Table of contents
- Signs someone is spying on your computer
- Battery drains too fast
- Computer often overheats
- Apps are acting up
- Slow speeds
- Webcam is recording without your permission
- Erratically flashing lights
- Strange and frequent pop-ups on your desktop
- Sudden homepage change
- Browser keeps redirecting
- Unknown programs installed on the computer
- Suspicious browser activity
- Ransomware attack message
- The task manager or activity monitor is disabled
- Programs start randomly
- How to detect and remove spyware on your computer?
- Check for suspicious processes through Task Manager
- Use a trusted antivirus
- View active internet connections
- Watch for open ports
- Format your hard drive
- How to protect your computer from spying
- Install an antivirus program
- Download software only from trusted sources
- Update your system regularly
- Avoid suspicious websites
- Use а VPN
- Use complex passwords
- Be suspicious of strangers
- Don’t open emails from unknown senders
- Scan your system regularly for viruses
- Be attentive to antivirus notifications
- Is someone spying on your computer?
Signs someone is spying on your computer
Though it’s difficult to always know if someone is spying on your computer, there are telltale signs. Spyware and other forms of malware almost always affect your hardware, leading to poor device and app performance or just generally strange behavior.
Here are the signs someone is spying on your computer:
- Laptop battery drains too fast
- Computer often overheats
- Apps are acting up
- Slow speeds
- Webcam is recording without your permission
- Erratically flashing lights
- Strange and frequent pop-ups on your desktop
- Sudden homepage change
- Browser keeps redirecting
- Unknown programs installed on your computer
- Suspicious browser activity
- Ransomware attack message
- The task manager or activity monitor is disabled
- Programs start randomly
Now let’s unpack these spying signs:
Battery drains too fast
If you notice a considerable difference in your device’s battery life, it could hint at spying. Background spying apps and processes can drain your battery. But a quickly draining battery could also be due to your own personal device usage or a device that’s getting older. Be sure to rule out those factors first.
Computer often overheats
An overheating computer deals with more computing activity than it can handle—and possibly spying apps and processes. To assess whether the activity causing your overheating issue is due to you or spying, check your task manager or activity monitor for anything out of the ordinary (more on that below).
Apps are acting up
If your apps suddenly behave strangely (randomly shut down or lag), you might be dealing with computer spying. How to tell if someone is spying on your phone? Assessing app behavior is one way to do it. Unauthorized access or unusual network activity due to spying can affect your otherwise normally functioning apps.
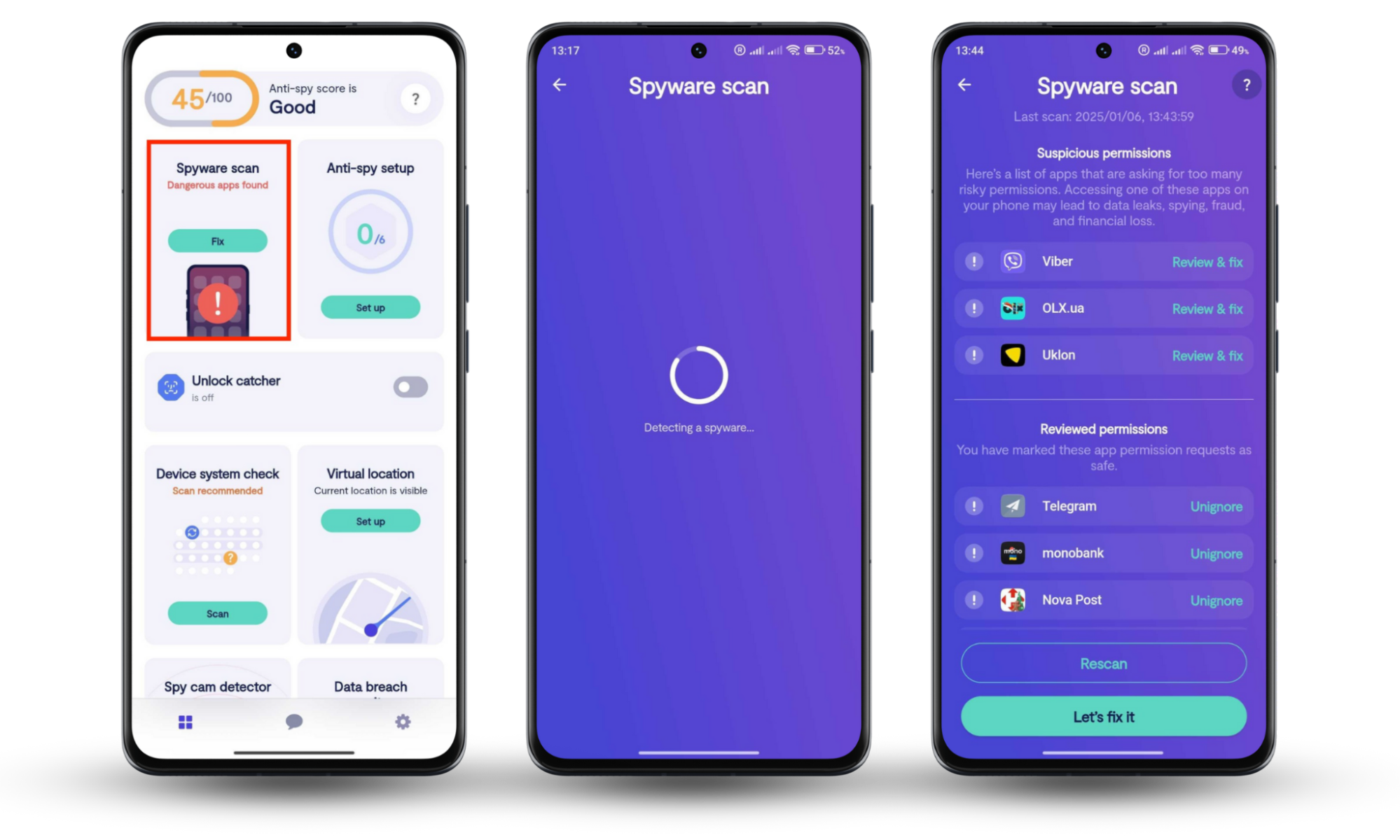
