Table of contents
- What is Pegasus spyware?
- What is the NSO group?
- Who does Pegasus target?
- How does Pegasus get on your phone?
- WhatsApp zero-click exploit
- Apple Messages zero-click exploit
- How to tell if your phone's been infected with Pegasus
- How to protect against Pegasus spyware?
- How Pegasus Differs from Typical Malware
- General recommendations
- Are you protected from Pegasus and other spyware?
What is Pegasus spyware?
Definition
Pegasus is a government-grade spyware tool developed by NSO Group that can secretly access messages, calls, microphones, cameras, and location data on infected smartphones. It is known for using “zero-click” exploits, meaning users may not need to interact with a message or link to become infected.
Pegasus is spyware designed to infiltrate smartphones to monitor activity and steal personal information. While malware of this type isn’t new, Pegasus is a particularly effective breed because it's easy to install, difficult to detect Pegasus spyware, and grants access to all the data on a device. Investigators have linked the spyware, which is primarily associated with mobile phone surveillance, to multiple security breaches, many involving journalists. Some articles refer to a Pegasus spyware scam—phishing messages or fake “security” pages that exploit fear of Pegasus—so treat unexpected links and urgent update prompts with caution.
Recently, research group The Citizen Lab discovered an exploit in multiple operating systems, including iOS, macOS, and watchOS, that could leave a device vulnerable to a Pegasus infection. Fortunately, Apple was quick to patch these issues with security updates. For stronger protection, install patches immediately and review your security settings right after updating.
Pegasus spyware boasts several standout features. The software is:
- Simple to install
- Difficult to detect
- Super effective
- Tough to remove
When it comes to Pegasus, you’re dealing with a high-level piece of spyware, and that’s nothing to scoff at. The program was designed for government use, which means its quality and functionality are as good as they get. If anything feels off, run a spyware scan and keep a brief incident report with timestamps and screenshots.
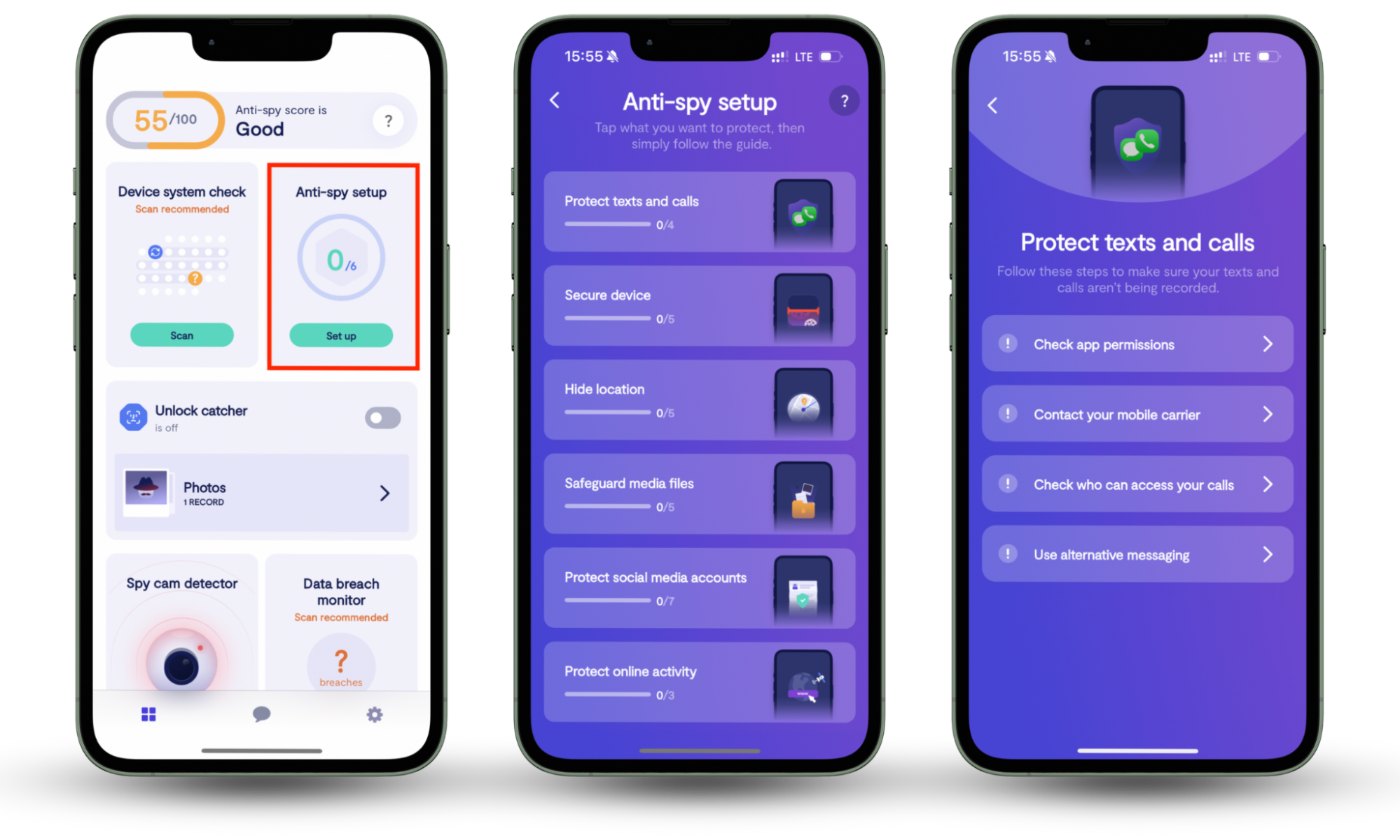
You can protect yourself from Pegasus using dedicated cybersecurity software—and that’s where Clario Anti Spy comes in.
Clario Anti Spy offers a range of features that protect your devices, your personal data, and your privacy. Use Anti-spy setup to safeguard your device against prying eyes, check whether your online accounts are accessible to spies using the Data breach monitor, and get 24/7 assistance when you need anti-spy help.
Here’s how to use Clario Anti Spy’s Anti-spy setup:
- Launch Clario Anti Spy and locate the Anti-spy setup section.
- Press Set up and follow the instructions to make your device as secure as possible against spies.
Note
Pegasus itself is not typically distributed as a public “scam.” However, cybercriminals may impersonate security alerts or government warnings referencing Pegasus to trick users into clicking malicious links.
What is the NSO group?
NSO Group is a cybersecurity firm based in Israel. The company specializes in cyber intelligence and assists governments to mitigate threats and maintain public safety. NSO Group is the firm responsible for producing the Pegasus spyware, the development of which is the organization’s primary claim to fame.
The firm allegedly had a contract with former Panama president Ricardo Martinella. Martinella faced accusations of surveilling his political opponents, and the Pegasus spyware allegedly provided by NSO Group may have been involved in those operations. Evidently, the organization is more than a typical cybersecurity firm. NSO Group possess tools capable of retrieving classified information, influencing elections, and shaping the world.
NSO Group states that its technology is intended for use by authorized government agencies to combat crime and terrorism. However, multiple independent investigations have raised concerns about potential misuse.
Who does Pegasus target?
The Citizen Lab has identified widespread usage that spans continents. An investigation revealed that Pegasus surveillance operations may be taking place in at least 45 countries, including Mexico, United States, United Kingdom, France, and Canada, with some nations having a higher number of infections than others. The spyware has affected a variety of targets, including lawyers, journalists, human rights advocates, and politicians. We can’t be certain how many malicious operators are linked to government intelligence programs and how many are rogue agents.
Therefore, anyone could be a target. You may not be someone worthy of government-sponsored phone hacking, but, traditionally, spyware affects everyone. While most people infected by the Pegasus surveillance software have been high-value targets, once a tool like this is out in the wild, anyone can utilize it for malicious purposes. This software can be used to steal your identity and track your every move.
How does Pegasus get on your phone?
As with any malware, a malicious operator must first get the Pegasus program onto a target device. While someone could install the software physically — using a fake charging cable or by bypassing your passcode — or with a wireless transceiver, the developers at NSO group designed the spyware to be more versatile than that. The ease with which Pegasus can infect a device is alarming. Understanding how Pegasus works is the first step to defending against it.
Pegasus has targeted both iOS and Android devices in documented investigations, with exploit methods tailored to each operating system’s vulnerabilities.
WhatsApp zero-click exploit
A zero-click exploit allows malware to execute code without user interaction. Unlike phishing attacks that require tapping a link, zero-click attacks exploit vulnerabilities in messaging or communication services to process malicious data automatically in the background.
Malicious operators used a WhatsApp exploit to install Pegasus spyware on target devices. The vulnerability is disturbing because, as the name suggests, the infection can occur without you clicking a single thing.
In the case of the WhatsApp hack, operators were able to call a target’s phone and send infected data through to the device even if no one answered. Therefore, through no fault of your own, you could become the victim of a sophisticated spyware attack. WhatsApp has since fixed the vulnerability with a patch released on May 13, 2019.
Apple Messages zero-click exploit
Apple devices were vulnerable to a similar zero-click exploit until a security update patched the issue on September 13, 2021. iOS 14.8, iPadOS 14.8, watchOS 7.6.2, and macOS 11.6 contain the fix so if you haven’t installed the latest updates, now’s a good time to do so.
In the case of the Messages exploit, operators could send an infected PDF through Apple’s built-in messaging app and infect the device with Pegasus spyware. The vulnerability affected multiple Apple operating systems, including iOS and macOS.
While these specific vulnerabilities were patched, researchers continue to investigate new exploit chains. Keeping devices updated remains essential because spyware developers constantly search for new vulnerabilities.
How to tell if your phone's been infected with Pegasus
To identify a compromised phone, you can search for the telltale signs of a mobile malware infection. Pegasus infections often attempt to remain stealthy, but advanced spyware activity may still trigger indirect warning signs, which include:
- Device overheating
- Battery draining quicker than expected
- Device performing poorly
- Inexplicable increase in data usage
These symptoms alone do not confirm a Pegasus infection but may indicate malware or unauthorized background activity requiring investigation.
For a deeper check, Amnesty International has developed the Mobile Verification Toolkit (MVT). This tool helps analyze iOS or Android devices for traces of Pegasus spyware. You can download it directly from the official GitHub page, though it’s designed mainly for forensic researchers rather than casual users.
How to protect against Pegasus spyware?
While Apple and WhatsApp have fixed the two biggest zero-click exploits, you’re still vulnerable to infection through other means. Malicious operators can install malware with physical access to a device, wirelessly, or with infected files sent through email or a web browser. Additionally, more zero-click exploits could exist, and you should do everything in your power to protect yourself from an attack.
Security agencies and cybersecurity bodies such as NIST (National Institute of Standards and Technology) recommend layered defense strategies, including regular patching, access control management, and monitoring for unusual device behavior.
How Pegasus Differs from Typical Malware
While Pegasus is often described as “just another piece of malware,” it operates very differently from the threats most users encounter. Unlike mass-distributed viruses or ransomware campaigns, Pegasus is typically deployed in highly targeted surveillance operations using advanced exploitation techniques. Understanding these differences helps clarify why Pegasus is considered a high-risk, government-grade spyware tool rather than conventional malware.
- Targeting: Pegasus is often deployed against specific individuals; typical malware spreads broadly.
- Installation method: Pegasus may use zero-click exploits; most malware requires user interaction.
- Detection difficulty: Pegasus uses advanced evasion techniques.
- Purpose: Surveillance and intelligence gathering vs financial theft or ransomware.
General recommendations
Prevention is better than the cure, and several tips can help protect you from Pegasus and other malware attacks. These recommendations apply not only to Pegasus but to advanced mobile spyware threats in general:
- Always keep software up to date
- Never open email attachments from unknown sources
- Avoid disreputable websites
- Never click suspicious links
- Block pop-up windows whenever possible
- Avoid jailbreaking devices
- Install security software
The right tools and understanding will put you in a good position to protect yourself and avoid a malware infection. An antivirus solution is a key defense against threats like Pegasus and ransomware. Using the right software can help you stop the threat and delete malicious files.
Are you protected from Pegasus and other spyware?
Malware is always evolving, and keeping up with the latest trends can be a burden. You can, however, make life easier by utilizing the right tools. Use Clario Anti Spy to avoid spyware threats like Pegasus, securing your phone using Anti-spy setup and getting you data breach alerts before it’s too late.


