Table of contents
- What are the most notable examples of computer viruses?
- Morris Worm
- Nimda
- Tinba
- ILOVEYOU
- SQL Slammer
- Stuxnet
- CryptoLocker
- Conficker
- Welchia
- Shlayer
- Protect Yourself From Common Computer Viruses
- Final thought
What are the most notable examples of computer viruses?
With so many types of viruses online and ready to attack, avoiding a computer virus is challenging. While you’re reading this, 970 million pieces of malware are circulating the web, ready to pounce. Even when you’re armored with antivirus software, there is still a chance your system and personal data may be corrupted. But knowing the most destructive and tricky computer viruses in history can help you avoid them.
Hackers don’t need to reinvent the wheel every time and use best practices from their successful counterparts. Below is a list of computer viruses, which features 10 of the most notorious ones.
Morris Worm
Let’s start our journey with Morris Worm, also known as the “Great Worm”. If you look at a “names of computer viruses” list, this is one of those that’ll most likely pop up. It’s believed to be the pioneer among computer worms distributed through the internet. Created to highlight security flaws in Unix systems, its founder — Robert Morris —made a fatal error that transformed the worm from a potentially harmless software to a denial-of-service (DDoS) attack machine.
The worm was supposed to ask whether there was already a copy running on the computer but instead it just continuously made copies of itself, slowing the system down. Finally, it caused crashes and made the computer completely useless.
It’s believed that Morris Worm infected around 6,000 major Unix machines, causing up to $10 million of damage.
Nimda
A worm, a virus, and a Trojan horse all in one sounds like something out of a horror movie. But it’s actually a computer virus called Nimda (admin spelt backwards), which hit the internet in 2001.
Within an hour after its release, Nimda reached the top spot of all reported attacks. No wonder, since the worm used five different transmission routes.
Though its main target is believed to be internet Servers running Windows NT and 2000, Nimda also affected regular users’ PCs running Windows. The latter helped it spread rapidly and caused huge network outages.
Tinba
Tinba is the pet name for the Tiny Banker Trojan that hit the headlines in 2016. As the name suggests, its main target was financial institution websites. Tinba used man-in-the-browser attacks and network sniffing to get users’ banking information. Account numbers, usernames, passwords, credit card numbers, PIN codes; all of these were stolen to later hack into bank accounts. Tinba has infected dozens of banking institutions, including giants such as Wells Fargo, TD Bank, Bank of America, Chase, PNC, and HSBC.