Did you know that apps acting up is also a sign of spyware on your Android or iOS device? If spyware has infected your desktop, your mobile phone may also be at risk. To protect your devices from damage, use Clario Anti Spy’s Spyware scan feature. It helps you check your phone for spyware and reduces the chance of falling victim to stalkers.
Here’s how to use Clario Anti Spy’s Spyware scan:
- Open Clario Anti Spy and create an account.
- Press Scan beneath “Spyware scan.”
- Wait for Clario Anti Spy to scan your device, then follow its instructions to secure your phone.
Note
iOS users can use Clario Anti Spy’s Device system check to scan for evidence of a jailbreak, which is one of the main tactics spies use to install spy software on your phone. Open Clario Anti Spy and press Scan underneath Device system check to get started.
Slow speeds
Slow speeds mean that your device storage is full or is overwhelmed with computing tasks. Either of these causes could be due to spying apps or unauthorized device access. If your device storage is near capacity, clear up space—and if you are still experiencing slow speeds, you might be dealing with spying.
Webcam is recording without your permission
If your webcam suddenly records without your permission, it’s likely due to unauthorized device access. Legitimate apps and programs always ask for your permission before using your webcam.
Erratically flashing lights
Flashing lights are a sign of device activity. Though this activity can be due to normal device usage, erratically flashing lights—especially if you’re not engaged in any heavy computing tasks—indicates that spy apps or processes may be running in the background.
Strange and frequent pop-ups on your desktop
Hackers try to trick you into downloading spyware. Sometimes pop-ups that claim to be anti-spy apps or notifications, are actually spyware in disguise. They con you into clicking them with “notifications” that your device is infected or that you urgently need protection. Legitimate spy tools will never use emotional language to persuade you.
Sudden homepage change
If your homepage suddenly changes on your web browser, it may be due to unauthorized device access. Hackers and spies may change your homepage to a malware-ridden website or a site that offers fake malware solutions or scams.
Browser keeps redirecting
If your browser frequently redirects your web traffic to irrelevant search results or unsafe websites, it could be a sign that you’ve been hacked. A browser hijacker may also be the culprit. This type of malware will redirect your web traffic to unsafe websites—often to generate ad revenue.
Unknown programs installed on the computer
Unknown programs can be installed by hackers accessing your computer—or if you accidentally download malware-infected files or programs. Either way, these programs are unsafe and should be completely removed from your device.
Suspicious browser activity
Suspicious browser activity indicates that someone is trying to get to your data. Your browser is the gateway to your online identity, and hackers can use tools like keyloggers, browser hijackers, and screen capture to steal your personal data.
Ransomware attack message
A ransomware attack message is a clear sign that someone has stolen your data—if the message is real. Though sometimes hackers can bluff to get you to pay the ransom, you should treat these messages seriously. It’s advised not to pay the ransom and contact the proper authorities to help get your data back.
The task manager or activity monitor is disabled
A disabled task manager or activity monitor is a common sign of malware infection. These applications are designed to give you an overview of what programs are running on your computer—and can help you target malware. Some malware will disable these apps to avoid detection.
Programs start randomly
Some types of malware will automatically start up unwanted programs when you boot your computer. Often these programs are dangerous, like adware, browser hijackers, and other malware.
How to detect and remove spyware on your computer?
Spyware is designed to steal your private information to cause further harm to you and your contacts. Stopping the threat, swiftly and completely, will help stop the attack from spreading.
Here’s how to detect and remove spyware on your computer:
- Check for suspicious processes through Task Manager
- Use a trusted antivirus
- View active internet connections
- Watch for open ports
- Format your hard drive
Now let’s explore these solutions in more detail:
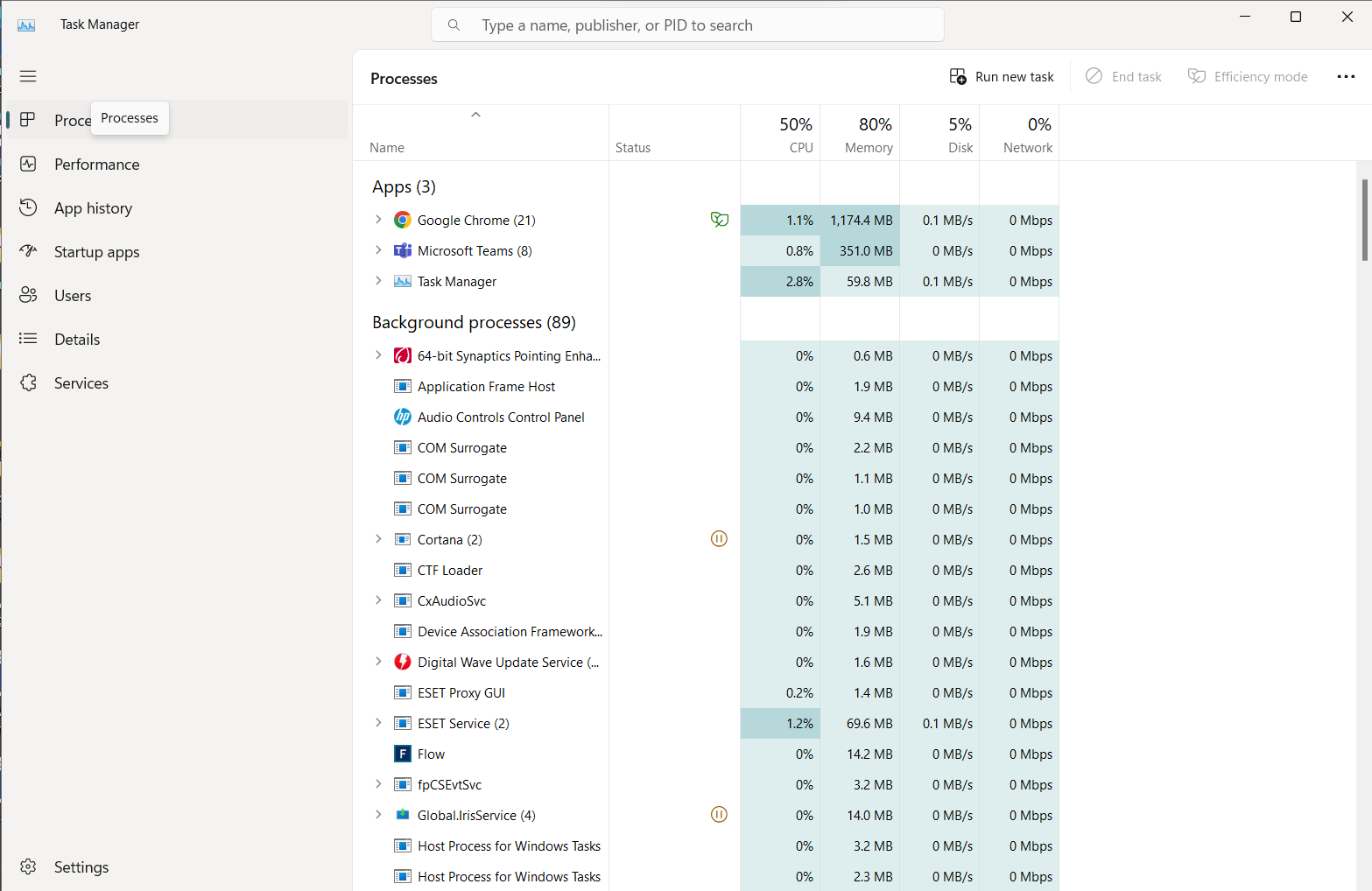
Check for suspicious processes through Task Manager
Checking for suspicious processes can help you identify and stop spyware. Often spyware runs as a background process on your system to steal your data without detection. Task manager programs help you detect the low-key processes of spyware threats.
