Table of contents
- How does a honeypot work in cybersecurity?
- What are honeypots used for?
- Production honeypot
- Research honeypot
- Types of honeypots
- Email trap or spam trap
- Decoy database
- Malware honeypot
- Spider honeypot
- HoneyBots
- Client honeypot
- Honeypots by the complexity
- Pure honeypots
- Low-interaction honeypots
- Mid-interaction honeypot
- High-interaction honeypots
- Deception technology
- Honeypot limitations
- Benefits of honeypots
- Break down the attacker kill chain
- Help in testing the incident response processes
- Straightforward and low maintenance
- Are honeypots illegal?
- Honeynet vs honeypot
- Honeypot network setup
- Database attack
- Insider attack
- Random attacks
- Conclusion
Honeypot meaning
Honeypots can be defined as security vulnerabilities that lure attackers into a trap to protect a company’s systems.
How does a honeypot work in cybersecurity?
Honeypots are designed to look exactly like a genuine computer system, at least to cyber attackers. For example, a honeypot can be made to look like it contains sensitive information belonging to a company’s customers or clients. These can include credit card information, full names, dates of birth, and other personally identifiable information.
Think of honeypots as decoys that are placed alongside a company’s actual systems used for production. They’re deployed by researchers acting similarly to a white hat hacker. The mirroring technique routes cybercriminals away from the intended target — the main systems.
When using honeypots, companies may leave certain portals open, which attackers may view as vulnerable and proceed to take advantage of them. As such, open ports can be used to entice attackers. Companies would then observe the attackers’ movements to learn how they work.
Honeypot cybersecurity isn’t designed for prevention, per se. It helps companies make a vulnerability assessment of their response systems by observing how attackers behave, approach their systems, and go about their attacks. This tells the organization if its defense systems are strong and reliable enough to withstand attacks.
If any gaps are found, the business will implement its learnings to improve and strengthen its intrusion detection system (IDS). There are many solutions used by companies to protect their systems — a honeypot trap is one of them.
Hackers will go out of their way to infiltrate a vulnerable system, but they don’t always have to work that hard.
One of the easiest ways they gain access is through exposed work emails. Once they have access, hackers can use these emails to send phishing messages, spread malware, or impersonate employees to steal sensitive company data.
The pros for hackers are obvious, but the cons for businesses are severe, ranging from financial losses to reputational damage.
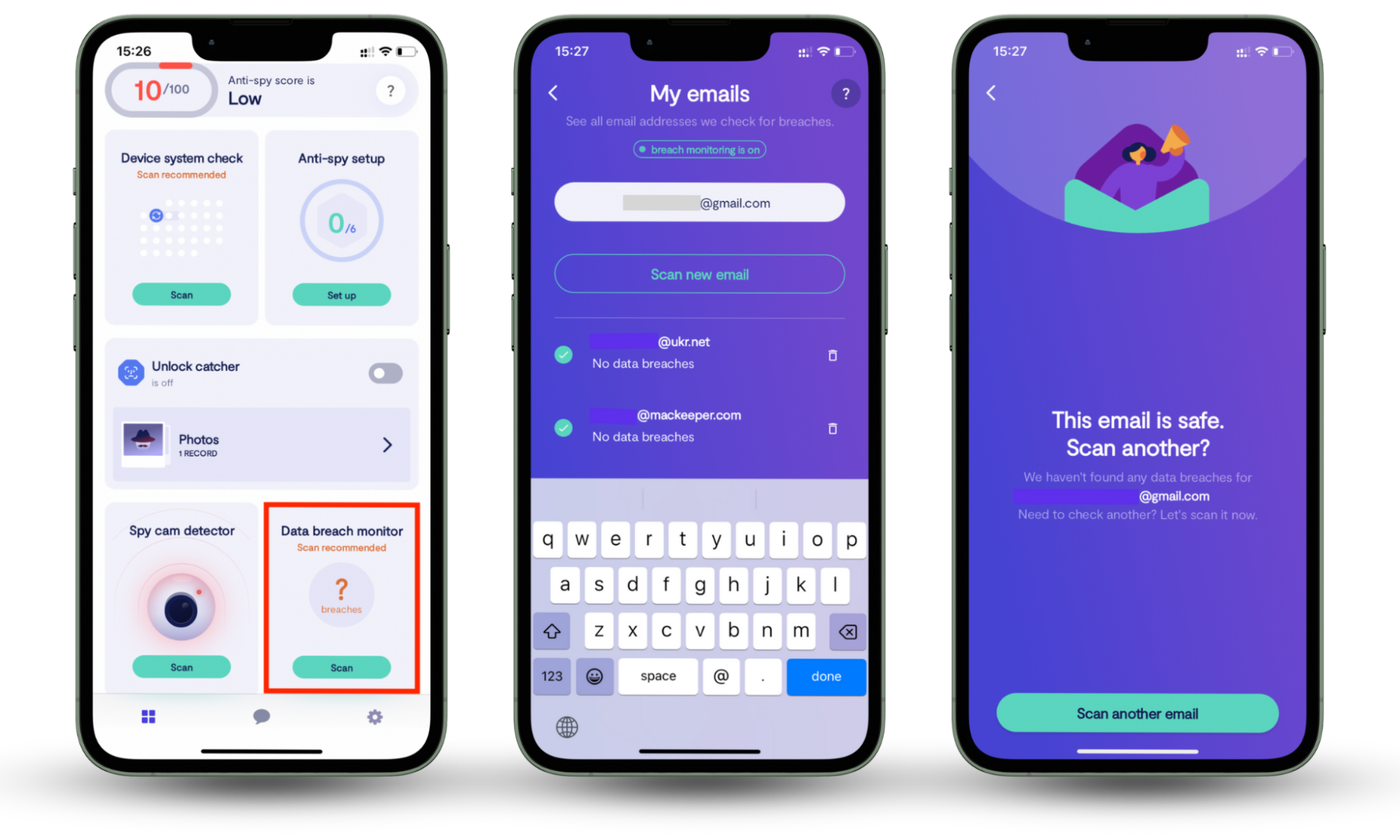
That’s why you should protect yourself from hackers with Clario Anti Spy’s data breach monitor. It checks if your email or account credentials have been exposed to a data/server breach and lets you act quickly to secure them.
