Table of contents
- What is social engineering?
- How does social engineering work?
- Real examples of social engineering
- Toyota Boshoku $37 million loss
- Shark Tank bookkeeper tricked into investing in a home renovation project
- Yahoo’s worldwide data breach
- MyEtherWallet attack
- Democratic convention phishing scam
- Raffle House user’s information exposed after a data breach
- Popular types of social engineering attacks
- Phishing
- Spear phishing
- Pretexting
- Baiting
- Scareware
- Tailgating
- DNS spoofing
- Tips for preventing social engineering attacks
- Verify contacts
- Watch for website certification
- Avoid tempting offers
- Implement multi-factor authentication
- Use strong passwords
- Stay alert at door entries
- Install robust security software
- Avoid social engineering scams to safeguard your data
We’re often told to pay attention to cybersecurity, and for a good reason. A hacker attack occurs every 39 seconds, and sometimes they’re successful not only because of technical vulnerabilities. In most cases, cybercriminals prey on human weakness. This tactic is often called human-based social engineering fraud or human hacking.
Social engineering fraud is less predictable than regular malware-based intrusions, making it even more dangerous. That’s why to protect yourself online, you should be aware of the tactics criminals can use against you. This awareness can supplement software that detects and removes malicious programs from your devices.
What is social engineering?
Social engineering is a manipulation technique used to persuade people to share sensitive information. Skilled manipulators try to get your personal details (for example, your full name, date of birth, or address), payment information (credit card or social security number), or account passwords to commit financial fraud.
Unlike traditional hacking, these attacks target human vulnerabilities to gain unauthorized access to your devices or accounts. And what’s scary is that you can implement all the latest technological safeguards (like firewalls and antivirus software), yet social engineers can still penetrate them by hacking human psychology instead.
Let’s look at how criminals operate to get what they need.
How does social engineering work?
Scammers usually obtain data from their victims remotely, and sometimes, they don’t even interact with people directly. For example, they might send phishing emails with malicious links. More sophisticated types of social engineering attacks are carefully planned and include several steps:
- A social engineer gathers data about any potential victims by scanning their social media accounts, mail, asking around, or even digging through their dumpster.
- A scammer then contacts the victim to gain their trust, posing as an acquaintance, colleague, bank manager, etc.
- The victim takes the bait and willingly hands over whatever information is requested.
Social engineering cybercriminals target individuals, and can also gain unauthorized access to entire companies. Yes, you got that right: even enterprises with cybersecurity departments can fall for such scams. According to the 2021 Data Breach Investigations Report, educational, financial, scientific, arts and entertainment, and public administration entities were the industries most susceptible to these attacks.
Real examples of social engineering
Do you still doubt that serious organizations could willingly hand over their confidential information to scammers?
Well, many real-world examples prove otherwise. Let’s see how industry veterans have been tricked by social engineering scams.
Toyota Boshoku $37 million loss
The infamous Toyota 2019 social engineering attack is a prime example of a business email compromise tactic.
Attackers, posing as company representatives, convinced an employee with financial authority at Toyota Boshoku Corporation (a major supplier of Toyota) to share payment data. Criminals used this information to wire over $37 million from the company’s accounts.
Shark Tank bookkeeper tricked into investing in a home renovation project
Barbara Corcoran from the television program Shark Tank nearly lost $400k to cybercriminals who convinced her bookkeeper to pay a fake real estate renovation invoice. These criminals had clearly done their homework. They engaged in back and forth email exchanges with her bookkeeper. After a few carefully crafted messages, scammers convinced the assistant to transfer money to them.
Luckily, Corcoran’s team noticed the scam and was able to get the money back later. However, this is one of many examples of social engineering attacks affecting even pros.
Yahoo’s worldwide data breach
Tech companies are no less vulnerable to these attacks. In 2014, a Yahoo employee fell for a social engineering scam that led to one of the largest data breaches of all time.
The employee clicked on a phishing email link and unwillingly infected the entire Yahoo network with malware. A single person’s mistake resulted in leaking the data of over 3 billion users.
MyEtherWallet attack
Criminals managed to steal Ethereum from MyEtherWallet accounts. The hackers intercepted users’ browser activity and automatically redirected them to a fake version of the cryptocurrency’s storage website. When unsuspecting users tried to log in, their account data was sent to the hackers, who quickly transferred over $150,000 worth of Ethereum to other wallets.
Democratic convention phishing scam
Politicians also get hit by social engineering attacks, as shown by the hacking of Hillary Clinton's 2016 presidential campaign email. The candidate’s chairman clicked on a seemingly harmless email link masquerading as a Gmail service. This allowed hackers to steal his login credentials and leak over 50,000 emails.
Raffle House user’s information exposed after a data breach
A leading UK online lottery platform, Raffle House suffered a massive data breach in 2021. Due to a misconfigured Amazon S3 bucket, users could see each other’s personal data. This led to the massive leak of personally identifiable information (including names, emails, prize IDs, and phone numbers). The possible implications of such a breach for customers could have been identity theft or fraud, phishing, and blackmail.
Popular types of social engineering attacks
Social engineering is possible anywhere when humans are involved and comes in many different forms. They include the following:
Let’s see how you can recognize these attacks.
Phishing
Phishing means baiting unsuspecting users into revealing sensitive information. Criminals can get victims to share data in many ways, but email phishing is the most common and effective type. It implies sending emails with attached trackers or links containing other malware.
According to the 2020 Phishing Benchmark Global Report, nearly 20% of employees clicked on phishing emails during simulations meant to measure clickthrough rates (even in organizations with security awareness training).
Spear phishing
Spear phishing is a form of phishing targeted at specific individuals or groups. These attacks involve a lot of research to make the emails believable. Some spear phishing attacks take weeks to prepare and have far better results than regular email phishing (for criminals, of course).
Pretexting
Pretexting takes advantage of a user’s trust in a communication’s authenticity. In contrast to regular phishing, pretexting usually takes place over the phone or in voice chat. Criminals pretend to be someone trustworthy to gain access to sensitive information. For example, a scammer impersonating the head of a department can trick an employee into disclosing corporate account data.
Baiting
Baiting social engineering is also similar to phishing, but it relies on manipulating people's sense of opportunity and curiosity. For example, the victim may be tricked into clicking on a conveniently placed link with a free song from their favorite artist, not knowing it contains malicious software.
Criminals can bait you even offline. For example, they may leave flash drives lying where they know people will find them (in a bathroom or stairwell in a hotel). Curiosity makes you plug the found flash drive into a computer, inadvertently infecting the system with malware.
Scareware
Scareware (fraudware) is a fear-based tactic that prompts victims to purchase useless or dangerous products. For example, a pop-up ad may say that your device is infected with a virus and provide a link to a fake antivirus application. However, installing this software actually infects you with malware, allowing hackers to get hold of your data.
Tailgating
Tailgating means using an authorized person to gain access to restricted areas. For example, someone might gain access to a secured area of a building by pretending they forgot their security pass and following someone else in.
A criminal can also use tailgating to gain access to a public computer, in an internet café, for example. If the previous user forgot to log off from their email account, the scammer could access all those messages.
DNS spoofing
In DNS (Domain Name System) spoofing, a hacker redirects internet users to a fake website instead of the one the victim wanted to visit. This is done via DNS cache poisoning and intercepting the victim’s DNS requests (their browser’s request for information from a website’s server). When the victim enters their account credentials on the fake website, the information goes straight to the cybercriminals.
Spoofing is one of the more subtle engineering attacks, and most users don’t even notice they’ve been redirected. Thankfully, you can avoid these scams if you stick to some essential safety tips.
Tips for preventing social engineering attacks
Social engineering attacks rely on human error and emotion, which is both their strength and weakness. There are simple rules for staying safe online, and awareness should be your primary means of protection against social engineering.
The most useful tips and practices include:
- Verify contacts
- Watch for website certification
- Avoid tempting offers
- Implement multi-factor authentication
- Use strong passwords
- Stay alert at door entries
- Install robust antivirus software
Here’s how these practices can help you.
Verify contacts
You can protect against most phishing emails as long as you verify they are from trusted senders. Scammers usually imitate legitimate companies by mimicking their names. You can easily check their authenticity by looking at the domain name (the part after the “@” symbol in the title). Here, you should watch out for misspellings (in the name or the email body) or copy the domain name into the search engine to check if it is legitimate.
Watch for website certification
You can quickly check if a website is secure without clicking on a link. How? Secure URLs start with an “HTTPS” instead of “HTTP.” If a website you visited raises your suspicions — don’t click anywhere. Instead, click on the padlock icon near the address bar, and it’ll show if the site has an SSL certificate (if not — exit quickly).
Avoid tempting offers
If a deal sounds too good to be true, then it probably isn’t true. Sounds pessimistic but If someone makes an outlandish offer or offers a free reward, stop and think about it. How does it benefit the sender? Does it even make sense? The golden rule: if you’re not paying, you’re the product (or victim, in this case).
Implement multi-factor authentication
Multi-factor authentication requires users to provide different pieces of data to access a system. For example, a user might need to input a one-time code delivered via SMS in addition to a password to enter a secured website. This technology makes the criminal’s job much harder, as they tend to obtain just one piece of data via this form of hacking.
Use strong passwords
Complex passwords provide essential protection because they prevent scammers from accessing your account through guesswork. A strong password contains at least eight characters (including numbers and special symbols). Plus, you should exclude any commonly used words or combinations. Feel free to read our blog to learn more about creating complex passwords.
Stay alert at door entries
Ensure no one without the proper credentials follows you when you enter restricted areas, like your workplace or apartment building. If you think you’re being tailgated, just wait for the stranger to enter the door first, using their own credentials.
Install robust security software
No matter how careful you are, you can’t avoid social engineering scams all the time. However, a powerful tool like Clario Anti Spy adds a protective barrier between malicious programs and your devices. Though not an antivirus tool, it protects you from tracking, data loss, and other privacy threats.
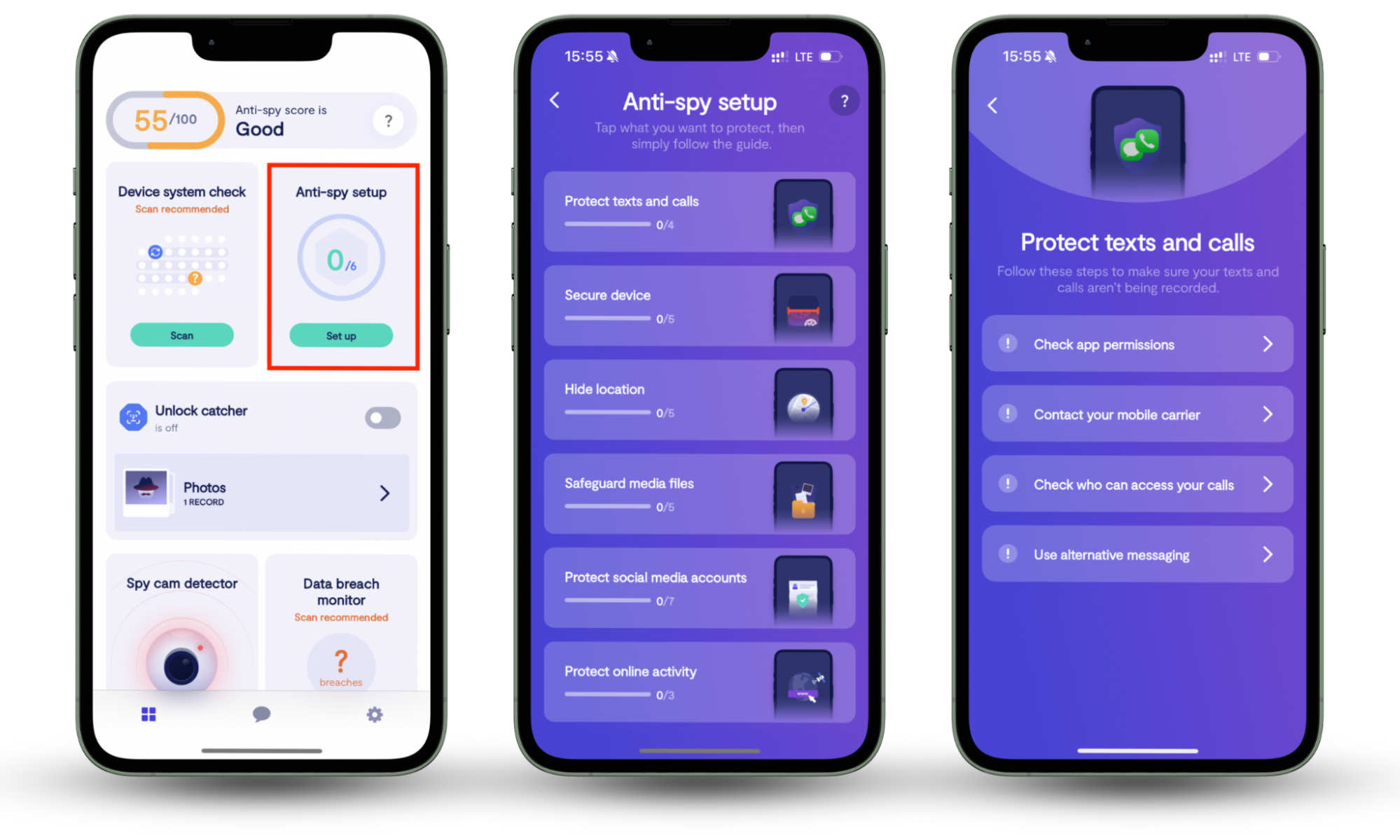
Social engineers are always coming up with new ways to access your data. That’s why you must have up-to-date anti-spy software to keep your devices secure 24/7. Our Anti-spy setup ensures you have the key protections you need to reduce your chances of spying. And with 24/7 support, you’ll always have access to expert help when you need it.
Follow the steps below to start using Clario’s Anti-spy setup to prevent tracking:
- Download Clario Anti Spy, get a subscription, and set up an account.
- Navigate to Anti-spy setup and click on Set up just below it.
- Clario Anti Spy will show you a list of categories. Click on each category and meticulously go through the steps to protect your data. Don’t worry; the app will guide you through this by taking you to the relevant page as needed.
Avoid social engineering scams to safeguard your data
Social engineering scams can be more meticulous than others, which is likely why they’re so successful. When you realize you were scammed, you feel helpless and frustrated with yourself, wondering how you could’ve let such a thing happen. For these reasons, learning about social engineering scams, including how they work, is important to avoid becoming a victim.
Take proactive measures, such as securing your phone using Clario Anti Spy’s Anti spy setup. It’s a nifty tool that removes the guesswork from protecting your privacy, helping you avoid social engineering and other scams.


