the keystrokes on your phone or computer. Once installed, that data alone can provide hackers with a plethora of sensitive information based on what you type and tap, including your:
- Text conversations
- Login information for your apps and online accounts
- Social Security Number (SSN)
- Search history
- Website visits
Keyloggers also send this data to hackers. By the time you realize your phone is compromised (if you do), the damage could already be extensive. For example, the hacker could have already stolen your identity to defraud other unsuspecting victims or opened credit cards in your name.
6. Hacking your iCloud
iCloud accounts are goldmines for hackers. Once a cybercriminal breaches your iCloud account, they can access, exploit, and steal a host of your data, including:
- Copies of your ID
- Copies of sensitive documents like your marriage certificate, will, business documents, and more
- Private and sometimes compromising photos and videos
- Passwords for your online accounts in your Notes
Good to know
According to IBM’s 2023 Cost of a Data Breach Report, 82% of breaches involved data stored in the cloud and cloud environments were frequent targets for attackers.
The worst part is that attackers can also sell or distribute your data on the dark web, where other cybercriminals can access it and breach your online accounts.
7. Tracking programs
Tracking apps are designed to keep tabs on someone. Unlike spyware, they’re more widely available on official app stores like the App Store and developers’ websites. They are typically parental control apps that parents use to monitor and control their children’s digital activity.
Although parental control apps aren’t inherently malicious, bad actors can exploit them to spy on you. For example, your girlfriend, boyfriend, or spouse can install a parental control app on your phone to monitor your activity. They may be interested in finding out who you talk to, when you communicate with them, how much time you spend on your phone, what websites you visit, and more. If you notice a parental control app on your phone, someone could be using it to monitor your phone and online activity.
What are the signs of your iPhone being hacked
These are the common signs that someone has hacked your iPhone:
- Your battery depletes at an alarming rate
- Your data depletes faster than it normally does
- Your iPhone’s performance starts to deteriorate
- Your friends and family report receiving concerning messages from you
- You are locked out of your Apple ID
- Strange apps appear on your home screen
Here’s why the scenarios listed above should raise your suspicion:
1. Your battery depletes at an alarming rate
A fast-depleting battery is common with older iPhone models. On newer models, it can indicate that something is amiss. It can be caused by an attacker secretly collecting your information from your phone without your knowledge. For example, a hacker can collect your camera data if you grant suspicious app permissions relating to your camera.
2. Your data depletes faster than it normally does
You should know how much data you typically use and how long it lasts. When you notice that your data depletes faster than usual, it can be a red flag that a cyber attacker is stealing your information.
3. Your iPhone’s performance starts to deteriorate
iPhone monitoring apps typically collect your data even when your phone is not in use, like when you’ve put it down. Look out for the phone overheating or displaying signs of being active when not in use, as this can be caused by cyber attackers monitoring you and uploading your data to their servers.
4. Your friends and family report receiving concerning messages from you
Hackers don’t stop their activities after successfully breaching you. They cast their net wide, reaching out to your contacts and anyone in your circle to ensnare them too. Attackers may text your loved ones, asking them for money. However, your loved ones may suspect something is wrong due to the language the hackers use or something they say that gives them away.
5. You are locked out of your Apple ID
One of the first things attackers do is lock victims out of their accounts. As an iPhone user, your attacker may lock you out of your Apple ID to gain full control over your data and prevent you from securing it.
6. Strange apps appear on your home screen
Spying apps allow bad actors to monitor you and gather your information discreetly. Bad actors (people you know included) can install spy apps and parental control apps to watch your every move. Therefore, pay attention to strange apps that suddenly appear on your iPhone that you can’t account for.
What to do if your iPhone has been hacked
It’s important to act fast when you suspect your iPhone has been hacked. Implement the following measures to tighten up your device’s security and prevent the hacker from locking you out of your iPhone:
1. Turn off your iPhone
Disconnect Wi-Fi, Bluetooth, and all accessories, like AirPods, then switch off your phone by long pressing the power button on the side of the device.
