Table of contents
- Can you get hacked by giving someone your phone number
- Can someone hack into your phone by calling you?
- Can someone hack into your phone by texting you?
- Where can hackers find your phone number
- 1. Via your social media
- 2. Phishing scams
- 3. Confidential information in the mail
- 4. Public Wi-Fi network
- 5. Via Dark Web
- What can hackers do with your phone number
- 1. Redirect your number
- 2. Exploit your data
- 3. Counterfeit your number
- 4. Send you a scam text message
- 5. Impersonate you or send you spyware
- What to do if a scammer has your phone number
- 1. Contact your service provider
- 2. Warn about a hacked number
- 3. Keep evidence of the hack
- 4. Update your contact information
- How to secure your phone number from hackers
- 1. Enable two-factor authentication
- 2. Be careful about your privacy settings
- 3. Install security software
- 4. Protect your SIM card
- 5. Avoid clicking links from unknown senders
- 6. Never call back a number from an unsolicited message
- 7. Keep your phone safe in public
- Conclusion
95% of cyber attacks occur due to human error, which can be as simple as clicking a link in a text message or using an unsecured public Wi-Fi. For example, a phishing link will take you to a fake website asking you to sign into your Google account. If you do, the hacker will access your Google account credentials, thus, your Gmail. And if they have access to your Gmail, they can potentially bypass the two-factor authorization. If this happens, act fast to fix the breach by changing passwords, enabling 2FA, and running a spyware scan. Can your phone be hacked when turned off? In practice, most phone hacks require the device to be powered on, so powering down helps reduce risk.
Read this guide on the dangers of sharing your phone number and the steps to protect yourself from getting hacked.
Can you get hacked by giving someone your phone number
Most times, sharing your phone number is entirely safe. If you are sharing it in ways that you know are safe, with contacts you know are legitimate, you aren’t putting yourself in any danger. However, someone can hack a phone with just a phone number if they have access to it. It is very easy for hackers to contact you under false pretenses and cause you digital harm, like identity theft or financial fraud.
Can someone hack into your phone by calling you?
While hackers can’t hack your phone solely by calling it, there are several ways they can scam you once you answer the call. It usually happens to older people who have less experience in online behavior.
One methodology they may use is pretending to be an organization you trust, like your bank, using automated voice messaging that can seem legitimate. Once they successfully trick you, they can request personal information from you that they will use maliciously.
Another scheme hackers can enact is to use artificial intelligence to record and reproduce your voice or the voice of someone in your family. As deep-fake technology becomes more convincing, voice-cloning can be used to scam money out of people in your contacts list. With a clone of your voice, hackers can call your family and friends, pretending to be you, in need of money.
Tip
One thing you could do to avoid falling victim to scams is never answer calls from these area codes.
Can someone hack into your phone by texting you?
Simply receiving a text from a hacker typically does not pose a danger. As long as you don’t click any links, open any files, or respond to the message, you should be safe.
Links or file attachments may include malware or take you to a scam website. Scammers can retrieve your private data through these schemes, so always remain cautious. Ensure you trust the contact you received the link from and that it’s the link you were expecting. Otherwise, avoid opening any attachments or links from unknown contacts.
Where can hackers find your phone number
While malicious texts and emails are often the processes hackers use to access the data they want, there are also many more you may not even realize. Here are some of the ways that hackers may steal your private information from you:
1. Via your social media
You’ve probably been asked to link your phone number to several social media accounts. Some social media apps, like WhatsApp, require your phone number for registration. Other social media platforms, like Facebook or Instagram, make linking your phone number optional but prompt you to do so for additional security.
While social media platforms may claim that adding your personal contact information is for your own security, it can have the opposite effect. If the social media site had a data breach, your phone number could have been retrieved, sold, or traded online. With more of your private data at their fingertips, you become a more vulnerable target for hackers. Remember, phone numbers get hacked, too.
2. Phishing scams
It can be easy to feel confident that you can decipher fraudulent emails, texts, and calls from trustworthy ones. Yet, phishing scams remain one of the most imminent threats online. Scammers have many ways of tricking you into believing they are a reliable source and requesting your personal information to help you.
These scammers pretend to be authentic contacts from organizations like your bank, insurance company, healthcare provider, or even your favorite online shop. Once they trick you into believing they’re legitimate, they can easily pretend they need your phone number for things like contact info confirmation or purposes like online raffles.
3. Confidential information in the mail
Dedicated and malicious hackers will go as far as they need to steal your sensitive information. Some hackers prefer to keep their data thieving online—but not all. Since they know that most people receive confidential information in the mail, physical targets are still a thing.
Whether this means going through someone’s trash or stealing their mail right off their doorstep—nothing is too extreme for scammers. To ensure your physical confidential info is safe, shred any documents or paperwork you receive in the mail before putting it in trash. You may also consider separating the scraps of paper into different bags or bins to add an extra layer of security.
4. Public Wi-Fi network
Public Wi-Fi networks make you and your data extremely vulnerable. Once a hacker is on a network with you, they can read and steal the information that you put in. For example, while at a cafe connected to their Wi-Fi or at the airport terminal, making a purchase online and typing in your bank account, a hacker can seize that information without your knowledge. Always make sure you use a VPN when using public Wi-Fi.