Here’s how to check for suspicious processes through Task Manager on Windows:
- Press and hold: Control + Shift + Escape to open Task Manager
- Assess which background processes take up the most CPU power and verify them.
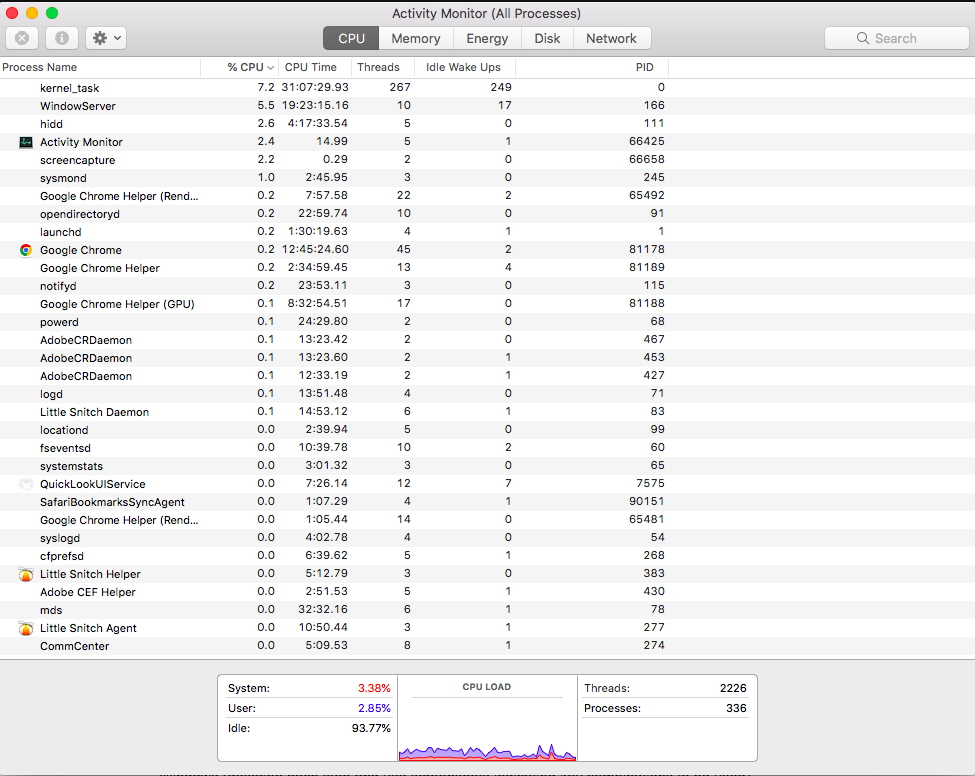
Here’s how to check for suspicious processes through Activity Monitor on macOS:
- Press: Command + Spacebar to open Spotlight.
- Search and select: “Activity Monitor”.
- Assess which process names take up the most CPU percentage and verify them.
What to do if your computer is hacked? If you’ve detected spyware on your computer, it’s crucial that you remove it immediately.
Use a trusted antivirus
Trusted antivirus apps are designed to check your computer for spyware and remove it—even those that are hard to detect. Plus, they are always updated to keep up with the latest threats. The best antivirus programs are often coupled with other cybersecurity tools to provide comprehensive protection.