2. Remove your phone’s external components
Remove external components such as charging devices, external storage devices, and your SIM card.
3. Lock down your Apple ID
Access your Apple ID from another device, such as your MacBook, and look for suspicious activity on your account.
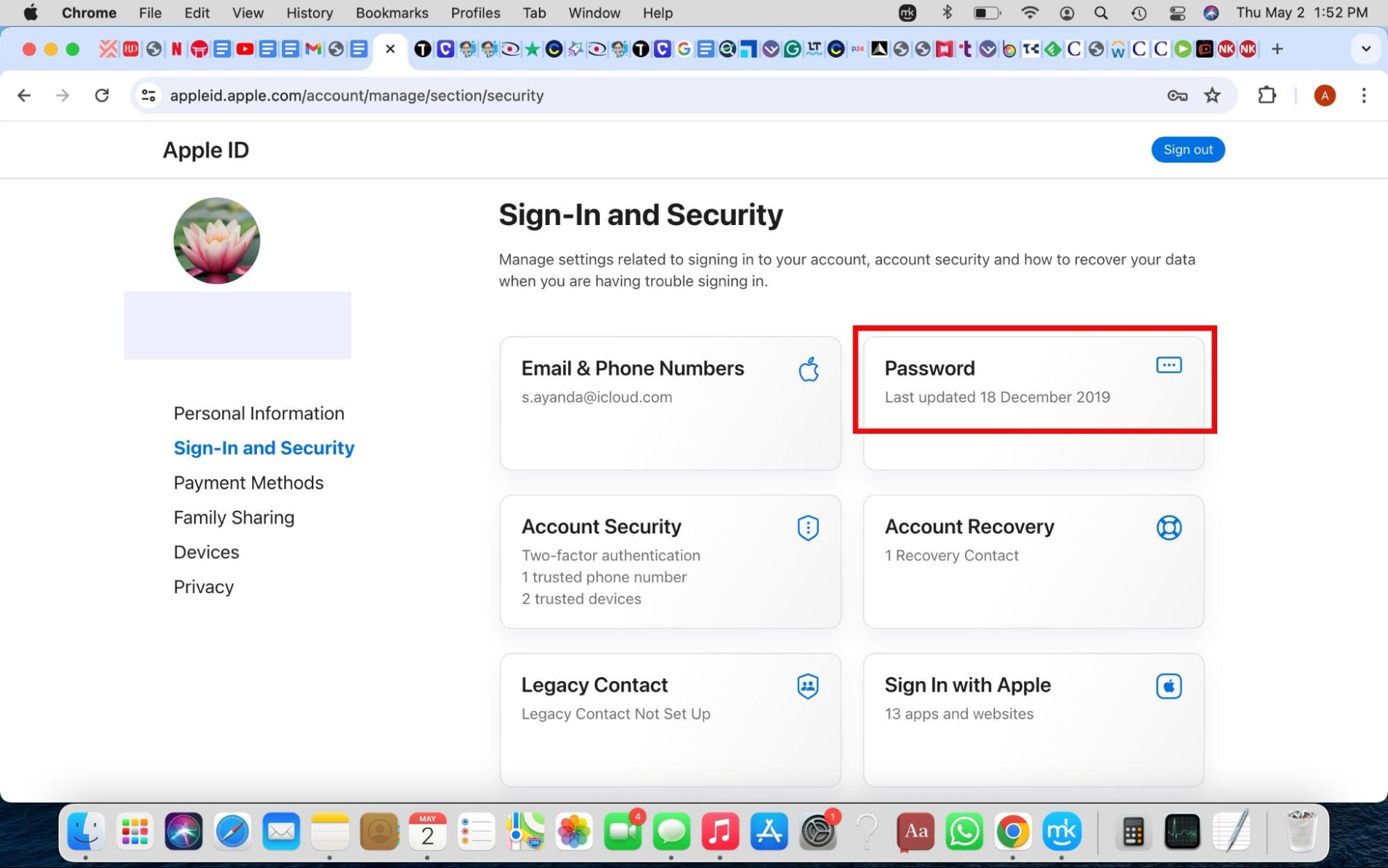
Reset your password to secure your Apple ID. Here’s how:
- Sign in to appleid.apple.com, click Sign-In and Security > Password, and enter a new password.