In the same way, your phone number can get hacked. To prevent hackers from stealing your private information, use incognito tabs when browsing the internet, and do not access websites with sensitive information. Also, do not read data such as your phone number aloud in public spaces to ensure no one is eavesdropping and taking note of what you are saying.
5. Via Dark Web
The dark web is one of the most infamous spaces scammers go to avoid detection of their illegal activities. It is not easily accessible and allows users to be anonymous, which means unlawful activities can run rampant in that space.
Hackers can utilize the dark web to buy, sell, and trade stolen sensitive information. If your password has ever been compromised in a data breach for an account in which you have input personal data such as your phone number, that information has possibly ended up on the dark web.
To prevent your phone number from getting hacked and receive alerts if your private information is involved in a leak, use Clario Anti Spy’s Data breach monitor. The monitor will scan the dark web for your data, let you know if your emails have been found in any known breaches, and guide you in resolving the vulnerabilities.
Here’s how to use Clario Anti Spy’s Data breach monitor:
- Download Clario Anti Spy and get a subscription to create an account.
- Click Scan under the Data breach monitor.
- Type your email in and click Scan.
- If Clario Anti Spy finds any breaches, follow the on-screen instructions to resolve privacy issues.
What can hackers do with your phone number
Once a hacker gains access to your phone number, they can continue in their scheme to access your highly sensitive and important data. Hackers can send you scams through text messages to trick you into giving them more data. They can then impersonate you to log into your online accounts.
They can even reroute your phone number to a new one or counterfeit it. And if you’re wondering, “Can someone track your location with your phone number?”—the answer is yes. They can explore whatever personal data they want. Read on to learn how hackers can use your phone number to hack into your phone.
1. Redirect your number
One option for a hacker to pursue is redirecting your phone number. This means that the hackers would end up receiving all of the text messages and phone calls intended to be sent to your number. If you consider all the content you receive via text messages and phone calls, it’s a jarring thought.
Many people don’t realize that this can be a deliberate request made to their cell phone service provider. The hacker simply calls their service provider and impersonates them, using the personal information they have accessed online.
After a hacker has redirected your phone number, they can:
- Get access to your email accounts: Often, people use their phone numbers to verify their access to email if they’ve forgotten the password. A hacker can simply choose the “Forgot my password” option on the Sign-in page, receive a verification text to the rerouted number, and gain access to your email account.
- Access your social media accounts: Most social media accounts are connected to your email account and/or phone number. When a hacker redirects your phone number and gains access to your email, they can quickly access your social media accounts, too.
- Get access to confidential accounts: Your phone number and email address are likely linked to your bank, insurance, and even government portal accounts. If someone obtains those, they can cause serious financial damage.
2. Exploit your data
Your data is a valuable item that can be sold and traded by malicious individuals and websites. Unfortunately, in today’s world, your data is of high value to ill-intended individuals. Your personal information, preferences, personality traits, and even insecurities are of high value to people's finder sites.
People finder sites, also known as people search sites, are used as a database for people’s private and personal information. This allows hackers to simply input your phone number, and easily access any available online information about you, with a few clicks.
Another way hackers exploit your data is by tracking your phone. This can mean tracking your physical location, your internet activity, or your social media accounts. This would enable hackers to collect more of your private and sensitive data, which they could use for further scams. There are many ways to find out if your phone is being tracked, which can be a helpful preventative measure.
With access to your data, hackers can do what they do best—act maliciously. Whether it is committing identity theft, fraud, extortion, stalking, or further account hacking—hackers can carry out whatever ill-natured offense they desire.
