Table of contents
- Can someone control my phone?
- Mobile security breaches: statistics
- How to tell if someone is accessing your phone remotely
- How to block someone from accessing your phone
- Tips to block remote access on iPhone and Android
- How to stop someone from accessing your iPhone remotely
- How to block remote access on Android phone
- Conclusion
- FAQ
- How can someone access my phone remotely?
- Who is looking to gain remote access?
- How do I find out if someone is remotely accessing my phone?
Can someone control my phone?
Yes, it’s possible for someone to remotely access your phone, especially if you’ve unknowingly granted permissions or your device has a security vulnerability. This can happen through malicious apps, spyware, or system-level exploits.
To protect your phone's security, use strong passwords, avoid installing unknown apps, and be cautious about granting permissions to apps or people you do not trust—your phone can be hacked remotely.
Mobile security breaches: statistics
Below is a list of key statistics on mobile security:
- 98% of mobile malware targets Android devices
- In Q1 2023, adware was the most common threat to mobile devices (34.8%)
- 80% of phishing attacks targeted mobile devices
How to tell if someone is accessing your phone remotely
You can usually tell if someone is accessing your phone remotely because of fast battery draining or strange behavior. If you haven't been using your device more than usual, but the battery is depleting rapidly, this could be a sign that spyware is running in the background. Likewise, if your device is behaving erratically, crashing frequently, or slowing down for no apparent reason, it could be hacked.
Here are some other signs that someone is remotely controlling your phone:
- Unusual warmth. Does your phone feel warm to the touch when idle? The reason for this can be malware or a malicious app running in the background, consuming your processing power.
- Unrecognized apps or accounts. If you see apps you don’t remember downloading, or new accounts linked to your device that you didn’t create, someone probably has access to your device. These are often the result of phishing attacks where you accidentally grant access to attackers.
- Data spikes. A sudden, unexplained spike in data usage could signal that something on your phone is sending information to a remote server. Malware may be transmitting your data in the background.
- Unexpected security notifications. Suspicious password change requests or new login locations can mean someone is attempting to access your accounts. This might follow a successful phishing attack where the attacker obtained your credentials.
- Unusual pop-ups and ads. A barrage of pop-ups and ads might indicate your device has adware, a form of malware. This could result from downloading an infected app from an untrusted source.
- Emails or texts sent from your account. If friends or family report receiving strange messages from you or you notice emails or texts in your sent folder that you didn’t write, this could be a sign of unauthorized access to your account.
Tip
If you notice at least two of the signs above, there’s a high chance someone has compromised your device. Take action quickly to protect yourself from further threats. Also, educate yourself on how to stop someone from spying on your phone.