- Check the box to Sign out of Apple devices and websites associated with your Apple ID.
4. Enable 2FA
Protect your Apple ID by enabling 2FA. This makes it more difficult for hackers to access it. Find the instructions in the Enable 2FA section.
5. Check your phone’s settings
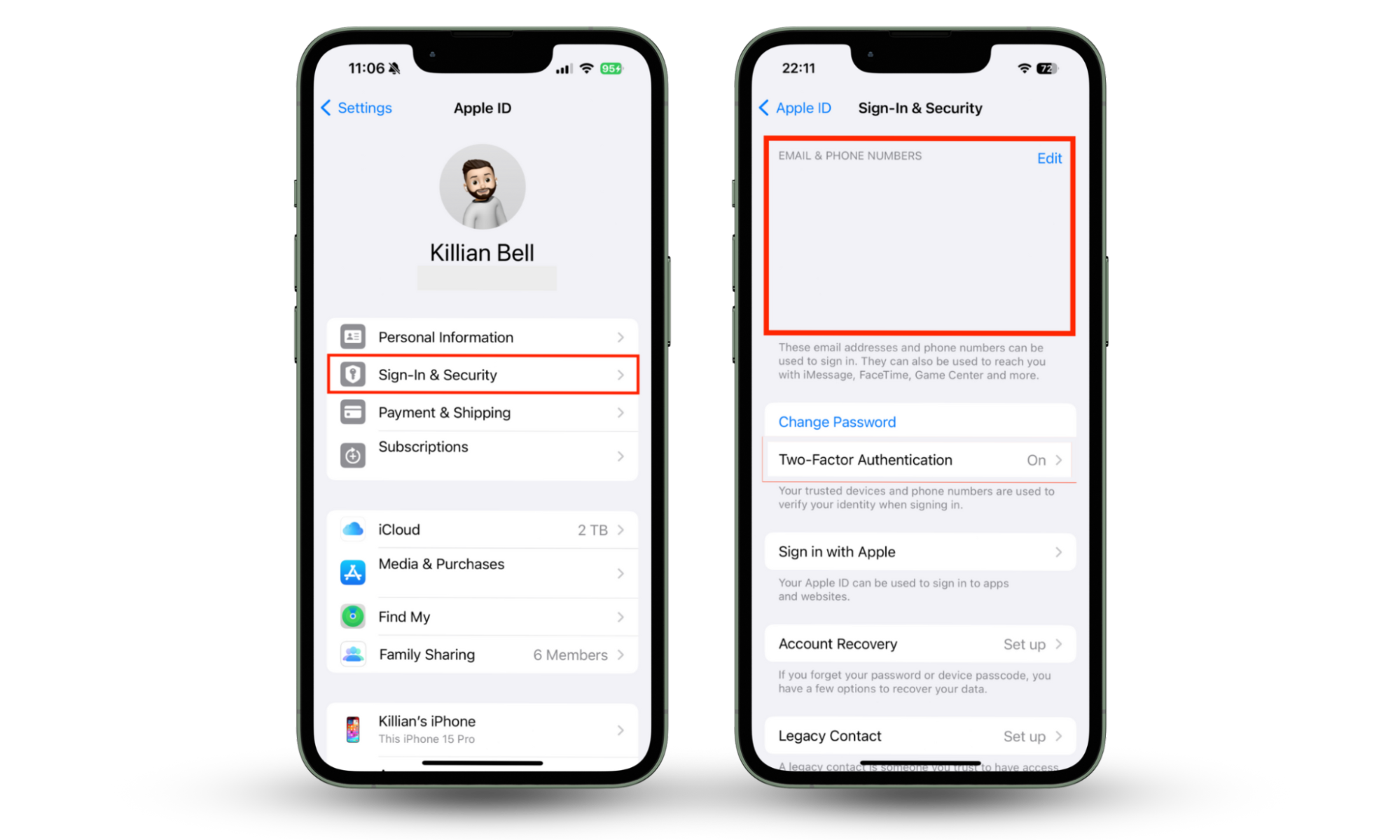
You’re most likely signed into some apps with your Apple ID. As your iPhone can be hacked, attackers can change your Apple ID’s email address to access your social media accounts.