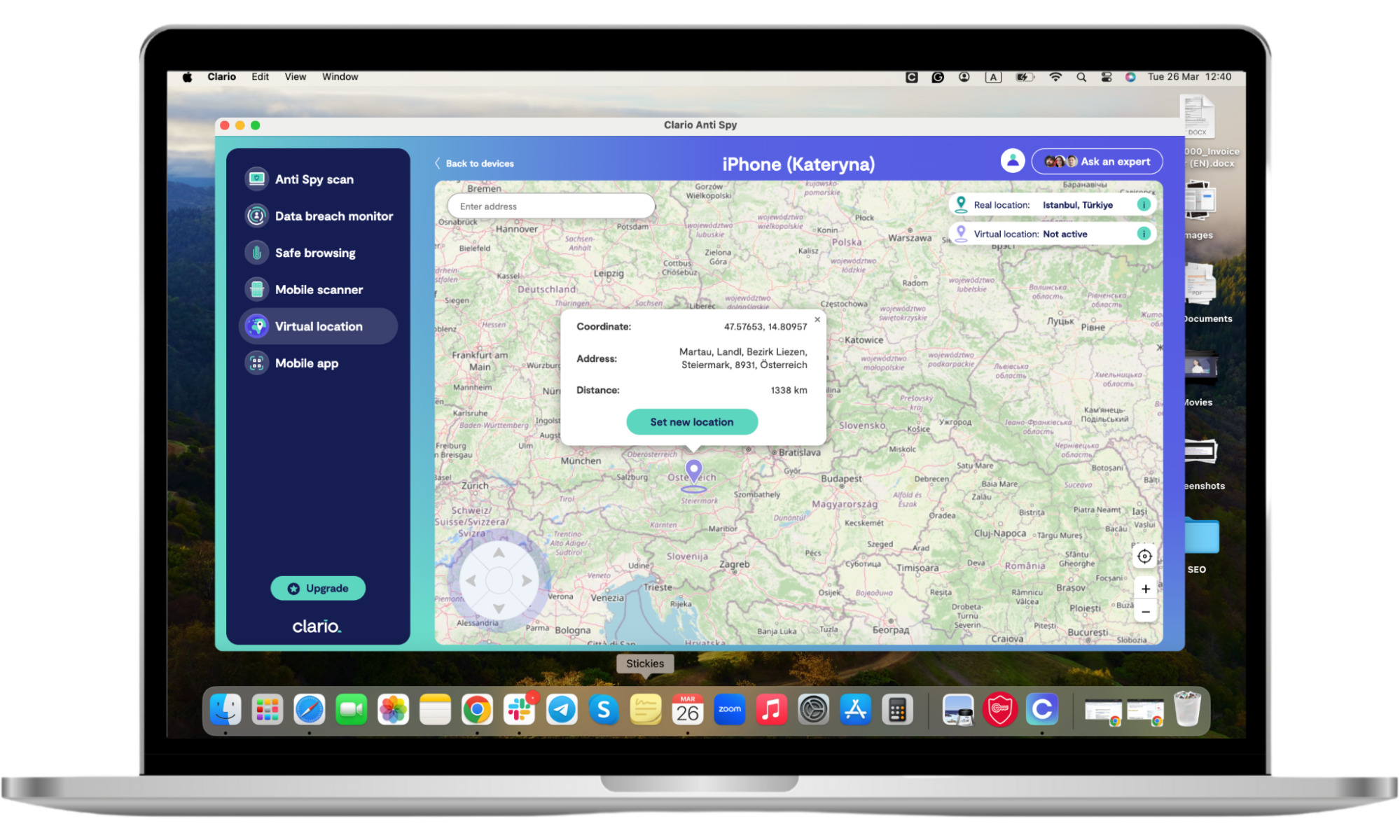
If you suspect someone might be tracking your phone’s location without your consent, you can lead them off the trail and give yourself more time to figure out what this is and how to stop it. Use Clario Anti Spy’s Virtual Location to mask the geo-location your phone is transmitting and set it to any point in the world. You can be in New York, but your phone will be transmitting geo-position in Tokyo or Paris.
Here’s how to use Clario Anti Spy’s Virtual Location feature:
- Download Clario Anti Spy and get a subscription to create an account.
- Click Virtual location.
- Follow the on-screen instructions and connect your phone to your computer.
- Open the desktop version of Clario Anti Spy.
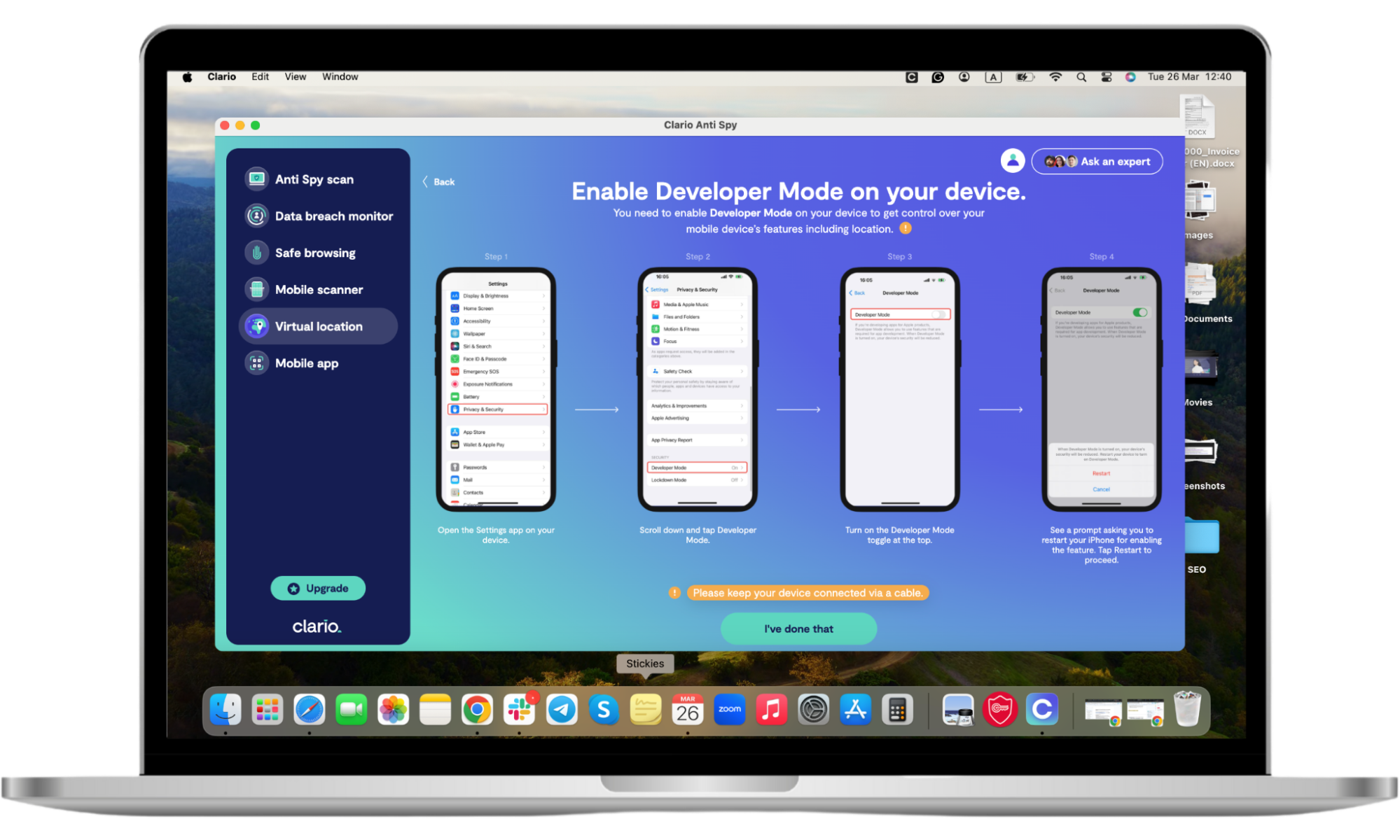
- Click Virtual location and proceed to set your phone into Developer mode.