How to use Clario Anti Spy’s Data breach monitor:
- Download Clario Anti Spy on your device and create an account.
- Go to Data breach monitor on the dashboard.
- Add the email you want to check and tap Scan.
- Review any breaches found and follow the different recommendations to secure your accounts.
Note
No single tool can protect all your data because attackers use different tricks to exploit weaknesses. That’s why a mix of tools works best. Use a firewall to protect your incoming data, Clario Anti Spy’s spy cam detector to check for hidden devices on your network, and a data breach monitor to find out if your personal information has been leaked. Knowing the differences between threats and having a clear list of any breaches makes it easier to stay secure.
Additionally, avoid dark patterns to protect your privacy.
What are honeypots used for?
Honeypots can be categorized according to their use — production honeypots and research honeypots.
Production honeypot
Production honeypots are geared toward finding and improving vulnerabilities in your internal network. They’re placed near your real production servers and run the same services to look genuine. This increases the chances of convincing attackers that the honeypot used is a real server, so they can be lured in.
Research honeypot
Conversely, research honeypots are focused on collecting information about how attacks work both in your network and externally on a broader scale. The information gained from the use of research honeypots helps administrators determine which vulnerabilities need urgent attention. It also helps them implement stronger defense systems against cyber threats.
Types of honeypots
There are various types of honeypots that fall into the production and research categories:
Email trap or spam trap
Email or spam honeypots use mail relays and open proxies to trap spammers. They detect the tests used by spammers. Spammers use tests on mail relays to determine if they can send multiple spam emails. After detection, the spam is blocked.
Decoy database
A decoy database honeypot lures attackers who target databases that manage data. Database firewalls can be used to implement this type of honeypot.
Malware honeypot
Malware honeypots attract malware attacks by mirroring APIs and software apps. When a trap is successful, the malware is analyzed to patch up vulnerabilities in the API and develop anti-malware protection.
Spider honeypot
Spider honeypots are honeypots used for trapping spiders, better known as web crawlers, by creating links and webpages that only web crawlers can access. The information obtained from these honeypots aids in blocking ad-networks crawlers and malicious bots.
HoneyBots
HoneyBots are a new type of honeypot. They were created to address the concern that honeypots could look suspicious to hackers, given that they don’t interact with them. As such, unlike other honeypots, HoneyBots are designed to interact with attackers. This increases the chances of fooling them into believing the honeypots are legitimate and trapping them as a result.
Client honeypot
Client honeypots are aimed at learning how attackers hack clients. As such, they trap the malicious servers used by attackers and monitor how they modify their target servers during an attack.
Honeypots by the complexity
Honeypots differ in their complexities and features:
- Pure honeypots
- Low-interaction honeypots
- Mid-interaction honeypot
- High-interaction honeypots
- Deception technology
Pure honeypots
These are unsophisticated, full-scale systems that operate on multiple systems. Pure honeypots use bug taps to monitor attackers’ movements. They masquerade as production systems carrying sensitive information to attract attackers and trap them.
Low-interaction honeypots
Low-interaction honeypots target systems that are known to attract criminals. They use fewer resources, including network services, Internet Protocol (IP), and Transmission Control Protocol (TCP).
This makes them simpler to use. Because they use limited resources, low-interaction honeypots don’t engage with attackers for extended periods, which means they collect limited information about attacks. Low-interaction honeypots can help collect data from worms and botnets.
Mid-interaction honeypot
Mid-interaction honeypots keep attackers engaged by confusing or distracting them. The mission is to collect information that will help organizations decide how best to respond to certain attacks.
High-interaction honeypots
High-interaction honeypots are more complex and aim to keep the attacker engaged as long as possible. That’s why, unlike other honeypots, high-interaction honeypots have multiple systems, processes, and databases available for the hacker to try to attack.