Verify your Apple ID by following these instructions:
- Go to Settings and tap your name > Sign-In & Security.
- Verify your Apple ID in the Email & Phone Numbers section.
6. Call your cellular service provider
Inform your service provider that you were hacked and ask them to check if the hacker made any purchases on your account.
7. Use a VPN service
Find a reliable VPN service that you can use and ensure you keep it enabled as often as possible. Doing this will hide your IP address and personal information from hackers lurking on the internet.
How to protect your iPhone from being hacked
Following the tips listed above won’t prevent your iPhone from being hacked again. Instead, you must proactively protect your device by learning how to secure your iPhone from hackers.
Take this approach to protect your iPhone from hacking:
- Use an anti-spying tool
- Don’t jailbreak your iPhone
- Update iOS regularly
- Use a complex passcode
- Enable 2FA
- Only sync important data
Note that you can’t completely avoid hacking. However, by using the guide below, you can reduce your chances of becoming a victim.
1. Use an anti-spying tool
The key to protecting your personal information is identifying and dealing with threats timeously. In addition to antivirus tools, anti-spying utilities can come in handy. However, not all anti-spying tools are created equal.
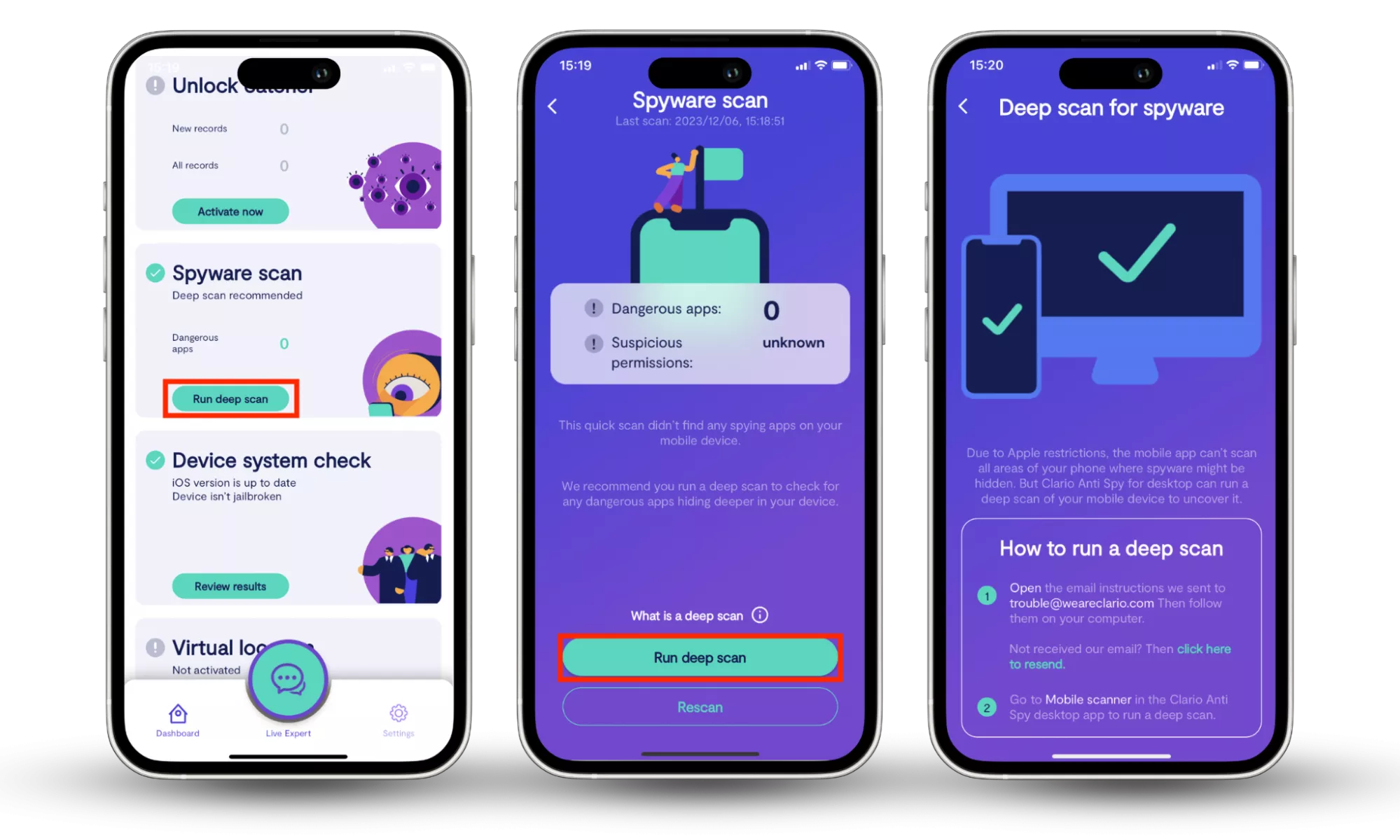
Clario Anti Spy’s Spyware scan is a reliable and effective anti-spying tool that automates the process of finding hidden threats on your iPhone, removing any guesswork on your part. It also empowers you to get rid of the threats it finds and secure your device.
Follow these steps to easily protect your iPhone with Clario Anti Spy’s Spyware scan:
- Download Clario AntiSpy on your iPhone and create an account.
- Hit the Spyware scan and Run deep scan buttons, then give the scan a few moments to check your iPhone.
- Follow the on-screen instructions.
- Review the report and follow the easy instructions to remove any threats Clario AntiSpy identifies.
2. Don’t jailbreak your iPhone
As we’ve previously mentioned, jailbreaking your iPhone strips it of Apple’s built-in security measures, thereby placing it at risk of hacking and spying. Avoid jailbreaking your iPhone to keep it secure and free of threats.
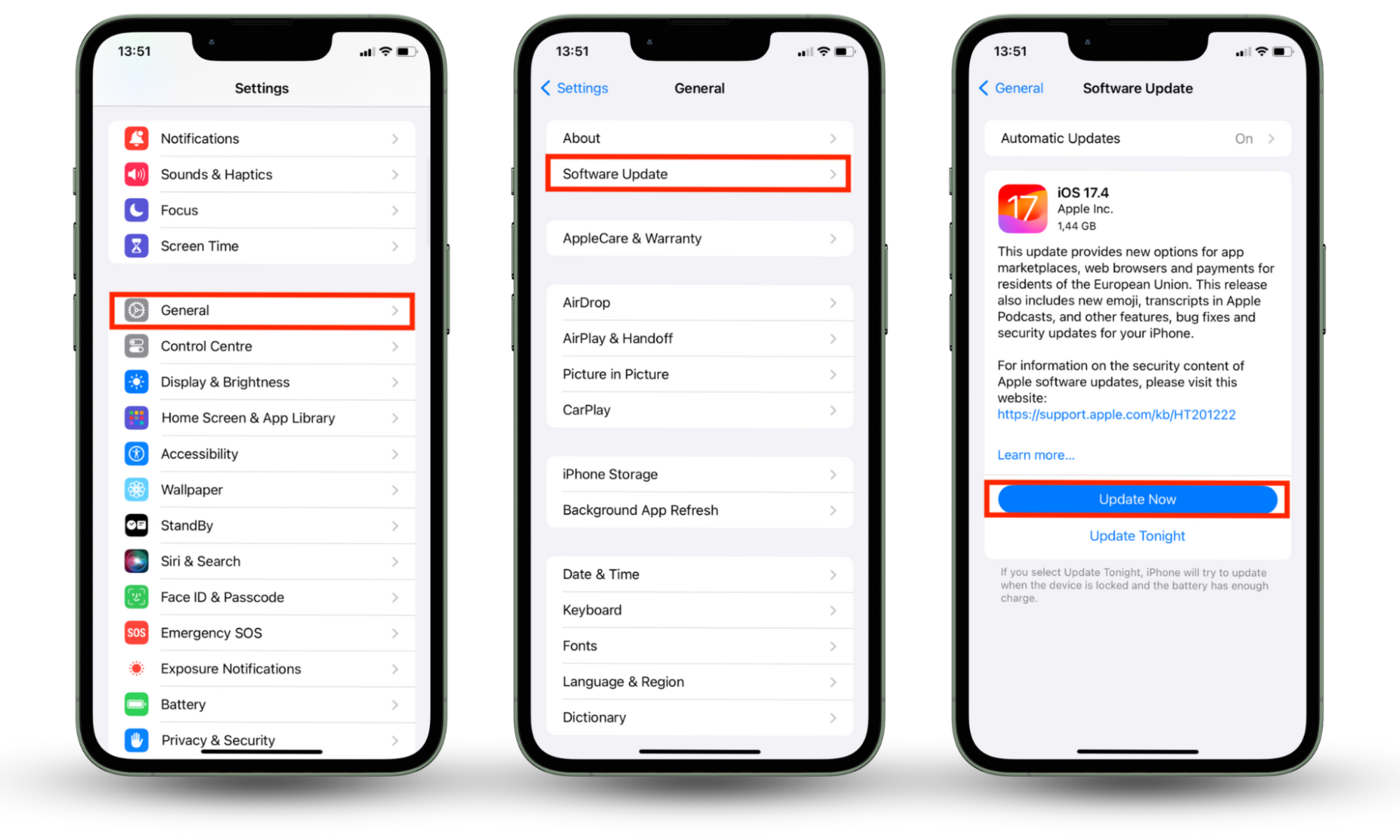
3. Update iOS regularly
Apple releases iOS updates to patch security vulnerabilities. Take advantage of new iOS updates to keep your phone secure and resistant to hacking.