- Once done, Clario Anti Spy will show you the map, where you can set your virtual location to anywhere in the world.
3. Counterfeit your number
Another scheme hackers can carry out is to counterfeit your number. This means that the scammer can call other phone numbers, pretending it’s your phone number calling them.
This scam typically works when a hacker calls an unsuspecting victim under a stolen number to mask their identity. If the victim answers, the hacker can play any kind of scheme to gain private information from them.
For example, they can call your friends or family members using a clone of your voice. Using deep-fake technology, they can pretend you’re in distress or need money. This high-quality artificial intelligence technology can fool even those who know you best into believing the hackers.
You may wonder how this counterfeiting scheme is possible. Unfortunately, it’s a relatively easy process. The scammer can simply download an app called SpoofCard or go to the VoIP.ms website and make calls using counterfeit numbers within minutes.
If you suspect someone is calling you from a counterfeit number, end the call immediately.
4. Send you a scam text message
Hackers can trick you into providing sensitive information or installing malware onto your device through text messages. While you may feel confident in discerning scams from trustworthy texts, it can only take a momentary lapse of judgment to fall for the scheme.
A hacker may text you pretending to be your doctor, in need of your personal information, like your address. They could provide a link for you to click, which would then take you to a malicious website where you’d be requested to fill in your information. The scam could play out in less than 30 seconds, ending with the hacker achieving their goal.
Or, instead of including a link to a website, the scammer may include a file attachment that downloads malware onto your phone. You may notice that your phone is overheating due to a virus. With the malware installed, the hacker could then steal information stored on your device, charge you for services you did not sign up for, or even jumble up your data and demand payment to reorganize it.
You may have even seen these types of texts before. The pretenses may change, but the scam is the same—get the victim to click a link.
If you receive a text message with a clickable link or file, take precautions before clicking it. For example, you can ask your doctor if they’ve sent you a link. You can also look up the number from which you received the message. Always be careful when it comes to questionable text messages.
5. Impersonate you or send you spyware
Similar to the scam text messages that hackers can send you, they can also send you spyware and even impersonate you using the data they stole. One common type of scam that hackers utilize is the phishing scam.
The scheme starts out the same way as any other scam text message—by sending you a malicious link. This link can contain downloadable spyware that secretly collects all kinds of data from your phone. The hacker then receives this personal and sensitive information.
Hackers can do whatever they choose with such information, including impersonating you. If they gain access to your bank info, they can make purchases under your name. They can impersonate you on social media to target your friends and family. Or, they can even commit identity theft to basically live life pretending to be you.