Regularly checking your device for unfamiliar apps, monitoring battery and data usage, and being mindful of your phone’s typical performance can make the difference in catching unauthorized access early.
How to block someone from accessing your phone
Prevention is the key to ensuring your phone remains secure from cyber threats. Use the following practices to bolster your phone’s defenses and avoid the headaches associated with unauthorized access to your phone.
Tips to block remote access on iPhone and Android
To prevent someone from remotely accessing your iPhone or Android device, take these steps:
- Keep your software up to date. Software updates often include security patches that protect your phone from known vulnerabilities.
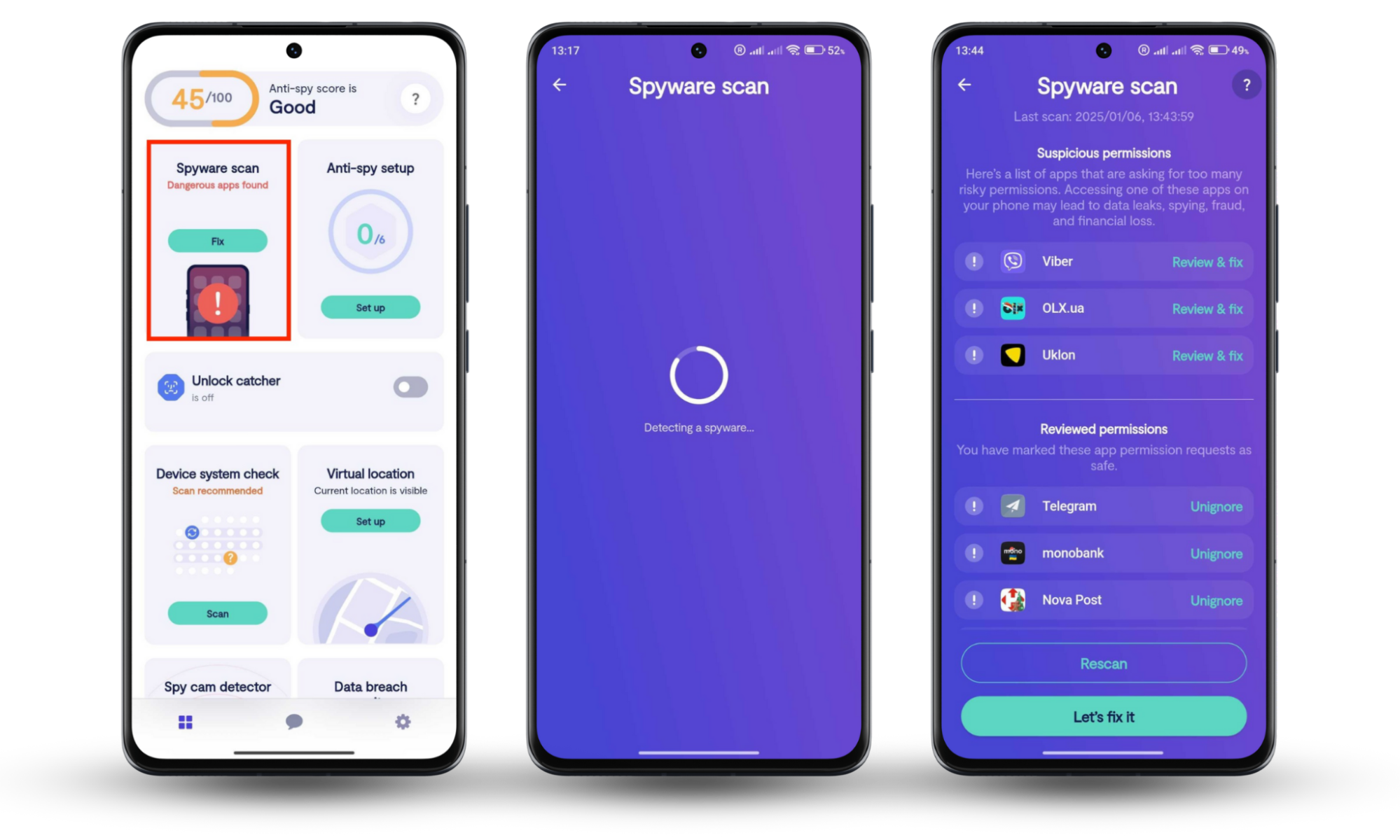
- Run a Spyware scan. Use Clario Anti Spy’s Spyware scan tool to identify and remove unauthorized spy apps or apps with suspicious permissions on your Android. To run a deep spyware scan, follow these steps:
- Download Clario Anti Spy and get a subscription.
- Click Spyware scan and wait for the check to run.
- If Clario Anti Spy identifies suspicious apps, follow the on-screen instructions to immediately get rid of the spyware app and restore your privacy.
- Use a strong passcode or PIN. A strong passcode or PIN will make it more difficult for someone to access your phone if it’s lost or stolen.
- Enable two-factor authentication. 2FA adds an extra layer of security by requiring you to enter a code from your phone in addition to your password when you log in to your accounts.
- Be careful what links you click and what attachments you open. Phishing emails and text messages often contain links or attachments that can infect your phone with malware.
- Only download apps from trusted sources. The App Store and Google Play Store have security measures to restrict malicious apps. Stick to these services when downloading new apps and be selective about what you download.
- Follow safety checklists. Clario Anti Spy’s Anti-spy setup gives you step-by-step checklists to ensure you have all the essential protections to block someone from accessing your phone.
- Utilize VPNs and Secure Networks. A Virtual Private Network (VPN) encrypts your data and secures your connection, particularly when connecting to public Wi-Fi. This reduces the risk of hackers intercepting your data.
- Regularly review the list of apps on your device. Check both your main applications list and any app folders. Remember, some malicious apps may hide themselves. To find hidden apps, go to the App Store and click the profile picture in the upper-right corner. Then, go through this list carefully and remove any apps you don't recognize or didn't install yourself.
- Examine the accounts connected to your device. Go to your device settings and select “Accounts” or a similar option. Ensure all linked accounts are familiar to you.
- Turn off tracking. If you’re concerned that someone is tracking you, follow the comprehensive steps on how to stop someone from tracking your phone.
- Find out if someone has leaked your data online. With Clario Anti Spy’s Data breach monitor, you can scan the Dark Web and see if recent security breaches have involved your passwords and accounts. You can then review the list of compromised passwords and change them or delete the accounts.