Follow the simple steps below to update iOS:
- Open the Settings app and select General > Software Update.
- If there’s an update available, install it by tapping Install Now or Update Now.
4. Use a complex passcode
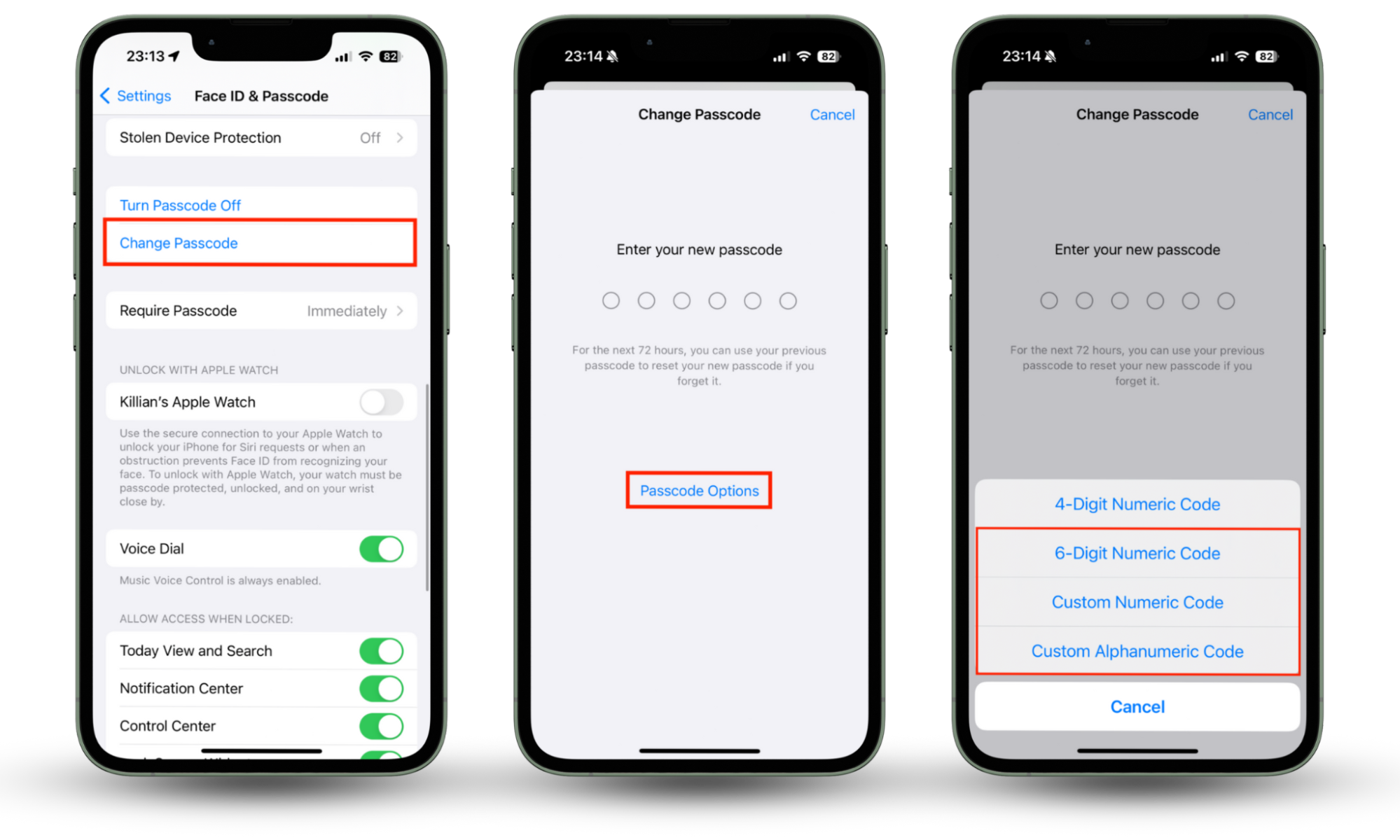
People in your circle or anyone with physical access to your phone can install software to monitor you. Block this from happening in the future by changing your passcode to one that is complex and not easy to guess. Here’s how:
- In the Settings app, choose Touch ID & Passcode or Face ID & Passcode, and enter your current iPhone passcode.
- Tap Change Passcode and re-enter your passcode.
- Select Passcode Options above the keyboard, choose between a Custom Alphanumeric Code, Custom Numeric Code, and a 6-digit Numeric Code (if applicable), enter a complex code, and hit Next to complete the setup.