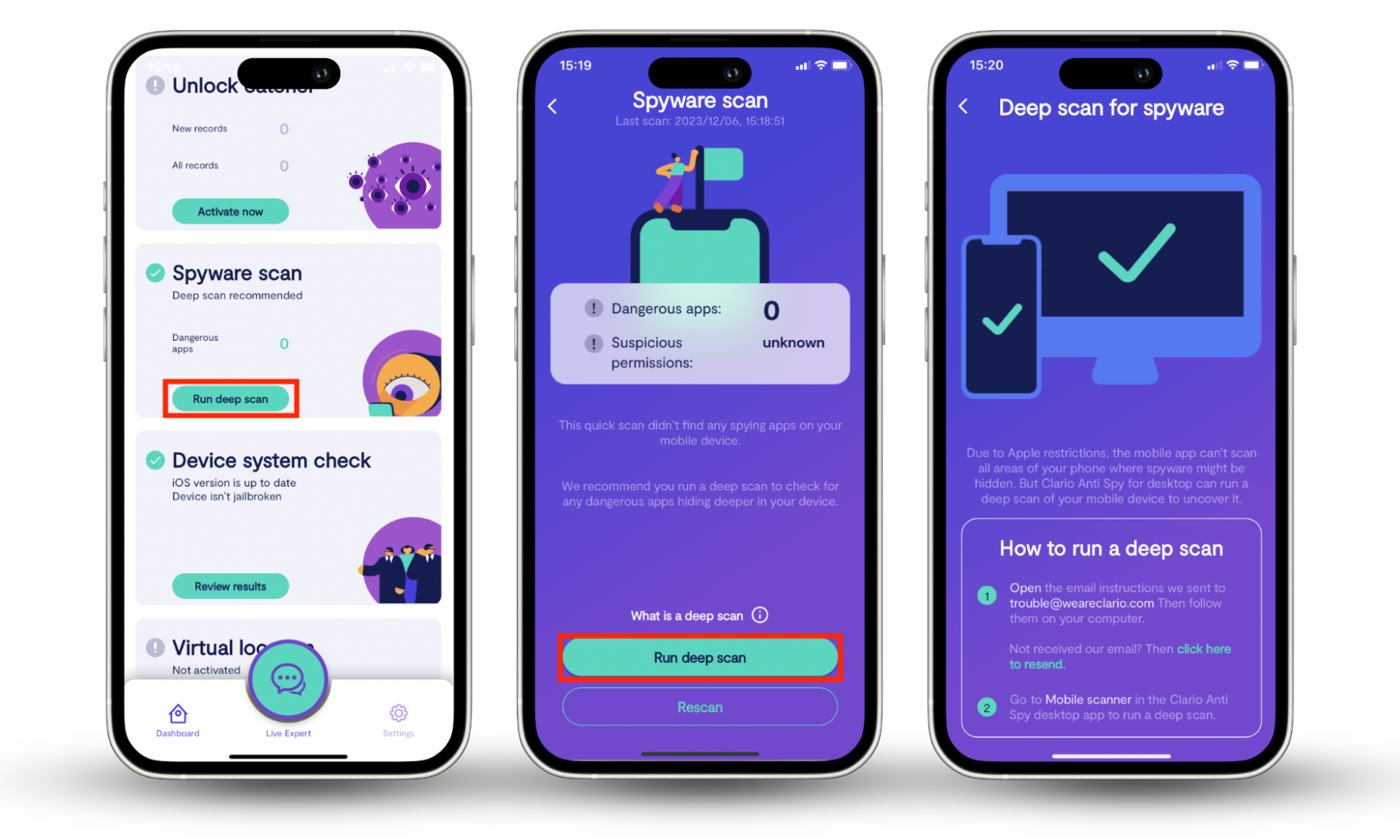
As mentioned above, never click a link that you do not trust. In fact, scanning your phone for spyware is a good idea to ensure you’re not secretly being spied on. You can use Clario Anti Spy’s Spyware scan feature to check for spying or potentially unwanted apps and remove them from your device. This is a key step in cybersecurity. Spyware scan helps ensure your digital safety, all in three easy steps.
Here’s how to use Clario Anti Spy’s Spyware scan:
- Download Clario Anti Spy and get a subscription.
- Click Run deep scan.
- Follow the on-screen instructions to check your device for spyware.
- If Clario Anti Spy finds any sign of spyware on your device, it will guide you through getting rid of it and restoring your privacy.
What to do if a scammer has your phone number
If a scammer has access to your phone number, you may feel entirely helpless. While the situation can feel out of your control, there are steps you can take to regain it.
1. Contact your service provider
Call your mobile phone service provider and let them know the details of your situation. Your service provider needs to know that your phone number has been hacked so that they can help you regain control over it.
They may be able to help in some ways or note it should any further issues occur. Your mobile service provider can also freeze your number, deterring hackers from using your number in their scheme.
Before making any phone calls about the situation, it’s important to know how to check if your phone is tapped or find out who hacked your device. That way, you can ensure it’s safe to discuss your private information on the phone.
2. Warn about a hacked number
It’s just as valuable to inform your friends, family, and colleagues that your phone number has been hacked. Consider sending texts or phone calls to your contact list to inform them of the situation. That way, if they receive any sketchy calls or texts from the number down the line, they’ll know not to partake in the scam.
3. Keep evidence of the hack
Ensure that you keep track of the hack. Here are some ways you can do it:
- Take screenshots, photos, or recordings of evidence that your phone number has been hacked.
- Take screenshots, photos, or recordings of letting your contact list know you’ve been hacked.
- Take a recording of you informing your phone service provider.
- If anyone from your contact list receives a call or text from the hacker under your phone number, ask them to forward you the proof.
- Keep a timeline of the dates and times of each step you’ve taken, as well as each time you know the hacker has used your phone number.
The more details you have about the case, the better. Remember that scammers are engaging in illegal activity under your identity. You need to be able to defend yourself against being held responsible for actions you did not commit.
4. Update your contact information
Ensure all of your accounts have updated contact information. Call your work, school, bank, insurance provider, and any other institution with your compromised phone number listed under your contact information. It’s extremely important that they all receive a new number for you to prevent scammers from stealing any more of your private information. If any of this evidence shows your phone has been compromised, it’s time to take action and remove a hacker from your phone using trusted security tools.
How to secure your phone number from hackers
Scammers can devise an extensive list of schemes using your phone number. Thankfully, there are preventative measures you can take to secure your phone number from those with malicious intentions.
1. Enable two-factor authentication
The first step to protecting yourself from hackers is to enable two-factor authentication for your online accounts. Passwords and usernames can often get compromised relatively easily. Two-factor authentication typically includes inputting your username and password, followed by confirmation of your login attempt via call or text.
Note
The steps for setting up two-factor authentication differ according to the website and account. Ensure you set it up for each account that allows it, including your bank, email, and social media accounts.
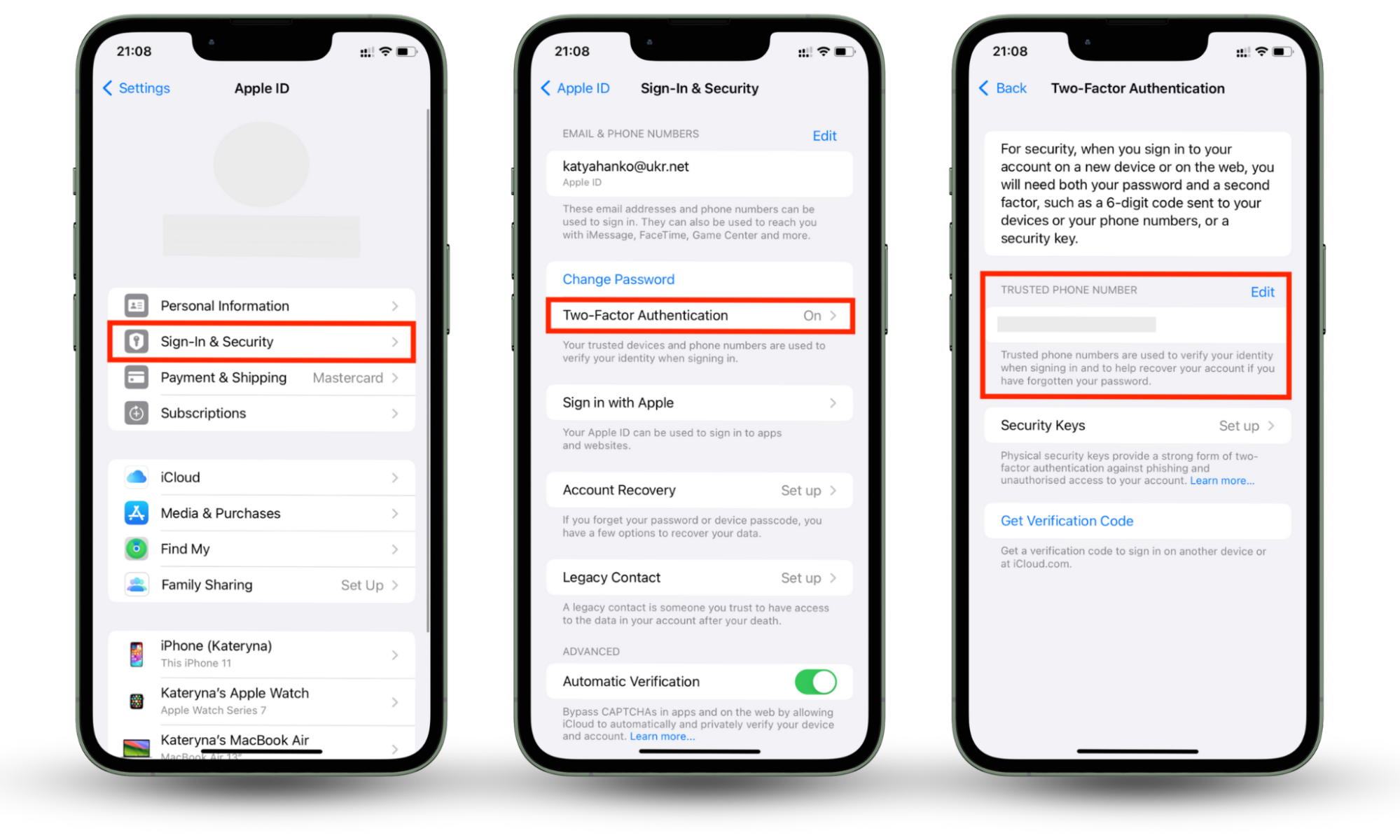
If you have an iPhone, here’s how to set up two-factor authentication for your Apple ID:
- Go to the Settings app and click on your profile picture.
- Select Sign-in & Security.
- Click on Two-Factor Authentication and toggle it on in case it was not activated.
- Choose how you want to receive your authentication code (phone number or email).
- Done!
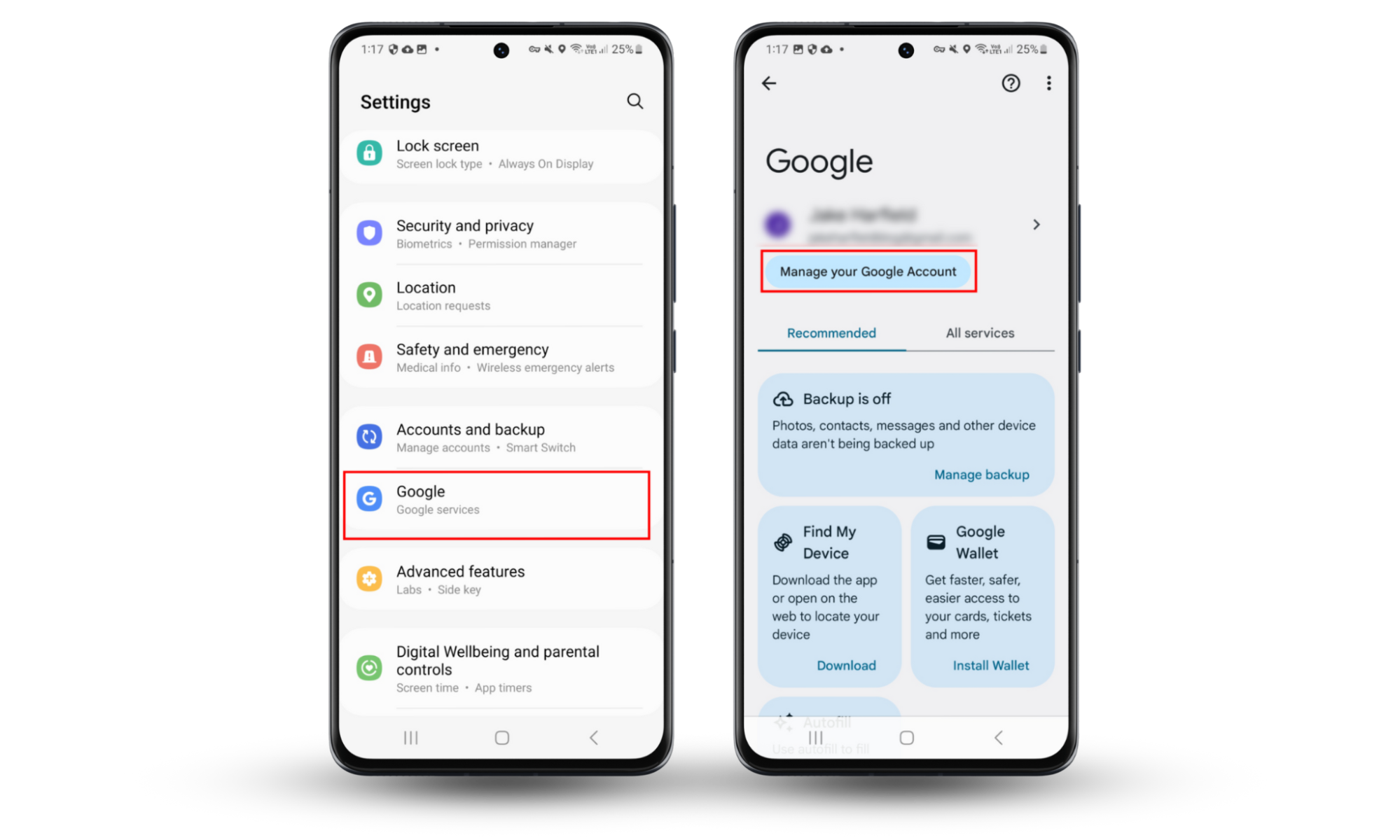
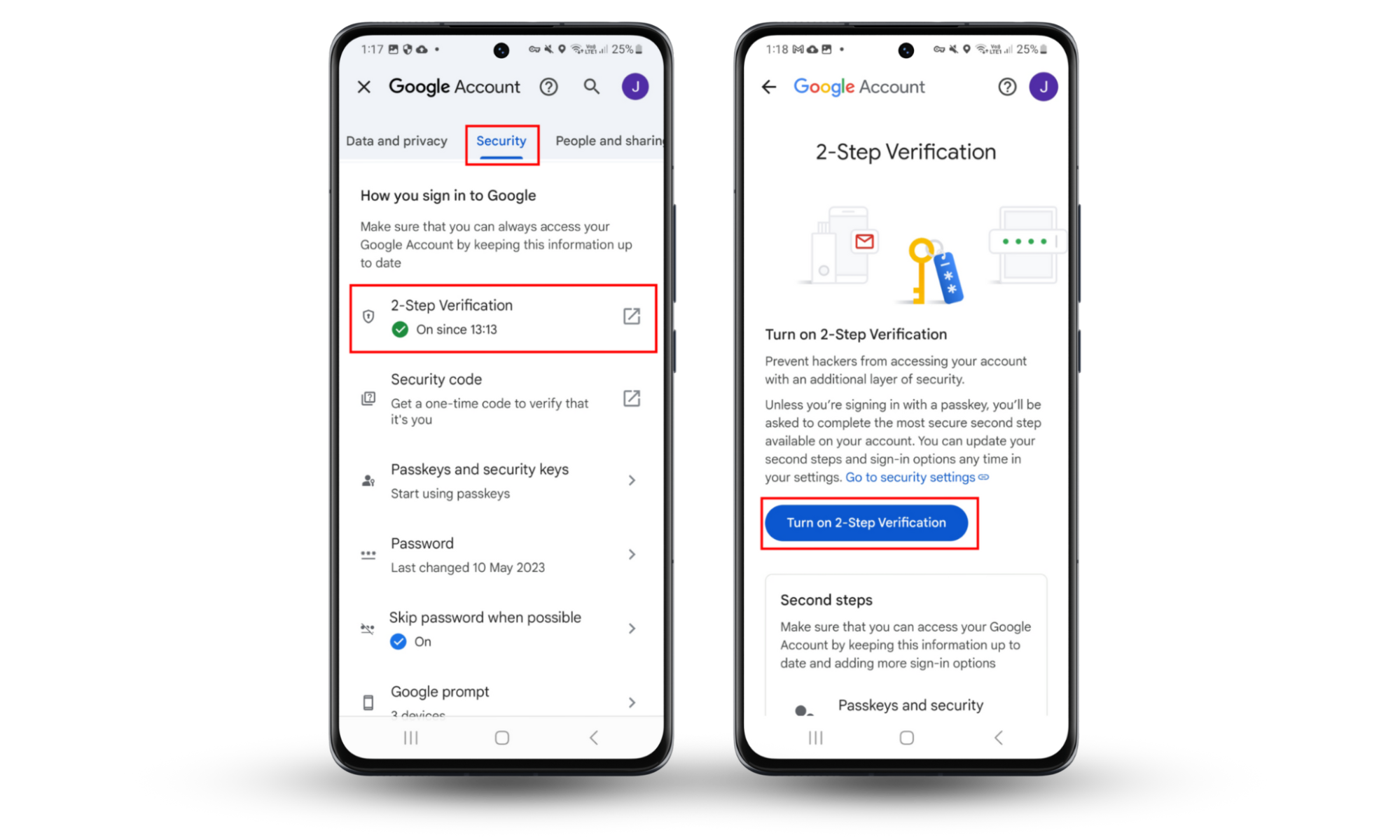
If you are using an Android, follow these steps to set up a two-factor authentication for your Google account:
- Open Settings and tap Google.
- Choose Manage your Google account.
- Press Security, then tap 2-Step Verification.
- Confirm that it’s you, then press Turn on 2-Step Verification.
2. Be careful about your privacy settings
One way that scammers can gather your data is by secretly installing spyware on your phone. That’s why it’s important to consistently check the privacy settings and app permissions on your devices.
To complete a thorough check of your device, use Clario’s Anti-spy setup. The Anti-spy setup feature guides you through a checklist of steps to protect and safeguard your smartphone. By following the steps provided, you can reduce the chance of future threats occurring.
3. Install security software
Another helpful step in securing your device from hackers is installing security software. These apps can help protect you from scammers by detecting suspicious activity on your device.
Clario Anti Spy includes a data breach monitor feature, which alerts you if your information has been leaked online. When you receive a notification about a data breach, you will be instructed to resolve the issue. Clario Anti Spy also includes other device protection features, like Spyware Scan, which checks your device for potentially unwanted or harmful apps, and deletes them.
4. Protect your SIM card
There may be further measures you can take to protect yourself with your mobile phone’s SIM card provider. Often, service providers offer additional steps to secure your account. That may be having to provide a PIN or a password when making changes to your account. Some providers may even include answering authentication questions before they allow you to change any information.
5. Avoid clicking links from unknown senders
As mentioned above, clicking links from unknown senders is never a good idea. It’s better to err on caution before clicking anything you don’t recognize.
Being skeptical of links from known contacts can also be a good idea. Scammers can be extremely effective at pretending to be someone they’re not. Ensure the link you’ve been sent is safe before clicking it.
6. Never call back a number from an unsolicited message
Just as you should not trust unsolicited links, neither should you trust call prompts from numbers you do not recognize. Hackers can pretend to be trusted contacts, such as your bank, and request that you call them.
When you call a hacker’s phone number, they can trick you into providing private information. This may not be evidently suspicious on the surface. For example, the scammer can play automated recordings of yes-or-no questions, which can fool many unsuspecting people.
Once a hacker successfully tricks you into their scam, they can tap your phone. If you suspect your phone has been tapped, see codes to check if your phone is monitored, and remember to be wary of unsolicited messages you receive in the future.
7. Keep your phone safe in public
Ensure that you are aware of where your phone is at all times. Do not leave it unaccompanied or out of sight. Scammers can also target you in person.
Set up strong security measures to prevent a hacker from accessing your data using your phone. Use strong passwords or PINs, and set up biometric identification to lock your phone more securely.
Conclusion
As mentioned above, hackers are able to gain access to your phone number in various ways, including your social media, through public Wi-Fi, or even via the dark web. While it’s a scary thought that malicious individuals can access your number, it’s important to note that they cannot hack you solely by calling or texting you. The hacking is only successful if you fall for their tricks and click untrustworthy links or provide your personal information.
With the Spyware scan feature in Clario Anti Spy, you can feel confident that no spyware apps are causing you digital harm. Spyware scan will find potentially unwanted or harmful apps and wipe them from your device. Download Clario Anti Spy today and take your digital power back.