How to stop someone from accessing your iPhone remotely
To stop someone from accessing your iPhone remotely, focus on your Apple ID security and device settings. Use two-factor authentication, update iOS regularly, and enable biometric locks. Avoid jailbreaking your device and only install apps from the App Store. Your phone stays safer when these protections are in place.
Here are the most effective iPhone-specific actions you can take to prevent unauthorized remote access:
- Enable Touch ID or Face ID. Touch ID and Face ID add an extra layer of security by allowing you to unlock your phone with your fingerprint or facial scan.
- Use the Find My feature. Find My can help you track down your phone if it's lost or stolen.
- Enable remote wipe. Apple’s Find Devices feature allows you to erase all of the data on your phone remotely from another device if it's lost or stolen.
- Regularly review iCloud settings and security features. Ensure that features like two-factor authentication are enabled, and review app permissions in the Settings app. Only give apps permission to access data they need to function correctly.
- Only download apps from the official App Store. The App Store follows strict guidelines that reduce your risk of downloading malicious software.
- Don’t jailbreak your iPhone. Jailbreaking weakens your device's security mechanisms. This makes your iPhone much more vulnerable to attacks, making it very easy for attackers to install monitoring software. In fact, monitoring software often requires that your phone is jailbroken.
Clario Anti Spy’s Device system check feature can scan your device for signs of a jailbreak or other major security threats. This way, you’ll know whether anyone has bypassed Apple’s security to gain unauthorized access to your device.
How to block remote access on Android phone
To protect your Android phone from remote access, strengthen your screen lock, enable two-factor authentication for your Google account, and stick to trusted apps from the Play Store. Avoid rooting your device, keep your software up to date, and actively monitor your account activity and data security.
Take the following Android-focused actions to strengthen your phone’s defenses against remote intrusions:
- Enable Google Find My Device. Find My Device helps you locate, ring, or wipe your device from the web.
- Enable remote lock and remote erase. These features allow you to lock or erase your phone remotely if lost or stolen.
- Avoid rooting and downloading apps from third-party stores. Rooting, like jailbreaking for iPhones, can create security vulnerabilities, allowing someone to access your phone remotely. Stick to the options on the Google Play Store. You can also use Clario Anti Spy’s Device system check to scan your device for signs of tampering.
- Monitor your Google account activity. Keep track of your account activity, and utilize tools like Google Play Protect that scan apps and ensure they are safe.
- Encrypt sensitive data. Encrypt text messages and emails or use secure messaging apps, like WhatsApp or Signal, to protect your messages with strong encryption.
If someone is accessing your phone remotely, they might also be listening to your calls. Find out how to stop someone from listening to your phone calls and what to do in order to stop this invasion of privacy.
Conclusion
Don’t let hackers and stalkers access your private life through remote access to your phone. Protect your privacy by practicing good digital hygiene, staying vigilant, and using Clario Anti Spy to scan your device for signs that someone is trying to gain access.
Clario Anti Spy’s Anti-spy setup tells you everything you need to know to secure your device and prevent someone from accessing it. Combined with the powerful Data breach monitor that informs you when your personal information is leaked online, you’ll never have to worry about unauthorized spies again.
FAQ
How can someone access my phone remotely?
The most common way hackers can access a device is through phishing attacks. Hackers also use fake apps, insecure Wi-Fi networks, and other vulnerabilities.
Fake websites can steal your data. Phishing emails or texts look like official company communications, leading to websites that look familiar or similar to official ones. Once you click the link and enter your credit card details or a password on a website you feel is legitimate, you allow someone to access your phone or control your bank transactions remotely.
Always double-check the sender’s email address, and be wary of unsolicited requests for personal information. Avoid clicking links altogether, especially when they lead to a login screen. Instead, just navigate to the official website from your browser.
Hackers can trick you into downloading fake Android apps. If you use an Android device, always download apps from the Play Store to reduce the risk of malicious apps gaining unauthorized access to your data and your device’s features.
Hackers can use other methods to gain access. Avoid jailbreaking, SIM card swapping, and compromised Wi-Fi networks. Also, look out for rooting, USB debugging, SMS-based attacks, and Bluetooth vulnerabilities.
Who is looking to gain remote access?
- Hackers pursue money or political ends by adding malware or stealing personal data
- Spouses or partners can get jealous, suspicious, or just overly curious
- Employers may add trackers to ensure policy compliance or track productivity
- Governments gain remote access to support national security and law enforcement
- Tech support teams ask for remote access to troubleshoot issues.
How do I find out if someone is remotely accessing my phone?
Look for unexpected or suspicious behavior on your device, such as strange apps, unfamiliar pop-ups, or unusual data usage.
If you wonder how to remove a hacker from your phone, Clario Anti Spy has additional advice to help.