5. Enable 2FA
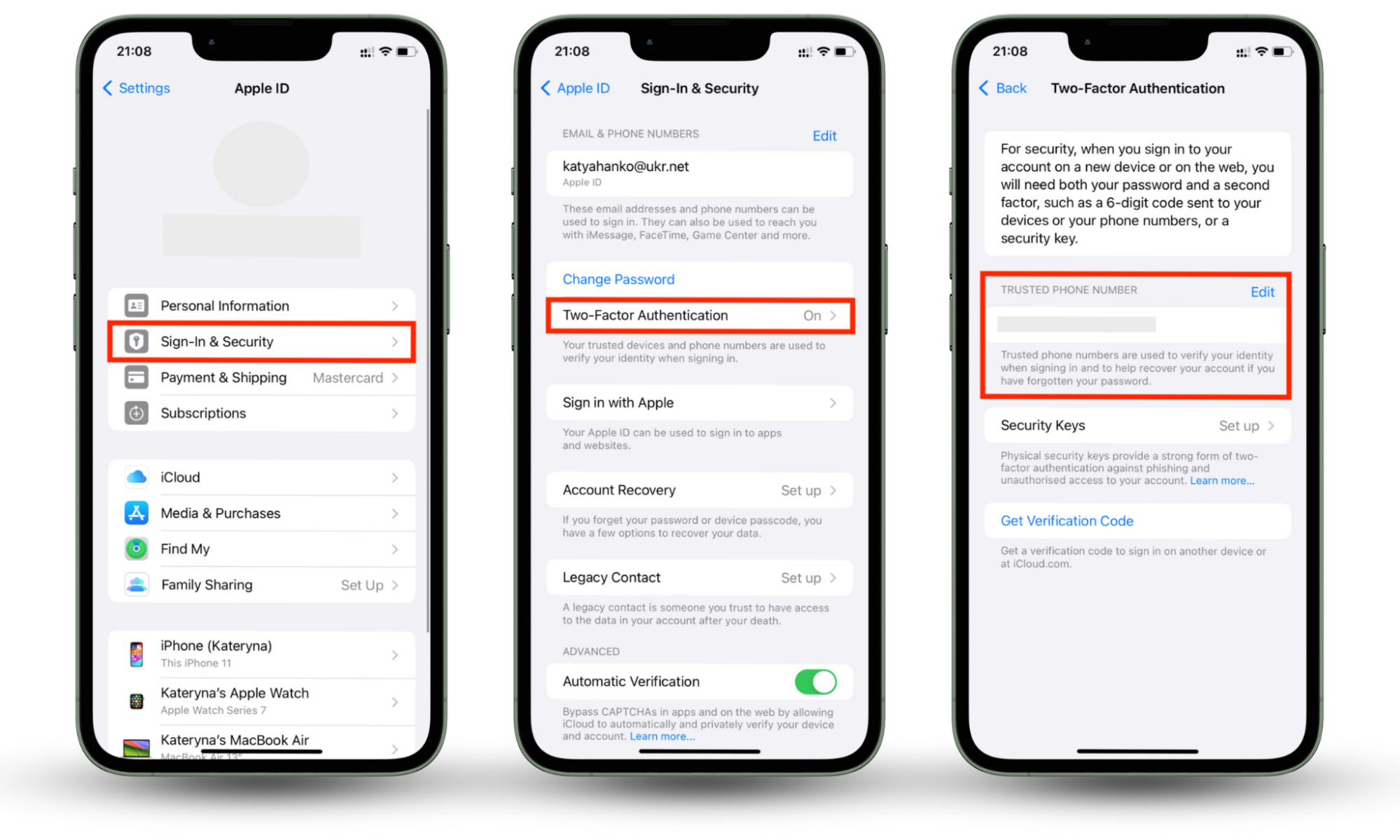
2FA deters hackers from accessing your Apple ID. Enable it to protect your Apple ID with an additional layer of security.
Enable 2FA by following the steps below:
- Open Settings and tap your name > Sign In & Security > Two-Factor Authentication.
- Enter a secure phone number where you want to receive a 2FA code (make sure it’s a phone number you have 24/7 access to) and complete the setup.
6. Only sync important data
Syncing your data to your iCloud account can be a convenient way to manage your iPhone's storage. However, it makes that data vulnerable to theft and exposure by way of hacking. To be safe, don’t sync sensitive data that you wouldn’t want cybercriminals to steal in a hacking incident.
Conclusion
If you think iPhones are safe from hackers, think again, as they are hackable, including when they get lost. Keeping your iPhone in your hand or nearby often doesn’t protect it from hacking. Hackers are cunning, employing various methods to infiltrate your phone and steal sensitive information. This can cost you your dignity and sometimes your money. Knowing the methods by which someone can hack your iPhone is key. Moreover, proactively protecting your phone from hacking can help you avoid becoming a victim.
One of the most effective ways to protect your iPhone from hacking is to use Clario AntiSpy’s Spyware scan. It scans your phone for threats, enabling you to eradicate them promptly, secure your phone, and enjoy peace of mind.