This gives researchers adequate time to study the attacker’s movements, preferences, and intentions, so they can identify any security gaps that may be present in the system. However, it also means they require a high level of expertise and need additional protection from threats.
Deception technology
Deception technology is used to identify cyber threats at an early stage, often with much success. It uses decoys in the form of databases, files, apps, and more to trap attackers and gather information.
Honeypot limitations
As with anything, honeypots have their disadvantages and potential risks.
- They don’t always successfully identify threats
- They fail to identify threats in legitimate systems
- Experienced hackers may be able to identify when a honeypot is being used
- The connection linking administrators and honeypots could be compromised
- Attackers can proceed to attack the legitimate system after they breach a honeypot, especially if the real system isn’t sufficiently protected.
Benefits of honeypots
Honeypots provide several benefits that can be helpful to researchers or administrators:
- Break down the attacker kill chain
- Help in testing the incident response processes
- Straightforward and low maintenance
Break down the attacker kill chain
Attackers prowl around looking for vulnerabilities in your system. Honeypots can stop them dead in their tracks and distract them, preventing them from attacking your real system. At this point, honeypots can keep adversaries engaged as they attempt to navigate the honeypot and get information, to no avail.
Help in testing the incident response processes
Honeypots can give you valuable information about how well your security systems fare against threats. Armed with this information, your security team can find ways to improve its response time and processes.
Straightforward and low maintenance
Honeypots are a simple and easy way to gather information about how threats behave. This can help organizations further strengthen their defense processes. All you need to do is set up a honeypot, and it takes care of the rest — you don’t have to spend time and additional resources monitoring and using it.
Are honeypots illegal?
It’s important to consider whether honeypots are legal, illegal, or ethical, especially if you’re looking into using them to improve your cybersecurity measures.
You may wonder whether honeypots could entice and trap innocent victims who may be trying to access a legitimate website. That’s a valid concern, however, non-hackers typically don’t go prodding around places they shouldn’t. Bad actors, on the other hand, actively look for targets to hack. That’s how they get trapped.
Another concern is whether it’s legal for researchers to collect information about the hackers trapped by honeypots without their knowledge or consent. Familiarize yourself with the Electronic Communications Privacy Act (ECPA) and Federal Wiretap Act, which protect service providers that collect information to protect themselves. For instance, you may fall under the ECPA’s service provider protection exemption.
Likewise, read up on the European Union (EU)’s General Data Protection Regulation (GDPR).
The most important thing is to avoid using personally identifiable information. And you must ensure that you use honeypots strictly to protect your organization.
Honeynet vs honeypot
A honeynet is a decoy network containing various types of honeypots hosted on one server or a handful of servers. This allows honeynets to research and monitor a wide range of attacks, including ransomware attacks, distributed denial-of-service (DDoS) attacks, and more. Honeynets appear as legitimate networks. However, they may plant vulnerabilities to lure in hackers. They monitor both incoming and outgoing traffic.
Honeypot network setup
The specific setup used to trap hackers using honeypots depends on what you intend to investigate.
Database attack
A government department’s security team could launch honeypots to strengthen its cybersecurity practices. It could set up a fake database that appears to carry the sensitive information of millions of citizens. This sensitive information could contain data like:
- Social Security Numbers (SSNs)
- Full names
- Email addresses
- Home addresses
- Mobile phone numbers
- Places of birth
- Veteran status
- Disability status
- Online passwords.
This is valuable data that hackers would want to get their hands on and sell on the dark web. Researchers would make this database look vulnerable to attract hackers. Once the hackers have been trapped, researchers can closely watch how they approach the database to steal the data.
Insider attack
IT professionals can set up honeypots to catch anyone suspected of overstepping their boundaries in the IT team or trying to launch an insider attack. They can also use honeypots for early detection of insider attacks. It’s a quiet, economical method to identify such attacks.
To close in on the culprit, they can set up a decoy server with the same access controls as the one they suspect is being targeted. The honeypot can be set up on Linux or Windows. This ensures that only authorized individuals can bypass the system. This would be someone from within the organization — specifically, the IT team.
Due to the nature of insider attacks, only key people should be aware that a honeypot is being implemented. Only the investigators and some individuals in management should be notified. An unassuming code name should be used in all communication relating to the honeypot, and the term “honeypot” itself should not be used anywhere.
Given that investigators are looking for inside attackers, they can set up a couple of low-interaction honeypots in the relevant data center locations. The purpose is to merely identify an attempt to attack the system — administrators would report attacks to investigators. It’s best to set up a firewall in such cases to limit connections from the honeypot to external destinations (destinations that aren’t in your network).
Random attacks
An organization may also want to learn about random attacks against its systems in general. In such cases, researchers may be more inclined to set up honeypots that look like servers that are easy to attack. This will make it easier for them to get the information they need about attacks and use it to improve their security systems.
Conclusion
Honeypots can help improve a company’s cybersecurity practices. It is important to remember that a company’s protection is the protection of each and everyone associated with this organization. Don’t forget to use Clario Anti Spy to protect your sensitive information from hackers.