Its success lies in its tiny size (20KB) and ways of spreading. Clicking on a website pop-up, downloading software from an unreliable source, or just opening an infected link could lead to getting infected with Tinba. What’s worse, it hides in your system and stays silent until you open the necessary website.
If you don’t want to fall for a cyberthreat like this, always check if the banking website you’re about to enter has a secure HTTPS connection (all banking websites have to use it) and don’t enter your sensitive information such as social security number or your mom’s maiden name; banks never ask for that.
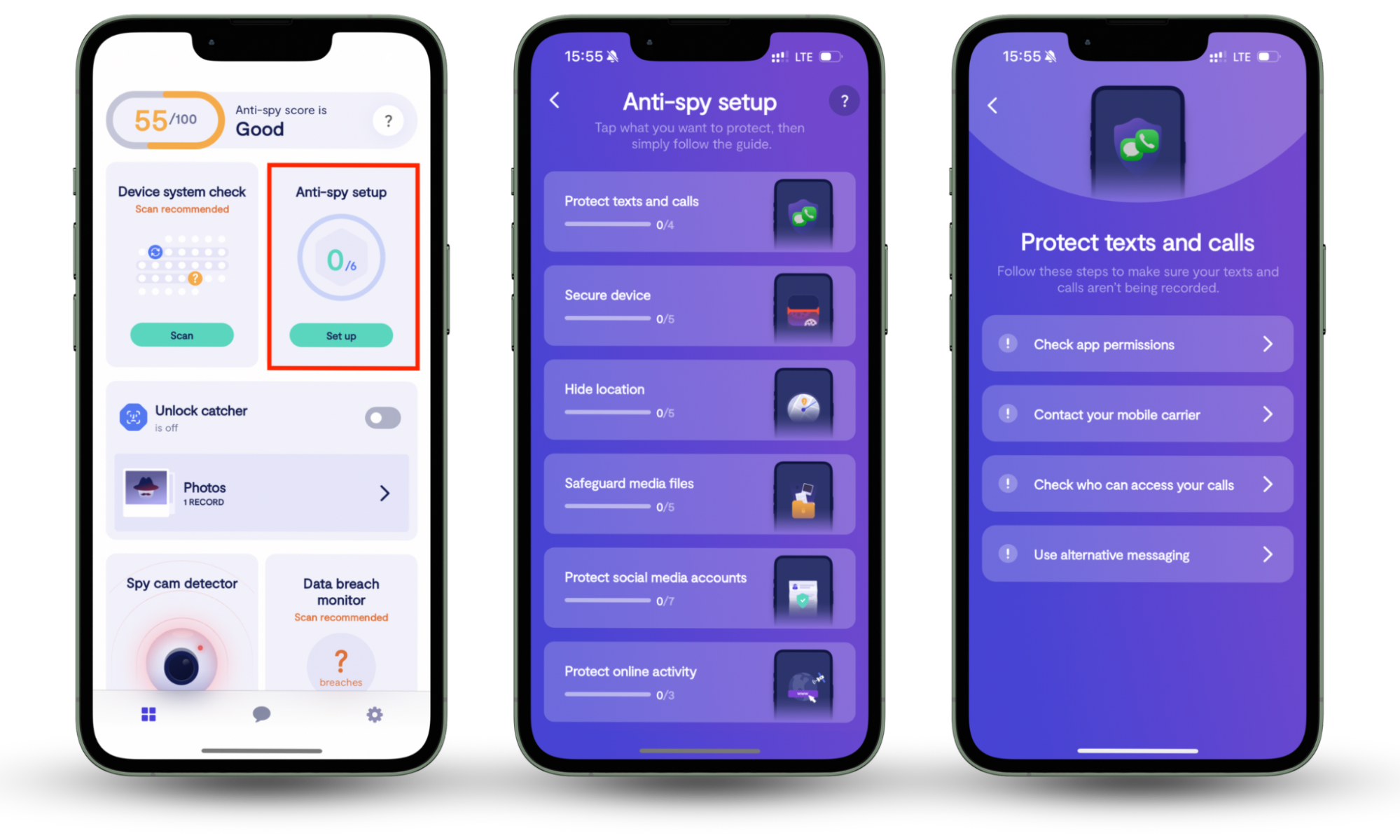
Tinba is very similar to a type of malware known as spyware. This malware infects your devices—including iPhones and Androids—to collect your personal information, track your activities, and even watch you through your camera. To make your phone harder for spyware to infect, use Clario Anti Spy’s Anti-spy setup.
Here’s how to use Clario Anti Spy’s Anti-spy setup on an iPhone or Android:
- Open Clario Anti Spy and log in to your Clario account.
- Under Anti-spy setup, choose Scan. Wait for Clario Anti Spy to check for vulnerabilities that make it easier for spyware to infect your device.
- Follow the instructions to secure your phone.
ILOVEYOU
As romantic as it sounds, the ILOVEYOU virus is not the kind of a gift you’d want to receive on Valentine’s Day. Instead, it’s one of the most famous computer viruses — and it can cause significant damage.
The virus used emails as a transmission channel, disguising itself as a love letter from one of its victim’s contacts. The malware was hidden in the attachment called “LOVE-LETTER-FOR-YOU.TXT.vbs”. Clicking on it activated a Visual Basic script (a programming language which allows programmers to modify code), and the worm started overwriting random files on the user’s PC. The worm also sent copies of itself to all contacts in the user’s address book.
ILOVEYOU infected over 10 million Windows PCs. The sudden rush caused by this “love” bug caused the Pentagon, the British Government, and the CIA to completely shut down their mail systems.
The takeaway: be careful when opening strange attachments in a love letter, even if it comes from your love interest.
SQL Slammer
Outages in 911 service in Seattle, the crash of the Bank of America’s ATM service, and cancellation of several Continental Airlines flights: these are just a few examples of what SQL Slammer (or simply Slammer) is capable of. It sparked at 05:30 UTC on January 25, 2003, infecting its first server.
Once the job was done, Slammer spread rapidly, doubling the number of victims every few seconds, and just 10 minutes after it was released in the wild, the number of infected computers grew to 75,000.
Slammer dramatically slowed down worldwide internet traffic, brought down several important systems, caused a huge panic and more than one billion dollars of damage.