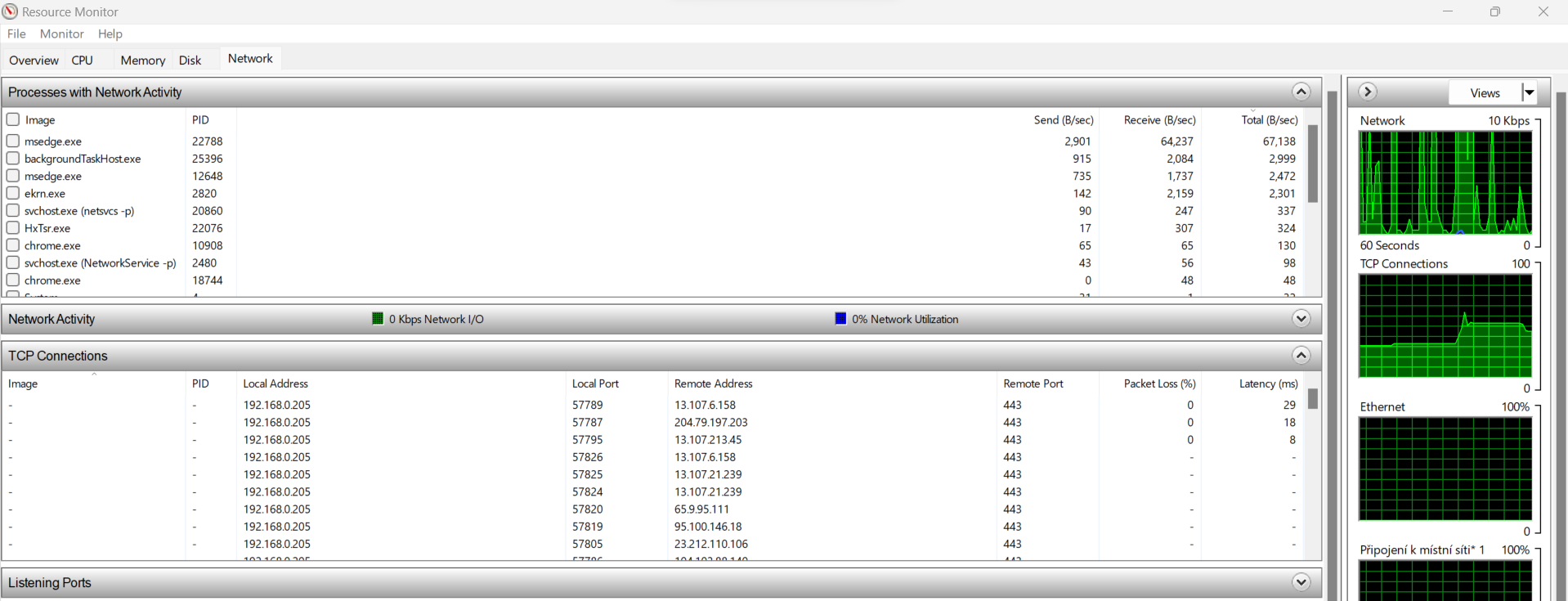
View active internet connections
If hackers use spyware to monitor your internet activity, you may catch them by checking your active internet connections. Spying tools eat up your internet bandwidth. Getting an overview of your active internet connections can let you spot possible threats.
Here’s how to view active internet connections on Windows:
- Press the Windows key + R to open the Run dialogue box.
- Type ‘resmon’ and press Enter to open the Resource Monitor.
- Click the Network tab in the Resource Monitor.
- Under the TCP Connections section, you’ll see a list of active internet connections.
Here’s how to view active internet connections on macOS:
- Press: Command + Spacebar to open Spotlight.
- Search and select: “Activity Monitor”.
- Click the Network tab to view active internet connections.
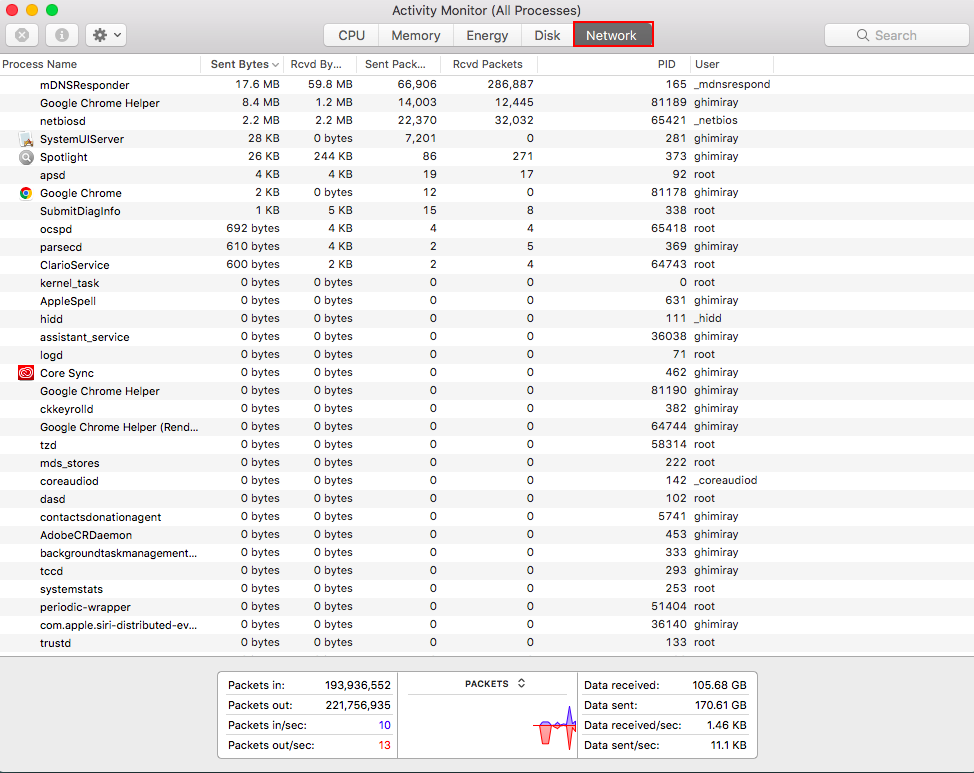
Watch for open ports
As the gateway to the internet, hackers can exploit your computer ports—especially if you have too many open. Your computer programs use various ports to connect you to different parts of the internet. But if you have too many open ports, you increase your attack surface.
Here’s how to check open ports on Windows:
- Press the Windows key + R to open the Run dialogue box.
- Type ‘resmon’ and press Enter to open the Resource Monitor.
- Click the Network tab in the Resource Monitor.
- Under the Listening Ports section, you’ll see a list of open ports.
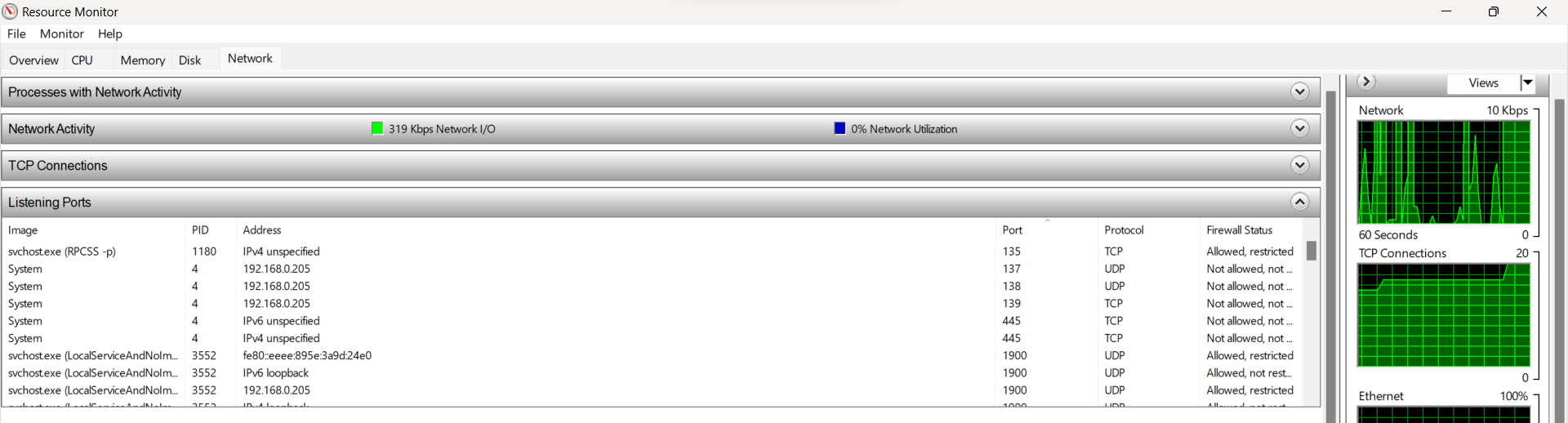
Here’s how to check open ports on macOS:
- Press: Command + Spacebar to open Spotlight.
- Search and select: “Network Utility”.
- Click the Port Scan tab. Enter your IP address (you can use a free tool to find your IP address), then click Scan.
- After the scan, the tool will display a list of open ports.
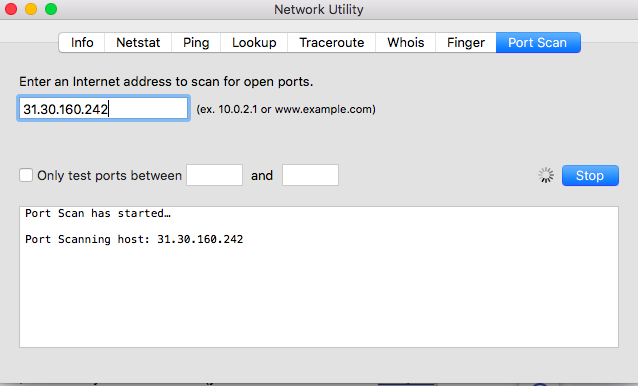
Format your hard drive
If your computer is ridden with spyware and other forms of malware, you can get a clean start by formatting your hard drive. Spyware is increasingly difficult to detect and remove, so sometimes, formatting your hard drive is the most effective solution. This process will wipe away anything saved on your hard drive (including malware)—unless you made a backup.
Here’s how to format a hard drive on Windows:
- Press the Windows key + X on your keyboard and select Disk Management from the pop-up window.
- In the Disk Management window, locate the hard drive you want to format.
- Right-click on the drive and click Format.
- In the Format window, choose the File System (usually NTFS) and the Volume Label (name of the drive).
- Click OK. You will be warned all data will be lost. Confirm.
Here’s how to format a hard drive on macOS:
- Press: Command + Spacebar to open Spotlight.
- Search and select: “Disk Utility”.
- In the Disk Utility window, locate the drive you wish to format from the left column.
- From the top toolbar, click Erase.
- In the Erase dialogue box, choose the format (usually APFS) from the dropdown menu You can change the volume name too.
- Click Erase to start the formatting process. Confirm.
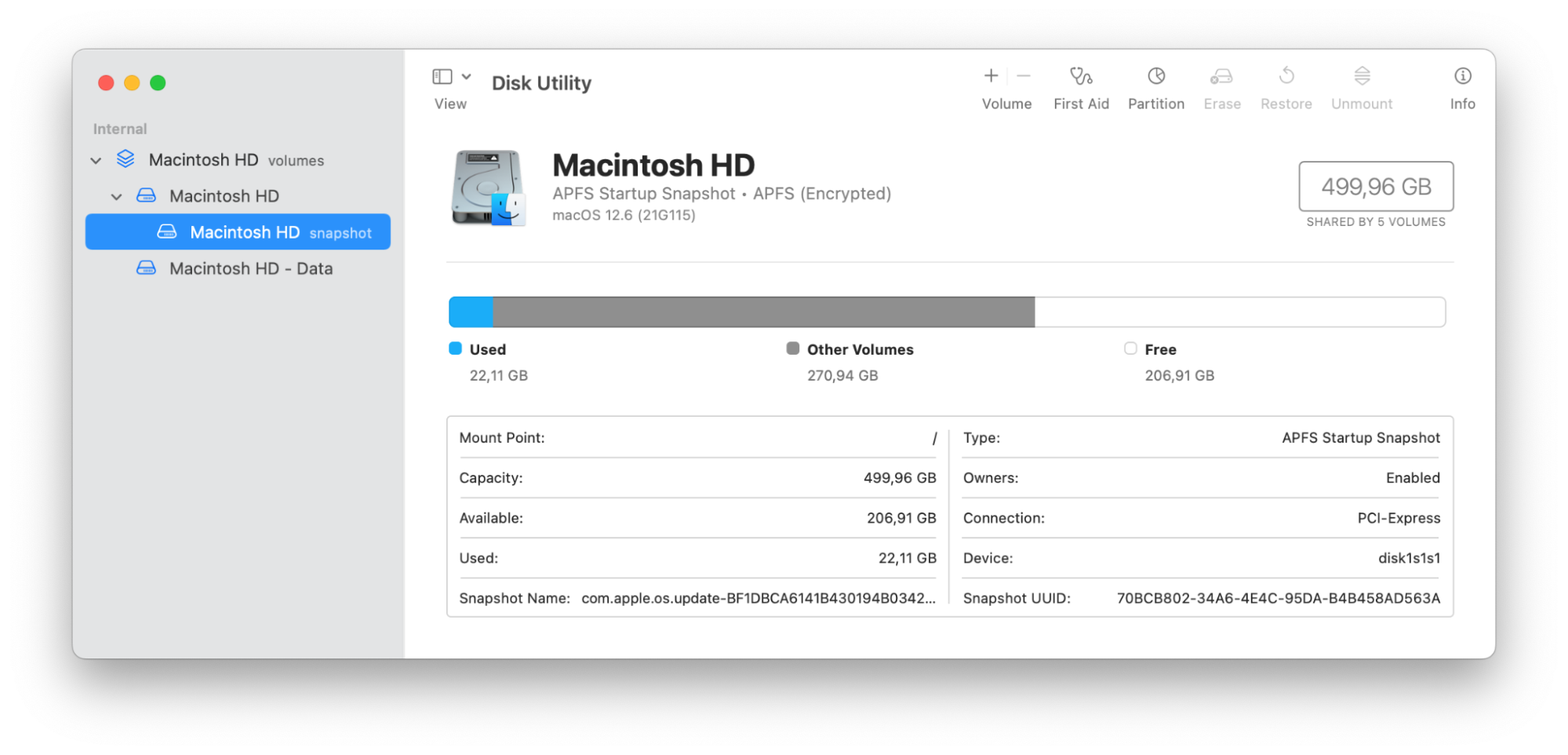
How to protect your computer from spying
Prevention is the best strategy against spying and malware. Hacker tools are increasingly sophisticated and it’s getting hard to tell if someone is spying on your computer. It’s better to avoid threats altogether than to fight off an attack that evades detection.
Here’s how to protect your computer from spying:
- Install an antivirus program
- Download software only from trusted sources
- Update your system regularly
- Avoid suspicious websites
- Use а VPN
- Use complex passwords
- Be suspicious of strangers
- Don’t open emails from unknown senders
- Scan your system regularly for viruses
- Be attentive to antivirus notifications
Let’s delve deeper into these protective measures:
Install an antivirus program
An antivirus program can scan your computer for spyware and stop a threat in its tracks. Also, quality antivirus software will keep up with the latest hackers' tools and techniques to ensure total protection against various threats.
Download software only from trusted sources
Unverified software from untrusted sources can contain hidden spyware and other malware. Plus, they can have bugs and glitches that affect your user experience. Steer clear of wonky apps, and only download quality software to ensure a safe and streamlined experience.
Update your system regularly
System updates can contain patches and security updates to protect your computer from the latest threats. Hackers and other bad actors are constantly developing new ways to attack your device and steal your data. Update your system regularly to stay ahead of them.
Avoid suspicious websites
Suspicious websites can contain spyware and links to other dangerous websites or infected files. You can usually identify these websites with their poor grammar and design, invasive pop-ups, or a general sense that something is “off.” Stay clear of these websites.
Use а VPN
A VPN will hide your IP address and encrypt your internet connection to ensure total protection against hackers and other snoops. It’s one of the most powerful tools for cybersecurity and offers other advantages, like bypassing geo-blocking.
Use complex passwords
Complex passwords and two-factor authentication are your first lines of defense to protect your profiles and devices from unauthorized access. Considering how much of our private information is up online, it’s a simple way to prevent spies and hackers from gaining access to it.
Be suspicious of strangers
Just like in real life, be wary of strangers in the cyber realm. Through social engineering, bad actors have a variety of ways to dupe you into giving up sensitive information, device access, and more. Don’t trust anyone you’ve never met in person. And remember: if they seem too good to be true, they probably are.
Don’t open emails from unknown senders
Email is a common way for hackers to send you malware-ridden files or links to unsafe websites. These attackers rely on the fact that people freely open emails from unknown senders. Don’t let your curiosity get the best of you. Ignore and delete these emails.
Scan your system regularly for viruses
A routine virus scan may help you detect spyware on your computer—as well as other forms of malware. A lot of spyware is designed to avoid detection by running in the background. A virus scan may find spyware on your computer that would have otherwise slipped right past you.
Be attentive to antivirus notifications
Antivirus notifications should never be ignored. They can fill you in on important software updates and even warn you of threats as they occur in real time. These notifications can help you take the necessary steps to immediately prevent a threat from spreading.
Is someone spying on your computer?
It’s not always easy to know if your computer is being monitored. Looking out for the signs of spyware and other malware is a start—but cyberprotection doesn’t end there. A dedicated anti-spy app, like Clario Anti Spy, is key for detecting and stopping spies in their tracks.
Clario Anti Spy protects your mobile devices from all types of cyber threats, helping you discover and remove vulnerabilities. Sign up today and use Clario Anti Spy’s Spyware scan and Device system check to check for spyware and security vulnerabilities.


