Table of contents
- What are endpoint devices?
- Why endpoint security matters
- Is antivirus enough for good endpoint security?
- How system endpoint protection works
- Types of endpoint security
- Password
- Antivirus
- IoT security
- URL filtering
- Network access control
- Conclusion
We bet you think endpoint security is something techy and complicated. But really, it’s just a simple way you can protect all your devices that are connected to the internet. Yes, it’s as easy as that.
Why are we talking about it now? Well, with the global shift to working from home, the need for endpoint security is stronger than ever. Opportunities for a cyberattack can now come from everywhere: your Mac, iPad, even a smart speaker.
But, while it might sound like a tall order, endpoint security isn’t too hard to achieve. In this guide, we’ll tell you how to organize your personal endpoint security and why you need more than just antivirus software alone to stay safe.
Definition
In simple terms, endpoint security means protecting every device that connects to the internet. This includes laptops, smartphones, tablets, and smart home devices. Unlike antivirus software, which mainly focuses on detecting known malware, endpoint security takes a broader approach by helping prevent unauthorized access, data leaks, phishing attacks, and other threats that target connected devices.
What are endpoint devices?
Endpoint definition is simple: all laptops, tablets, smartphones, IoT devices, servers, and workstations that are the ‘end points’ of a network are endpoint devices. This includes hundreds of corporate computers or just your personal MacBook, Apple Watch, and iPhone.
Endpoint devices generally fall into a few broad categories:
- Personal devices: laptops, smartphones, tablets, smartwatches
- Work-related devices: company-issued laptops, remote workstations, external drives
- IoT and smart home devices: smart speakers, security cameras, routers, smart TVs
Each of these devices connects to the internet in a different way, but all of them can be targeted by cybercriminals if left unsecured.
Why endpoint security matters
You can just ask thousands of endpoint cyberattack victims the same question. Endpoint security failures often start with just one device, but the consequences can quickly spread across entire organizations or expose massive amounts of personal and business data.
- SolarWinds was compromised through a Trojan, putting Fortune 500 companies and 40+ US government agencies in danger, including the National Nuclear Security Administration (NNSA)
- Verifications.io didn’t properly secure its cloud endpoints, exposing a database of two 808 billion records with personally identifiable information and sensitive business information
- Acer suffered a ransomware attack, with cybercriminals demanding a $50 million ransom
These incidents highlight a common pattern:
- A single compromised endpoint can expose thousands, or even billions, of records
- Attackers often use endpoints as an entry point to move deeper into networks
While large organizations are frequent targets, the same techniques are used against individual users with multiple connected devices.
It is usually large corporations that suffer from endpoint security breaches. However, you should remember that the more devices you have, the more endpoints are available for hackers. Be sure, they’re going to use the opportunity to attack you, even if you’re not a Forbes 500 company.
Oh, you have an antivirus installed on your Mac? That’s great. But you shouldn’t rely on antivirus alone to protect your endpoint.
Is antivirus enough for good endpoint security?
Antivirus is used for protecting individual devices from malware to ensure safer web browsing. But it’s not always enough. Some antiviruses are ineffective when it comes to tracking ransomware (viruses that may take your information hostage). Others can hardly protect you from identity theft or sophisticated scammers. Plus, guarding your endpoint is a joint effort: an antivirus is an important tool, but it’s not the only one.
In practice, antivirus software is designed to handle only part of the problem:
- It mainly detects and removes known malware after it reaches a device
- It offers limited protection against phishing, identity theft, and account takeover
- It may not stop attacks that exploit user behavior or unsecured network access
Endpoint security addresses these gaps by combining multiple protection layers across devices.
Endpoint security tools are all-encompassing. They include access control, data encryption, attack detection, user authentication, and much more. Together, they protect your privacy from ID theft, leaks of sensitive data, and even save you from money loss. Antivirus alone would hardly be able to cope with all of these responsibilities.
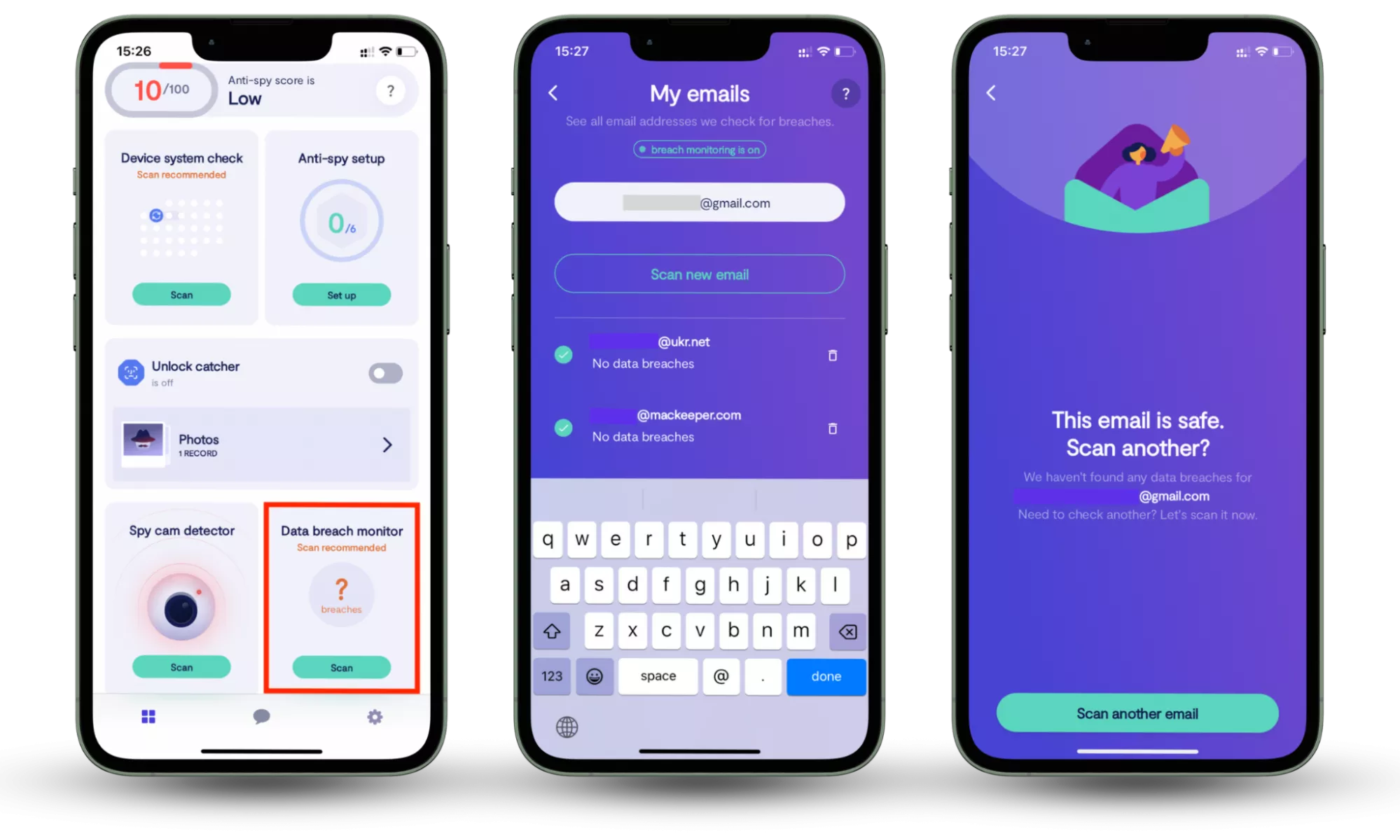
For example, if your email or online accounts have already been exposed in a data breach, antivirus software won’t alert you. Clario Anti Spy’s Data breach monitor checks whether your accounts are accessible to unauthorized parties and notifies you if your data appears in a breach, helping you secure compromised endpoints before further damage occurs.
How to check whether your information is compromised:
- Download Clario Anti Spy and subscribe.