The funny thing is that this cybersecurity breach could have easily been prevented. The worm exploited a bug in Microsoft's SQL Server. The patch preventing it had been released six months before the attack, but many organizations ignored or hadn’t applied it in time.
Stuxnet
The destructive power of computer viruses can make them weapons of mass digital destruction, and Stuxnet became the first one. Unlike any other virus or malware of that time, Stuxnet was developed by the US and Israeli government engineers to disrupt Iran’s nuclear program. Spread via a USB thumb drive, it targeted Siemens industrial control systems, causing centrifuges to mysteriously fail and self-destruct at a record rate.
It’s believed that Stuxnet infected over 200,000 computers and ruined one-fifth of Iran’s nuclear centrifuges. The engineers did a remarkable job. They took great care to hit only designated targets, causing no harm to the computers that didn’t meet the required configurations.
In 2010, the year it appeared, Stuxnet was believed to be the most sophisticated cyberweapon ever deployed. It successfully completed its mission and set back Iran’s progress in building nuclear weapons by a couple of years.
CryptoLocker
CryptoLocker is not like a typical computer virus that causes harm and spreads itself. It’s ransomware: a kind of malware that takes your files hostage, holding them for ransom. CryptoLocker used a trojan disguised as a PDF file that was spread through email attachments.
Surprisingly enough, CryptoLocker caused no harm to the computer itself and didn’t show up until the encryption was done. If you haven’t backed up your files, the only way to restore them was by paying a ransom.
Only 1.3% of all victims paid the ransom. The low rate, however, didn’t prevent hackers behind CryptoLocker from successfully extorting around three million dollars.
Conficker
If there is a flaw in the system, somewhere down the line, it will undoubtedly be exploited. Conficker, Downup, Downadup, Kido — these are all computer virus names that appeared on the internet in 2008. It used the MS08-067 Windows system vulnerability and advanced malware techniques to propagate and install itself into the system. These techniques included copying itself to shared folders and exploiting the AutoRun utility for removable media.
Once a computer was infected, Conficker disabled Windows system’s security services and automatic backup settings, deleted restore points, and made inaccessible security-related websites. Despite its wide distribution and the hassle caused to get rid of it, the worm itself did not cause much damage.
Welchia
As hard as it is to believe, some computer viruses can also be created to serve ethical purposes. Welchia, or the Nachi worm, is one of those.
Welchia was designed to battle and kill the Blaster worm on users’ PCs (if there was one), and prevent further Blaster infection by downloading and installing security patches from Microsoft. Once the job was done, Welchia took itself down.
However, it had a weak spot: the ethical virus slowed computers down. As a result, Welchia caused a nine-hour delay in processing and issuing visas by the US State Department. It also consumed three-quarters of the Navy-Marine Corps’ capacity, rendering it useless for some time.
Shlayer
When it comes to contracting a computer virus, Windows machines are commonly associated. Yet having a Mac doesn’t necessarily mean your chances of getting a virus are zero. The Shlayer trojan proved this; it was responsible for about 30% of all macOS attacks in 2019, making it the number one Mac malware threat that year.
Shlayer disguised itself as updates for Adobe Flash Player (that’s where its name comes from). When launched, it ran a series of shell scripts to proliferate various adware or potentially unwanted applications. In most cases, users got the Shlayer virus when visiting untrustworthy Torrent websites, clicking on the advertisements, or downloading shady files.
But getting Shlayer was just the tip of the iceberg, as it’s only a delivery mechanism. The adware-type applications it installs deliver intrusive advertisements that may lead you to malicious websites and more hidden downloads. In turn, it might result in high-risk system infections and Mac glitches.
Protect Yourself From Common Computer Viruses
Because systems are usually hard to corrupt, most common viruses rely on the weakest link in the chain: the person sitting in front of the screen.
Our advice is rather simple: don’t open strange attachments, ignore shady pop-ups, and think twice before installing software from dubious resources.
Oh, and don’t forget to protect your computer with good antivirus software that will warn you if you go astray.
Final thought
While famous computer viruses capture headlines, lesser-known threats like spyware pose a more significant risk. These invaders silently compromise your privacy on vulnerable devices. To safeguard your information and fortify your defenses against spyware, use Clario Anti Spy. Don't overlook these hidden threats—secure your devices and keep your data confidential.
Read more: