Table of contents
- VPN encryption in a nutshell
- Different types of VPNs you can use
- Standalone VPNs
- Browser extensions
- Router VPNs
- Corporate VPNs
- How secure is a VPN connection?
- Encryption strength
- Terms of VPN service
- Laws and jurisdictions of your country of residence
- Laws and jurisdictions of the VPN country of registration
- Types of VPN encryption protocols
- Conclusion
VPN encryption in a nutshell
VPN stands for Virtual Private Network. It means your computer becomes part of a virtual network and connects to the internet via a private connection rather than through your ISP’s (Internet Service Provider) servers. It lets you browse the internet privately by encrypting your outgoing data and disabling anyone from associating your IP address with your online activity.
But how does a VPN protect you exactly? Whether you access the internet using a VPN extension for a browser, a corporate VPN solution, a VPN feature on a router, or any other VPN type, here’s how a VPN works:
- The VPN tool creates a private tunnel to the VPN provider’s servers.
- The VPN tool uses a cipher to encrypt your data.
- Your device’s IP address is hidden by being encrypted. For anyone outside your VPN, your IP address is one of your VPN provider’s addresses.
- Your device and the VPN server issue a key to decrypt the data.
- The encrypted data is transferred to the destination server.
- The response passes back to the VPN provider’s servers. They then reroute it to your device through a VPN tunnel.
- The data is decrypted and you can access the internet safely.
Now, let’s take a closer look at various VPN types.
Different types of VPNs you can use
Depending on the devices you need to protect and your goals for applying VPN tools, there are several VPN types you could use.
Standalone VPNs
This is a perfect solution for individuals or small businesses. A standalone VPN is an app installed on your device to create a secure internet connection upon launch. There are usually different versions, so you will need to set up a VPN on Mac, Android, or iPhone.
Browser extensions
There are thousands of VPN browser extensions for Chrome, Firefox, and Safari. The Opera browser even has a VPN built-in. Unfortunately, it works only when using the browser with the extension installed. Plus, we advise you to avoid free VPN extensions as these are often nothing more than data collectors for shady operations.
Router VPNs
An excellent solution for smart homes and ecosystems of interconnected devices, these VPN tools come pre-installed with some router models. Once you sign up for a VPN service and install the required software on your router, this type of VPN protects all connected devices.
Corporate VPNs
These are custom-configured VPN tools managed (and sometimes built) by the in-house IT team of a particular company. They ensure employees can access corporate files and the software they need when working from home or on a business trip without compromising data security.
Need more info?
Now you know about the various types of VPN, it’s time to learn what makes them secure.
How secure is a VPN connection?
Securing financial transactions is one of the primary reasons for using a VPN solution. This is why enabling VPN encryption when using public Wi-Fi networks is a must. However, the actual degree of protection provided by a VPN depends on multiple factors:
- encryption strength
- terms of VPN service
- laws and jurisdictions of your country of residence
- laws and jurisdictions of the VPN country of registration
Below are each of these factors in detail.
Encryption strength
The strength of VPN encryption relies on the key length. Without going into too much detail, the longer the key length, the harder it is to be deciphered by cybercriminals. The first keys were 128-bit-long, now 256-bit-long keys are the gold standard. These can’t be cracked with brute force as it would take billions of years—yes, literally billions!—to go through all the possible combinations of bits.
There are also various types of ciphers—formulas used to encrypt the data:
- AES or Advanced Encryption Standard, instated by the US National Institute of Standards and Technology (NIST) in 2001. AES-256 is the basis for most contemporary VPN solutions.
- Blowfish, the default VPN algorithm for OpenVPN, is an open-source initiative used by the majority of commercial VPN providers. This algorithm is widely configurable, quite secure, and compliant with most devices.
- Camelia is an alternative to AES, but not certified by NIST. However, if compliance isn’t essential to you, Camelia can be used without any negative consequences.
Terms of VPN service
Every business has to monetize its services somehow. The most common approach for VPN providers is logging the customer’s actions to get aggregated data for analysis—or providing no-logging VPN for paid subscriptions.
Laws and jurisdictions of your country of residence
In many countries, VPN usage is expressly prohibited or should be regulated by special jurisdiction. For example, Chinese government regulates and oversees VPN usage by companies. There also are various limitations in Russia, Belarus, Iran, and other authoritarian countries. However, in most Western states you can freely use VPN encryption to protect your browsing experience from prying eyes.
Laws and jurisdictions of the VPN country of registration
VPN providers are businesses, meaning they are registered somewhere, pay taxes there, and should comply with the appropriate legislation. This also means if they receive an order from a court of law to provide data on your internet usage history, they will have to comply. Therefore, if what you’re doing online can get you in trouble, it’s best to use the Tor browser instead of a VPN.
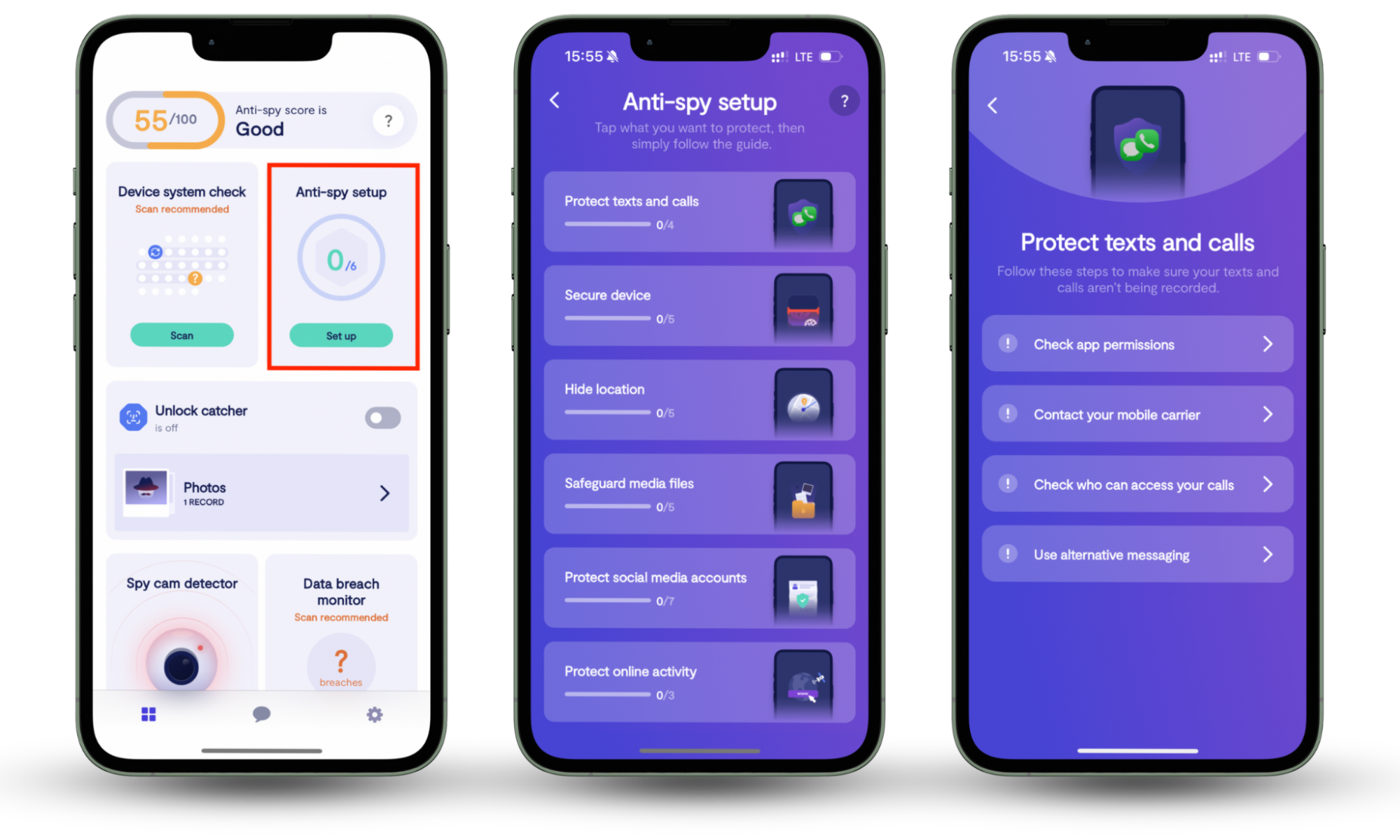
No matter how secure your VPN is, your privacy and security can still be at risk if you neglect important settings on your iPhone or Android. This is where Clario Anti Spy steps in. With its Anti-spy setup, it quickly helps patch security vulnerabilities and protects your device from spyware, online tracking, and stalking.
Here's how to run an Anti-spy setup with Clario Anti Spy:
- Download Clario Anti Spy and subscribe to create an account.
- Tap Set up under Anti-spy setup.
- Work through each category—Protect online activity, Secure device, Safeguard media files, etc.—to enhance your device's security.
Clario Anti Spy also keeps your device secure in other ways. For instance, it can warn you about hidden jailbreak exploits, alert you about data breaches, and provide expert support 24/7 for security issues.
Types of VPN encryption protocols
Now, let’s briefly overview the types of VPN encryption protocols. These protocols determine how data is transferred back and forth between the Internet and your device:
- Point-to-Point-Tunneling Protocol (PPTP). This is one of the oldest VPN protocols developed by Microsoft. It is simple to use and quick to deploy. Many legacy systems still use it, but it’s not recommended for newer solutions.
- Secure Socket Tunnelling Protocol (SSTP). A more modern Microsoft VPN tool, this uses 256-bit encryption and can circumvent most firewalls. It is pretty secure, as only the two parties involved in the exchange can decode the data, making you immune to the man-in-the-middle attacks.
- Level 2 Tunneling Protocol (L2TP). It is a PPTP-based protected data tunnel protocol from Cisco, yet it lacks security management features. This is why it’s always bundled with the IPSec protocol.
- Internet Key Exchange v2 (IKEv2). This is a product of Microsoft and Cisco’s collaboration — a lightweight security protocol used to protect mobile devices. It is also bundled with IPSec and is currently the gold standard for mobility protection.
- OpenVPN. It is an open-source project aimed at building a better and more secure web for all. Backed by a strong community of developers and providing excellent protection, this protocol is the de-facto standard for all modern VPN tools.
You can’t change your VPN encryption protocols, so understanding the purposes they serve is essential to protect your devices appropriately.
Want to learn more?
Conclusion
Now you know how a VPN works, how secure VPNs really are, and the types of VPN encryption you can use. For best results, combine your VPN with Clario Anti Spy—this anti-spyware utility helps you quickly patch out any vulnerabilities you might otherwise overlook.