- Open the app, and, under Data breach monitor, tap Scan.
- Enter your email address.
- When the scan is complete, follow the on-screen guidance to review any data breaches.
- Repeat the process for any other email addresses.
Once compromised, an endpoint (whatever device it may be) opens the door for cybercriminals. But it doesn't mean you are unable to stop them. Let’s see how you can.
How system endpoint protection works
Corporate protection is an excellent example of organizing endpoint security. System administrators monitor the state of every computer or phone connected to the corporate network. They watch out for any suspicious activity in corporate emails and urgently block access in case of phishing attempts.
While home users don’t have dedicated IT teams, the same principles apply: monitoring device activity, limiting access, and responding quickly to suspicious behavior.
But you don’t have a system administrator at home, do you? Here’s what average domestic users can do to stay safe.
Types of endpoint security
Your personal endpoint protection might include antivirus, data breach monitoring, or instant blocking of suspicious web pages. Plus, a well-tailored security tool can prevent you and your family from accidentally installing malware. Let’s give all these approaches a closer look.
The following security measures work together to reduce the most common risks facing personal endpoint devices.
Password
Okay, so the first thing you can do to secure your endpoint devices is to set up a strong password, passcode, or passphrase. Yes, you’re probably tired of repeatedly hearing about how critical strong passwords are, but it’s the first thing any of us should set up to ensure the basic level of protection. Endpoint devices are usually portable, and it’s easy to misplace them. Without a password on your device, anyone — be it a criminal or your younger sister — can access its files. And in some ways, we don’t know what’s worse.
For stronger protection of endpoint devices, passwords should follow a few basic rules:
- Use long passphrases instead of short or reused passwords
- Avoid using the same password across multiple devices or accounts
- Enable biometric authentication or device-level encryption where available
Antivirus
This is a common tool for digital protection, and every household should have one. Antivirus is your shield against malware, adware, and phishing. It also checks incoming files for potential threats. If something in your email or browser is suspicious, high-quality antivirus software will let you know or even deal with the trouble right away.
IoT security
Remember that every device connected to the internet may serve as an entry point for cybercriminals. This includes your home security camera, Amazon Echo, or even a portable Bluetooth speaker. The Internet of Things (IoT) increased the number of endpoint devices requiring security. And this means you need to protect them by being cautious, not doing anything suspicious that the device (and hackers behind it) tells you to, and setting up an antivirus on them (if you can).
URL filtering
Installing URL filtering software or browser extensions is another way to protect your endpoint. These tools monitor URLs and block access to or warn users about potential threats when they’re about to visit a web page. URL filtering is great for protection from phishing — this is one of the most widespread types of cyberattacks, when a malicious web page is designed to resemble a credible one (of a bank or payment system) to trick you into disclosing your credentials.
URL filtering tools typically work in a few steps:
- The website address is checked against databases of known malicious or suspicious URLs
- The page is analyzed for phishing patterns, malware, or fraudulent behavior
- Access is blocked or a warning is shown before any data can be entered
Network access control
This type of security measure checks who can or cannot enter the system. For a company, it might mean only enabling remote access to the corporate resources for employees. For a regular user, this protection is mainly known as a firewall — a set of tools checking the web traffic for safety and making a device invisible for a hacker.
Conclusion
As you can see, maintaining endpoint security isn’t hard. It simply requires following your general digital hygiene rules and using endpoint protection software like a decent antivirus. But remember: no antivirus will save you if you’re not serious about endpoint security, so be careful and learn as much as you can about cybersecurity from our blog.
Taken together, effective endpoint security comes down to a few essentials:
- Every internet-connected device is a potential target
- Antivirus software alone cannot cover all modern threats
- Combining multiple security measures significantly reduces risk
Another important part of endpoint security is knowing whether your accounts have already been exposed. Clario Anti Spy’s Data breach monitor helps identify if email addresses linked to your devices appear in known data breaches, alerting you so you can secure affected accounts. This kind of visibility helps reduce the risk of unauthorized access spreading across your connected devices.
Read more:


